|
|
Athira ChoudharyEduRev Computer Science Engineering (CSE) |
|
|
Athira Choudhary
EduRev Computer Science Engineering (CSE)
|
Content, tests & courses saved by you for accessing later. (visible to you only)
Discussed Questions
|
|
Athira Choudhary upvoted • Feb 07, 2025 |
The control unit controls other units by generating ____- a)Control signals
- b)Timing signals
- c)Transfer signals
- d)Command Signals
Correct answer is option 'B'. Can you explain this answer?
The control unit controls other units by generating ____
a)
Control signals
b)
Timing signals
c)
Transfer signals
d)
Command Signals

|
Bijoy Kapoor answered |
- The control unit (CU) is a component of a computer's central processing unit (CPU) that directs the operation of the processor.
- It tells the computer's memory, arithmetic/logic unit and input and output devices how to respond to the instructions that have been sent to the processor.
Hence, the correct answer is Option B
|
|
Athira Choudhary upvoted • Jan 17, 2025 |
Which of the following activation record unit points to non-local data stored in other activation records?- a)Machine status
- b)Access link
- c)Control link
- d)Temporary variables
Correct answer is option 'B'. Can you explain this answer?
Which of the following activation record unit points to non-local data stored in other activation records?
a)
Machine status
b)
Access link
c)
Control link
d)
Temporary variables
|
|
Avantika Yadav answered |
Temporary values: stores the values that arise in the evaluation of an expression.
Machine status: holds the information about the status of a machine just before the function call.
Access link: points to non-local data stored in other activation records.
Control link: points to activation record of a caller.
|
|
Athira Choudhary upvoted • Dec 30, 2024 |
In which of the following no information hiding is done?- a)Compile prig 1, prig 2
- b)Run test, prog
- c)Load R1 , A
- d)001001000010101
Correct answer is option 'D'. Can you explain this answer?
In which of the following no information hiding is done?
a)
Compile prig 1, prig 2
b)
Run test, prog
c)
Load R1 , A
d)
001001000010101
|
|
Shubham Chaudhary answered |
The entire binary symbol gives the information.
|
|
Athira Choudhary upvoted • Oct 21, 2024 |
In reading the columns of a matrix, if no key is pressed we should get all in binary notation- a)0
- b)1
- c)F
- d)7
Correct answer is option 'B'. Can you explain this answer?
In reading the columns of a matrix, if no key is pressed we should get all in binary notation
a)
0
b)
1
c)
F
d)
7
|
|
Shruti Tiwari answered |
If no key is pressed, then all the keys show 1 as they are all connected to power supply.
|
|
Athira Choudhary upvoted • Oct 03, 2024 |
Is following statement true/false? A DFS of a directed graph always produces the same number of tree edges, i.e., independent of the order in which vertices are considered for DFS.- a)True
- b)False
Correct answer is option 'B'. Can you explain this answer?
Is following statement true/false? A DFS of a directed graph always produces the same number of tree edges, i.e., independent of the order in which vertices are considered for DFS.
a)
True
b)
False
|
|
Sanya Agarwal answered |
Consider the following graph. If we start from 'a', then there is one tree edge. If we start from 'b', then there is no tree edge. a→b
Which of the following is the postfix equivalent of (9 - 5) + 2 ?- a)-95 + 2
- b)95 + 2-
- c)95 - 2+
- d)+-952
Correct answer is option 'C'. Can you explain this answer?
Which of the following is the postfix equivalent of (9 - 5) + 2 ?
a)
-95 + 2
b)
95 + 2-
c)
95 - 2+
d)
+-952
|
|
Athira Choudhary answered • Dec 09, 2023 |
The postfix notation, also known as Reverse Polish Notation (RPN), is a mathematical notation in which operators are written after their operands. In postfix notation, the expression (9 - 5) * 2 would be written as "9 5 - 2 *".
To convert the given expression (9 - 5) * 2 to postfix notation, we can follow the following steps:
1. Start with an empty stack and an empty postfix ... more
To convert the given expression (9 - 5) * 2 to postfix notation, we can follow the following steps:
1. Start with an empty stack and an empty postfix ... more
Which of the following statements is false?- a)Virtual memory implements the translation of a program‘s address space into physical memory address space
- b)Virtual memory allows each program to exceed the size of the primary memory
- c)Virtual memory increases the degree of multiprogramming
- d)Virtual memory reduces the context switching overhead
Correct answer is option 'D'. Can you explain this answer?
Which of the following statements is false?
a)
Virtual memory implements the translation of a program‘s address space into physical memory address space
b)
Virtual memory allows each program to exceed the size of the primary memory
c)
Virtual memory increases the degree of multiprogramming
d)
Virtual memory reduces the context switching overhead
|
|
Athira Choudhary answered • Dec 09, 2023 |
Introduction:
Virtual memory is a memory management technique that allows a computer to compensate for the limited physical memory by using a combination of hardware and software to temporarily transfer data between primary memory (RAM) and secondary storage (hard disk). It provides the illusion of a larger memory space than the physical memory available.
Explanation:... more
Virtual memory is a memory management technique that allows a computer to compensate for the limited physical memory by using a combination of hardware and software to temporarily transfer data between primary memory (RAM) and secondary storage (hard disk). It provides the illusion of a larger memory space than the physical memory available.
Explanation:... more
A simple graph (a graph without parallel edge or loops) with n vertices and k components can have at most- a)n edges
- b)n - k edges
- c)( n - k ) ( n - k + 1)
- d)( n - k)(n - k + 1 )/2 edges
Correct answer is option 'A'. Can you explain this answer?
A simple graph (a graph without parallel edge or loops) with n vertices and k components can have at most
a)
n edges
b)
n - k edges
c)
( n - k ) ( n - k + 1)
d)
( n - k)(n - k + 1 )/2 edges
|
|
Athira Choudhary answered • Dec 09, 2023 |
Explanation:
To understand why the correct answer is option A, let's break down the different options and analyze them one by one.
Option A: n edges
- This option states that a simple graph with n vertices and k components can have at most n edges.
- In a simple graph, each edge connects two distinct vertices. So, the maximum number of edges in a graph... more
To understand why the correct answer is option A, let's break down the different options and analyze them one by one.
Option A: n edges
- This option states that a simple graph with n vertices and k components can have at most n edges.
- In a simple graph, each edge connects two distinct vertices. So, the maximum number of edges in a graph... more
The pulses at T0 or T1 pin are counted in- a)timer mode
- b)counter mode
- c)idle mode
- d)power down mode
Correct answer is option 'B'. Can you explain this answer?
The pulses at T0 or T1 pin are counted in
a)
timer mode
b)
counter mode
c)
idle mode
d)
power down mode
|
|
Athira Choudhary answered • Dec 09, 2023 |
Explanation:
In order to understand why the pulses at T0 or T1 pin are counted in counter mode, let's first understand what timer and counter modes are.
Timer Mode:
In timer mode, the microcontroller's timer/counter module is used as a timing device. It can be used to generate time delays, measure the time interval between events, or generate periodic inter... more
In order to understand why the pulses at T0 or T1 pin are counted in counter mode, let's first understand what timer and counter modes are.
Timer Mode:
In timer mode, the microcontroller's timer/counter module is used as a timing device. It can be used to generate time delays, measure the time interval between events, or generate periodic inter... more
If the external interrupt sources control the flags IE0 and IE1, then the interrupt programmed is- a)level-sensitive
- b)edge-sensitive
- c)in serial port
- d)in parallel port
Correct answer is option 'A'. Can you explain this answer?
If the external interrupt sources control the flags IE0 and IE1, then the interrupt programmed is
a)
level-sensitive
b)
edge-sensitive
c)
in serial port
d)
in parallel port
|
|
Athira Choudhary answered • Dec 09, 2023 |
The Explanation:
External interrupts are used to interrupt the normal execution of a program and divert it to a specific routine or function. These interrupts are triggered by external events or signals, such as a button press or a sensor input.
The flags IE0 and IE1 are specific to the external interrupt sources in some microcontrollers or microprocessors. These flag... more
External interrupts are used to interrupt the normal execution of a program and divert it to a specific routine or function. These interrupts are triggered by external events or signals, such as a button press or a sensor input.
The flags IE0 and IE1 are specific to the external interrupt sources in some microcontrollers or microprocessors. These flag... more
The number of bytes stored on the stack during one operation of PUSH or POP is- a)1
- b)2
- c)3
- d)4
Correct answer is option 'A'. Can you explain this answer?
The number of bytes stored on the stack during one operation of PUSH or POP is
a)
1
b)
2
c)
3
d)
4
|
|
Athira Choudhary answered • Dec 09, 2023 |
Explanation:
In computer architecture, the stack is a region of memory used for temporary storage of data. It follows the Last-In-First-Out (LIFO) principle, which means that the last item pushed onto the stack is the first one to be popped off.
When a PUSH operation is performed, a value is added to the top of the stack. This means that the stack pointer is incremented by t... more
In computer architecture, the stack is a region of memory used for temporary storage of data. It follows the Last-In-First-Out (LIFO) principle, which means that the last item pushed onto the stack is the first one to be popped off.
When a PUSH operation is performed, a value is added to the top of the stack. This means that the stack pointer is incremented by t... more
In which of these addressing modes, a constant is specified in the instruction, after the opcode byte?- a)register instructions
- b)register specific instructions
- c)direct addressing
- d)immediate mode
Correct answer is option 'D'. Can you explain this answer?
In which of these addressing modes, a constant is specified in the instruction, after the opcode byte?
a)
register instructions
b)
register specific instructions
c)
direct addressing
d)
immediate mode
|
|
Athira Choudhary answered • Dec 09, 2023 |
Addressing Modes in Computer Architecture
The addressing mode in computer architecture refers to the way in which the operands of an instruction are specified. It determines how the CPU accesses data or operands from memory or registers. One common addressing mode is the immediate mode, which is the focus of this question.
Immediate Mode Addressing... more
The addressing mode in computer architecture refers to the way in which the operands of an instruction are specified. It determines how the CPU accesses data or operands from memory or registers. One common addressing mode is the immediate mode, which is the focus of this question.
Immediate Mode Addressing
The address register for storing the 16-bit addresses can only be- a)stack pointer
- b)data pointer
- c)instruction register
- d)accumulator
Correct answer is option 'B'. Can you explain this answer?
The address register for storing the 16-bit addresses can only be
a)
stack pointer
b)
data pointer
c)
instruction register
d)
accumulator
|
|
Athira Choudhary answered • Dec 09, 2023 |
Address Register
The address register is a hardware component in a computer system that is used to store memory addresses. It is responsible for holding the location of data or instructions in the memory. The size of the address register determines the maximum amount of memory that can be addressed.
16-bit Addresses
In computer systems, memory is typi... more
The address register is a hardware component in a computer system that is used to store memory addresses. It is responsible for holding the location of data or instructions in the memory. The size of the address register determines the maximum amount of memory that can be addressed.
16-bit Addresses
In computer systems, memory is typi... more
The addressing mode, in which the instructions has no source and destination operands is- a)register instructions
- b)register specific instructions
- c)direct addressing
- d)indirect addressing
Correct answer is option 'B'. Can you explain this answer?
The addressing mode, in which the instructions has no source and destination operands is
a)
register instructions
b)
register specific instructions
c)
direct addressing
d)
indirect addressing
|
|
Athira Choudhary answered • Dec 09, 2023 |
The addressing mode, in which the instructions have no source and destination operands, is register specific instructions.
In computer architecture and assembly language programming, addressing modes define how the operands of an instruction are specified. The addressing mode determines where the operands are located and how they are accessed. Different addressing modes have different syntax and semantics.... more
Explanation:
In computer architecture and assembly language programming, addressing modes define how the operands of an instruction are specified. The addressing mode determines where the operands are located and how they are accessed. Different addressing modes have different syntax and semantics.... more
The control transfer instructions are divided into- a)explicit and implicit control transfer instructions
- b)conditional and unconditional control transfer instructions
- c)auto control and self control transfer instructions
- d)all of the mentioned
Correct answer is option 'B'. Can you explain this answer?
The control transfer instructions are divided into
a)
explicit and implicit control transfer instructions
b)
conditional and unconditional control transfer instructions
c)
auto control and self control transfer instructions
d)
all of the mentioned
|
|
Athira Choudhary answered • Dec 09, 2023 |
Explanation:
Control transfer instructions are used in computer programming to alter the flow of control or the sequence of instructions being executed. These instructions allow the program to jump to a different location in the code, enabling the execution of different sections of the program based on certain conditions or criteria.
Control transfer instructions can be cate... more
Control transfer instructions are used in computer programming to alter the flow of control or the sequence of instructions being executed. These instructions allow the program to jump to a different location in the code, enabling the execution of different sections of the program based on certain conditions or criteria.
Control transfer instructions can be cate... more
|
|
Athira Choudhary asked • Jan 20, 2023 |
Assume ∑ = {a} and ε is the empty string: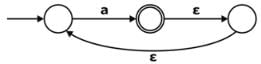
What is the complement of the language accepted by the NFA shown above?- a)∅
- b){ε}
- c)a*
- d){a, ε}
Correct answer is option 'B'. Can you explain this answer?
Assume ∑ = {a} and ε is the empty string:

What is the complement of the language accepted by the NFA shown above?
a)
∅
b)
{ε}
c)
a*
d)
{a, ε}
|
|
Eesha Bhat answered |
The given alphabet contains only one symbol {a} and the given NFA accepts all strings with any number of occurrences of ‘a’. In other words, the NFA accepts {a+}. Therefore complement of the language accepted by automata is an empty string.
The Σ = {a} and the given NFA accepts the strings {a, aa, aaa, aaaa,........} i.e. the language accepted by the NFA can be represented by the regular expression: {a+}
So, the complement of language is {a∗ − a+} = {ε}
Hence, the correct option is (B).
|
|
Athira Choudhary asked • Jul 02, 2021 |
In functional dependency Armstrong inference rules refers to- a)Reflexivity, Augmentation and Decomposition
- b)Transitivity, Augmentation and Reflexivity
- c)Augmentation, Transitivity, Reflexivity and Decomposition
- d)Reflexivity, Transitivity and Decomposition
Correct answer is option 'B'. Can you explain this answer?
In functional dependency Armstrong inference rules refers to
a)
Reflexivity, Augmentation and Decomposition
b)
Transitivity, Augmentation and Reflexivity
c)
Augmentation, Transitivity, Reflexivity and Decomposition
d)
Reflexivity, Transitivity and Decomposition
|
|
Yash Patel answered |
Armstrong inference rules refer to a set of inference rules used to infer all the functional dependencies on a relational database. It consists of the following axioms:
Axiom of Reflexivity:
This axiom states: if Y is a subset of X, then X determines Y
Axiom of Augmentation:
The axiom of augmentation, also known as a partial dependency,
states if X determines Y, then XZ determines YZ, for any Z
Axiom of Transitivity:
The axiom of transitivity says if X determines Y, and Y
determines Z, then X must also determine Z.
Axiom of Reflexivity:
This axiom states: if Y is a subset of X, then X determines Y
Axiom of Augmentation:
The axiom of augmentation, also known as a partial dependency,
states if X determines Y, then XZ determines YZ, for any Z
Axiom of Transitivity:
The axiom of transitivity says if X determines Y, and Y
determines Z, then X must also determine Z.
|
|
Athira Choudhary asked • Jun 16, 2021 |
In a modified merge sort, the input array is splitted at a position one-third of the length(N) of the array. Which of the following is the tightest upper bound on time complexity of this modified Merge Sort.- a)N(logN base 3)
- b)N(logN base 2/3)
- c)N(logN base 1/3)
- d)N(logN base 3/2)
Correct answer is option 'D'. Can you explain this answer?
In a modified merge sort, the input array is splitted at a position one-third of the length(N) of the array. Which of the following is the tightest upper bound on time complexity of this modified Merge Sort.
a)
N(logN base 3)
b)
N(logN base 2/3)
c)
N(logN base 1/3)
d)
N(logN base 3/2)
|
|
Yash Patel answered |
The time complexity is given by: T(N) = T(N/3) + T(2N/3) + N Solving the above recurrence relation gives, T(N) = N(logN base 3/2)
|
|
Athira Choudhary asked • Jun 03, 2021 |
Which of the following is FALSE about SJF (Shortest Job First Scheduling)?
S1: It causes minimum average waiting time
S2: It can cause starvation- a)Only S1
- b)Only S2
- c)Both S1 and S2
- d)Neither S1 nor S2
Correct answer is option 'D'. Can you explain this answer?
Which of the following is FALSE about SJF (Shortest Job First Scheduling)?
S1: It causes minimum average waiting time
S2: It can cause starvation
S1: It causes minimum average waiting time
S2: It can cause starvation
a)
Only S1
b)
Only S2
c)
Both S1 and S2
d)
Neither S1 nor S2
|
|
Sanya Agarwal answered |
- Both SJF and Shortest Remaining time first algorithms may cause starvation. Consider a situation when long process is there in ready queue and shorter processes keep coming.
- SJF is optimal in terms of average waiting time for a given set of processes, but problems with SJF is how to know/predict time of next job.
|
|
Athira Choudhary asked • Jan 04, 2020 |
Consider the following grammar G:
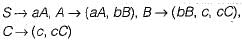
Which of the following is L(G)?- a)L(G) = a*b*c*
- b)L(G) = aa*b*c*
- c)L(G) = aa*bb*cc*
- d)L(G) = (abc)*
Correct answer is option 'C'. Can you explain this answer?
Consider the following grammar G:
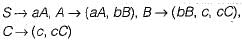
Which of the following is L(G)?
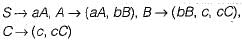
Which of the following is L(G)?
a)
L(G) = a*b*c*
b)
L(G) = aa*b*c*
c)
L(G) = aa*bb*cc*
d)
L(G) = (abc)*
|
|
Saikat Basu answered |
The given grammar is right linear.
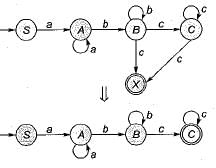
The above FA accepts the language
L(G) = aa* bb* cc*

The above FA accepts the language
L(G) = aa* bb* cc*
|
|
Athira Choudhary asked • Dec 27, 2019 |
If P and Q are predicates and P is the relational algebra expression, then which of the following equivalence are valid?- a)
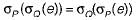
- b)
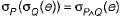
- c)
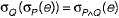
- d)All of these
Correct answer is option 'D'. Can you explain this answer?
If P and Q are predicates and P is the relational algebra expression, then which of the following equivalence are valid?
a)
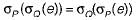
b)
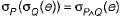
c)
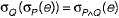
d)
All of these
|
|
Baishali Reddy answered |
All of the given option valid:
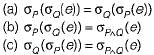
They simply find and selects the tuples which are common to both P and Q.
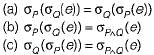
They simply find and selects the tuples which are common to both P and Q.
|
|
Athira Choudhary asked • Dec 18, 2019 |
Two trains from Delhi to Ranchi and from Ranchi to Delhi started at the same time. Due to fog in winter season, after crossing each other, they took 16 hr and 9 hr respectively to complete their journey. If the speed of train going to Ranchi was 45 km/h, what was the speed of train going to Delhi?
- a)60 km/h
- b)50 km/h
- c)65 km/h
- d)75 km/h
Correct answer is option 'A'. Can you explain this answer?
Two trains from Delhi to Ranchi and from Ranchi to Delhi started at the same time. Due to fog in winter season, after crossing each other, they took 16 hr and 9 hr respectively to complete their journey. If the speed of train going to Ranchi was 45 km/h, what was the speed of train going to Delhi?
a)
60 km/h
b)
50 km/h
c)
65 km/h
d)
75 km/h
|
|
Garima Mehta answered |
Let them meet at X after t hours and speed of train 2 be s kmph as shown in figure below
Train 1 is shown above the line and Train 2 is shown below the line
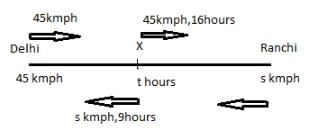
Distance travelled by train 1 before meeting = Distance travelled by train 2 after meeting
45*t = 9*s .... i
Also Distance travelled by train 2 before meeting = Distance travelled by train 1 after meeting
st = 45*16 .... ii
Using eq i ;
t= s/5
Putting in eq ii ;
s^2 / 5 = 45*16
s = 60 kmph
OR
Short trick:
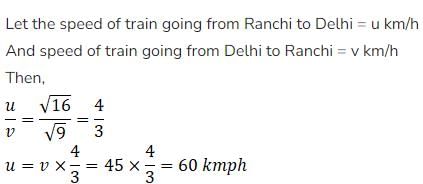
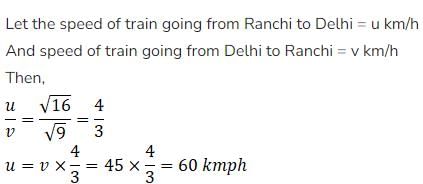
|
|
Athira Choudhary asked • Dec 15, 2019 |
A 5 stage pipelined processor has IF, ID, EXE, MEM and WB. WB stage operation is divided into two parts. In the first part register write operation and in the second part register read operation is performed. The latencies of all those stages are 300, 400, 500, 500 and 300 (in nano second) respectively. Consider the following code is executed on this processor
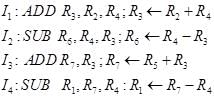
Find minimum number of nop instructions (no operation) to eliminate hazards without using operans forwarding. (Assume each instruction takes one cycle to complete its operation in every stage)
Correct answer is '4'. Can you explain this answer?
A 5 stage pipelined processor has IF, ID, EXE, MEM and WB. WB stage operation is divided into two parts. In the first part register write operation and in the second part register read operation is performed. The latencies of all those stages are 300, 400, 500, 500 and 300 (in nano second) respectively. Consider the following code is executed on this processor
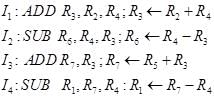
Find minimum number of nop instructions (no operation) to eliminate hazards without using operans forwarding. (Assume each instruction takes one cycle to complete its operation in every stage)
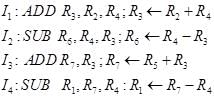
Find minimum number of nop instructions (no operation) to eliminate hazards without using operans forwarding. (Assume each instruction takes one cycle to complete its operation in every stage)
|
|
Rithika Tiwari answered |
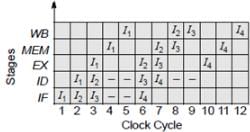
Since I1 and I2 are dependent. So I2 will enter into execute stage when I1completes WB stage.It creates 2 nop. Similarly I3 and I4 are dependent. They create 2 nop.
Total 4 nop instructions are required to eliminate hazards.
|
|
Athira Choudhary asked • Dec 07, 2019 |
During DMA transfer, DMA controller takes over the buses to manage the transfer- a)Directly from CPU to memory
- b)Directly from memory to CPU
- c)Indirectly between the I/O device and memory
- d)Directly between the I/O device and memory
Correct answer is option 'D'. Can you explain this answer?
During DMA transfer, DMA controller takes over the buses to manage the transfer
a)
Directly from CPU to memory
b)
Directly from memory to CPU
c)
Indirectly between the I/O device and memory
d)
Directly between the I/O device and memory
|
|
Ishaan Saini answered |
During DMA transfer, DMA controller takes over the busses to manage the transfer directly from I/O devices to memory or vice-versa.
|
|
Athira Choudhary asked • Nov 25, 2019 |
A counting semaphore was initialized to 0, then 20 V operations were successfully completed on this semaphore, followed with 18 P operations, the resulting value of the semaphore is:- a)18
- b)20
- c)0
- d)2
Correct answer is option 'D'. Can you explain this answer?
A counting semaphore was initialized to 0, then 20 V operations were successfully completed on this semaphore, followed with 18 P operations, the resulting value of the semaphore is:
a)
18
b)
20
c)
0
d)
2
|
|
Kunal Gupta answered |
20V => increments the semaphore 20 times. Hence , the value becomes 20. 18P => decrements the semaphore 18 times. Hence , the value becomes 2.
Fetching relevant content for you























