Technology and Internal Security | 1 Year Preparation for UPSC CSE PDF Download
Role of Social Media in National Security
Social media affects many areas of life, including national security. Social media's role in national security has grown with its use. Social media gathers intelligence, spreads information, and monitors risks. It can also spread propaganda, persuade, and recruit criminals.
Benefits Of social media In National Security:
- Intelligence gathering: Intelligence organisations use social media to find persons, networks,patterns, and events that can be used. For instance, internet research.
- Easy engaging with citizens: During riots and violence, law enforcement can reach the most people on social media to calm the situation and correct misinformation.
- Data Mining: Social media metadata such as username, current activities, and locations of suspects can be used by law enforcement agencies to forecast events like flash mobs, and protest violence.
- Indian security forces utilise data mining to detect unlawful border crossings and smuggling using cameras and sensors along the border.
- Policing: social media is an effective tool for policing. It is helping the Police department to speed up the investigation process, connect the public, make people aware of various rules and regulations etc.
- Ease of investigation: With the help of social media profiles of criminals and victims it becomes easy for law enforcement agencies to investigate and gather evidence for various criminal activities.
- Maintaining law and order: social media can help police maintain law and order by gathering public input, tipping on future events, and involving the public in policing.
Challenges/Threat of social media For National Security:
- Cyber terrorism: The biggest threat by social media is cyber terrorism. Terrorist organisations use social media to disturb the law and order of the nation.
- e.g., The Use of social media after the killing of Hizbul commander Burhan Wani to create sympathy for his death which resulted in massive protests in Kashmir valley.
- Spreading terrorism: Terrorist organisations such as ISIS used social media like Facebook and WhatsApp to spread their ideology and brainwash the youth to get success in their agenda of spreading terrorism all over the world.
- Use for Recruiting terrorists: During a Recent NIA investigation it is found that ISIS is using social media platforms like a telegram to recruit youth from Kerala has raised concern over the threat from social media.
- Spreading hatred: For example, the recent incident of the Palghar mob lynching where two people are lynched due to rumours of thieves' activities in the area spread through WhatsApp. Money Laundering: Advertising fake money-making schemes and fraudulent plans on social media to raise money for anti-social activities raises concerns about social media.
- Hacking: Hackers target defence personnel and key people to steal critical infrastructure data that threatens national security. Such as, A Pakistani hacker defaced the NSG website in 2017.
- Difficult to trace: Most social media platforms are owned by foreign companies and run from foreign countries, making it difficult to track the source of misinformation and take action against the perpetrator.
- Revolutions and False propaganda: It has been feared all over the world that social media platforms are used to trigger a violent revolution and protest against the government e.g., the Jasmine revolution in Tunisia.

Fake News
Traditional or digital media outlets spread fake news. Misinformation is often spread to deceive or advance a political or social agenda. With the rise of social media and digital content, fake news has spread worldwide.
Causes:
- Lack of media integrity: Some media outlets on social media and traditional media spread fake news without verifying it, often to increase TRP.
- Political propaganda: In some cases, fake news may be created and spread for political purposes. This can include spreading false information about a political candidate or party to sway public opinion.
- Sensationalism: Fake news is generally sensational hence some media platforms use them to increase their TRP on television and revenue on platforms like YouTube.
- No proper regulation and law: Though the government recently attempted to regulate social media, the biggest source of fake news is still unregulated.
- Lack of awareness: Lack of awareness about how to check the authenticity of sources and lack of digital literacy is making people fall into the trap of this news.
- Confirmation bias: Various studies have found that people generally do not care about finding the truth behind fake news, instead they try to find evidence to defend their biased view strongly.
- Profit motives: Some individuals and organisations may create and spread fake news to make money. This can include creating clickbait headlines or selling advertising space on websites that host fake news stories.
- Increasing use of the Internet: Increasing use of the Internet and social media has increased the intensity of creating and spreading fake news.
- Social media algorithms: Social media algorithms can spread fake news. These algorithms may prioritise popular or controversial content, spreading misinformation quickly.
Challenges:
- Data encryption: WhatsApp uses data encryption to secure end-to-end communication, making it difficult to decrypt messages to check sensitivity and stop fake ones from spreading.
- Difficult to get source: As messages are spread with very high speed and randomly to many people it becomes extremely difficult for law enforcement agencies to track its originator.
- Without boundary: social media is a global platform and there is also a chance that fake news has its source out of the country which makes it nearly impossible for agencies to track it for taking appropriate legal actions.
- Manipulation: Fake news can be used to manipulate public opinion and behaviour. This can have serious consequences, particularly in elections or other democratic processes.
- Legal and ethical challenges: Fake news can raise legal and ethical challenges, particularly around issues of free speech, censorship, and journalistic integrity.
- Security Challenges: Fake news can also pose a security threat, particularly when it is used to spread false information about national security or to incite violence.
- Lack of digital literacy: Maximum social media users are not digitally literate enough to cross-check each message hence the threat of fake news is increasing multifolds.

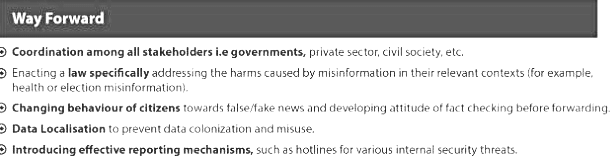
Way Forward
- Media literacy: Developing media literacy skills is essential for individuals to critically evaluate news stories and distinguish between real and fake news.
- Fact-checking: Fact-checking websites and initiatives play a crucial role in verifying the accuracy of news stories and claims.
- Independent news organisations: Independent news organisations are essential for impartial reporting. Independent journalism should be protected from harassment and violence by governments.
- Ethical standards for media organisations: Media organisations should adhere to ethical standards and codes of conduct that prioritise accuracy, fairness, and impartiality in reporting.
- Technology solutions: Technology companies should create fake news detection algorithms and fact-checking labels for social media posts.
- Government regulations: Governments should regulate media and tech companies for spreading fake news. False information spreading organisations are fined and punished.
MOB Violence/Communal Violence and Social Media
- There is a correlation between social media and communal violence as social media can contribute to the spread of rumours, propaganda, and hate speech that can incite violence between different communities.
- In 2018, the NCRB added a new category of "Mob Lynching" to its annual report on crime in India.
- The NCRB report noted that "rumours, fake news and morphed images/videos circulated through social media and messaging apps" were major factors contributing to mob lynching incidents.
Cyber Security
According to the Information Technology Act, of 2000, “Cyber security means protecting information, equipment, devices computer, computer resource, communication device and information stored therein from unauthorized access, use, disclosure, disruption, modification or destruction.”
Types of Cyber Threats

Cyber Crimes
- Financial Frauds: As banking services are shifting towards online platforms, cyber frauds related to banking are also increasing.
- Child Pornography: The internet is being highly used by its abusers to reach and abuse children sexually, worldwide. The explosion of internet usage has made children viable victims of cybercrime.
- Cyber Bullying or Stalking: It occurs when someone engages in offensive, menacing or harassing behaviour using technology. E.g., sending sexually explicit messages or images through a social networking site, email, or text message.
- Copyright Infringement: Online piracy is truly a menace to the cyber world. Online copyright infringement is done not just by people with ill intentions, but also people who are not even aware they are committing a crime.
- Misuse of social media in fanning intolerance, instigating tensions, and inciting riots. Posting inflammatory material that tends to incite hate crimes.
- Identity theft: Identity theft involves stealing someone's name, phone number, address, bank account number, Aadhaar number, credit/debit card number, etc.
- Cyber phishing: fraudulent attempts to steal money and sensitive data like usernames, passwords, and credit card numbers by impersonating a trustworthy entity via electronic communication. Jamtara village in Jharkhand was notorious for cyber phishing.
- Women get trapped to be a victim of cybercrimes and the online podiums are now the new platform where a woman’s privacy, dignity and security are increasingly being challenged every moment.
Cyber Warfare (Fifth Domain of Warfare)
- Cyber warfare involves units which are organised along nation-state boundaries, in offensive and defensive operations, using computers to attack other computers or networks through electronic means.
- E.g., Stuxnet virus was discovered, which was a highly sophisticated cyber-attack on Iran's nuclear program.
- Hackers and other individuals trained in software programming and exploiting the intricacies of computer networks are the primary executors of these attacks.
- According to the Global Cybersecurity Outlook report indicated, 125% of cyber-attacks increase between 2021 and 2022 and this trend goes as well for 2023.
Critical Infrastructure System
- Critical Infrastructure describes the physical and cyber systems and assets that are so vital to a country that their incapacity or destruction would have a debilitating impact on national security and the economic and social welfare of a state.
- The complex interactions among various industrial functions of critical infrastructure and the exchange of information leads to “interdependencies.”
- A minor disruption at one point could have a rippling effect across multiple infrastructures.
- A malware infection in the IT network of the Kudankulam Nuclear Power Plant (KKNPP) located in Tamil Nadu was first reported on social media on October 28, 2019.
Types of Threats to Critical Infrastructure
- Internal Threats: It is ‘one or more individuals with the access and/or inside knowledge of a company, organisation or enterprise that would allow them to exploit the vulnerabilities of that entity's security, systems, services, products or facilities with the intent of causing harm.
- External Threats: This external threat includes crippling CII, espionage, cyber/electronics warfare, cyber terrorism, and foreign government agents.
Importance of Critical Infrastructures
- Essential services: Critical infrastructures provide essential services that are necessary for the functioning of society, such as energy, water, transportation, and communication.
- Public safety and national security: National and public safety depend on critical infrastructure. These infrastructures can disrupt life, property, and the economy.
- Economic Impact: Critical infrastructures are also essential for the functioning of the economy. Disruptions to critical infrastructures can cause economic losses and affect supply chains, leading to further economic impacts.
- Interconnectivity: Critical infrastructures are often interconnected, with disruptions in one infrastructure affecting others.
- Public safety: Critical infrastructure is also essential for maintaining public safety and national security.
- For example, communication infrastructure is critical for emergency response and law enforcement, while energy infrastructure is necessary for maintaining military readiness.
- National security: Critical infrastructures are often targeted by cyber attackers and terrorists, making them vulnerable to sabotage and espionage.
Effects of Cyber-attack on Critical Infrastructure
- Public safety impact: Critical infrastructure cyberattacks can interrupt power, water, and transportation, endangering public safety. Disruptions can lead to huge economic as well as losses of lives.
- Ransomware attack on Maharashtra State Electricity Distribution Company in 2020.
- In 2020, it was reported that a Chinese state-sponsored hacking group had targeted Mumbai's power grid system.
- National security impact: Critical infrastructure cyberattacks can affect national security. State-sponsored hackers and terrorists routinely attack key infrastructures, compromising sensitive data and disrupting crucial systems.
- Social impact: Disruptions to critical infrastructure can lead to social unrest and instability, as people are unable to access essential services and supplies. This can lead to panic, unrest, and civil disorder.
- Psychological impact: Cyberattacks on key infrastructure can affect individuals and communities psychologically.
Rapid fear and uncertainty can cause widespread anxiety and misery.
Factors which Render CIS as Preferred Targets
- Adversary nation: Governments want to conduct persistent and sophisticated cyber operations against communication networks due to global rivalry and geopolitical conflict. Russia's cyberattacks on Georgia and Stuxnet's harm to Iran's nuclear facility.
- Embedded systems: Latest technologies and electronic components are procured via a global supply chain. It can potentially result in tampering, insertion of malicious software etc.
- Insider Threat: It can be in the form of disgruntled/compromised employees, unintentional hiring of a hacker etc. E.g., hacking, and subsequent revelations by Edward Snowden caused global havoc.
- Lack of Training: If an employee is inadequately trained, chances of CII disruption or damage by accident are higher.
- Conceal origin: the technology permits attackers to conceal its origin making it more lucrative for the state and non-state actors.
- No conventional restrictions of being in proximity to start an attack. Cyber-attack can be done from any location to affect systems anywhere in the world.
Steps Taken By Government
- Government has taken several steps to acquire and increase capacity in the field of cybersecurity. They fall under the
- Legal framework, Institutional framework, and other measures.
Information Technology Act 2000 (As Amended in 2008)
- The Information Technology Act, 2000 regulates the use of computer systems and computer networks and their data.
- The Act gives statutory recognition to electronic contracts and deals with electronic authentication, digital signatures, cybercrimes, the liability of network service providers etc.
- Salient Features of the Information Technology Act, 2000:
- Digital signature has been replaced with the electronic signature to make it a more technology-neutral act.
- It elaborates on offences, penalties, and breaches. It outlines the Justice Dispensation Systems for cyber-crimes.
- The Information Technology Act defines in a new section that a cybercafé is any facility from which access to the internet is offered by any person in the ordinary course of business to the members of the public.
Criticisms of the Information Technology Act:
- Inadequate Data Protection: The issues relating to confidential information and data of corporations and their adequate protection have not been adequately addressed.
- Need for a Comprehensive Policy: The issue of spam has not been dealt with comprehensively.
Key Features of the Information Technology (Intermediary Guidelines & Digital Media Ethics Code) Rules, 2021
- Categorization of social media intermediaries: Based on user numbers, the guidelines divide social media intermediaries into two groups.
- Social media intermediaries with more than 5 million users will be designated as Significant Social Media Intermediaries (SSMIs), while those with less will be other intermediaries.
- Appointment of grievance officers: All intermediaries, including SSMIs, are required to appoint a grievance officer who will be responsible for addressing complaints received from users.
- Compliance reports: SSMIs are required to publish a monthly compliance report, which includes details of complaints received and actions taken to address them.
- Removal of unlawful content: Intermediaries are required to remove content that is deemed to be unlawful by a court order or a government agency within 24 hours of receiving a complaint.
- Voluntary verification of user accounts: SSMIs are encouraged to provide users with a voluntary verification mechanism, which will help to identify fake or anonymous accounts.
- Digital media ethics code: The rules also include a digital media ethics code, which applies to digital news organisations, online curated content providers, and news aggregators.
- Traceability of messages: The proposed amendments require social media platforms with more than 5 million users to identify the "first originator" of a message upon government request to investigate and prevent illegal activities.
- Oversight mechanism: The "Self-Regulatory Body of Publishers and Online Curated Content Providers" will ensure online curated content publishers follow the Code of Ethics under the proposed amendments.
- Dispute resolution mechanism: The proposed amendments require social media platforms and publishers of online curated content to establish a grievance redressal mechanism to address user complaints and resolve disputes quickly.
Global Initiatives
- World Economic Forum Cyber Risk Framework: The core principles of the World Economic Forum’s Partnering for Cyber Resilience initiative are -
- Recognition of interdependence: All parties have a shared interest in fostering a common, resilient digital ecosystem.
- Role of leadership: Encourage executive-level awareness and leadership of cyber risk management.
- Budapest Convention: Only this multilateral cyber security treaty addresses Internet and computer crime. It aims to harmonise national laws, improve investigative authorities, and boost international cooperation.
- Internet corporation for assigned names and numbers (ICANN): ICANN coordinates and ensures the smooth and secure functioning of the cybernetic framework.
 |
Download the notes
Technology and Internal Security
|
Download as PDF |
Technology for Law Enforcement
Technology in crime and law enforcement
- Changing nature of crimes: The rise of Information & Communications Technology has changed the nature and modus operandi of crime. E.g. The traditional crimes (robbery, theft etc.) are on decline while crimes like identity theft, financial theft including ransomware, fake news, disinformation, sextortion etc. is on rise.
- Crimes like Drug trafficking have started to operate online, through the dark web.
- Technology adoption for law enforcement: With changed nature and methods of crime, the law enforcement agencies (LEAs) relationship with technology has also changed. These technologies aid in detection and prevention of crime (refer infographic).
Technological initiatives taken by Indian Law Enforcement Agencies (LEAs) and its benefits
- Crime and Criminal Tracking Network & Systems (CCTNS): It creates a national database of crime and criminals and feeds into the Interoperable Criminal Justice System (ICJS) which covers e-courts, e-prisons, forensics, and prosecution for an efficient criminal justice system.
- Technologies of Surveillance and Detection such as biometrics, CCTV, Facial Recognition, Automatic License Plate Recognition (ALPR) etc.
- Digital Forensic Software to investigate and examine IT systems after security incidents or for security related preventive maintenance.
- Crime Mapping and Forecasting, i.e., tracking crime trends geographically by using AI and Big Data that help in detecting crime hotspots and even predict the likelihood of a crime. E.g., This has been done in Delhi.
- Crime Multi Agency Centre (Cri-MAC): Cri-MAC was launched in 2020 by Ministry of Home Affairs (MHA) to share information on crime and criminals 24x7 with various law enforcement agencies.
Barriers in Use of Technology against Crime
- High Cost of technology: procurement and the opportunity cost, especially for developing nations like India.
- India has wide state-wise differences in terms of resources and availability of enabling infrastructure or technologies.
- Technology (Reliability/Effectiveness) Risk, i.e., technology not performing as expected or fulfills the tasks desired of it. E.g.
- Risk of biased outcomes or discrimination as the predictive algorithmic systems are trained on historic crime data. As was observed in USA due to racially biased algorithms.
- Lack of proper data security legislation to avoid data breaches and potential misuse of these technologies.
- Human Associated Risks, i.e., risk of lack of adaptation or efficient use of new technologies due to inadequate training or unwillingness among officials.
- Ethical Concerns such as:
- Violation of privacy by misusing technologies for personal data collection, unlawful surveillance, and possible security breaches.
- Excessive and inappropriate use of technologies in areas where it isn’t warranted.
Facial Recognition Technology
To empower the Indian police with information technology, the Government has approved the implementation of the National Automated Facial Recognition System (NAFRS).
- Facial recognition is a type of technology that uses biometric data and machine learning algorithms to identify or verify the identity of an individual based on their facial features.
National Automated Facial Recognition System (NAFRs)
- NAFRS is to be used by police pan-India and will be issued by the National Crime Records Bureau (NCRB).
- It would be a mobile and web-based application hosted in Delhi to help in crime prevention and detection, and fast- track document verification.
- It is supposed to be interlinked with other existing databases like Crime and Criminal Tracking Network & Systems (CCTNS), Integrated Criminal Justice System (ICJS), State-specific database systems and the Khoya-Paya portal.
|
1090 videos|2974 docs|1354 tests
|




























