All questions of Programming & Data Structures for Computer Science Engineering (CSE) Exam
Which of the following correctly declares an array?- a)int geeks[20];
- b)int geeks;
- c)geeks{20};
- d)array geeks[20];
Correct answer is option 'A'. Can you explain this answer?
Which of the following correctly declares an array?
a)
int geeks[20];
b)
int geeks;
c)
geeks{20};
d)
array geeks[20];
|
|
Eesha Bhat answered |
Option A is correct. Int is the data type used,geeks is the name of the array and [20] is the size of the array.
The order of an internal node in a B+ tree index is the maximum number of children it can have. Suppose that a child pointer takes 6 bytes, the search field value takes 14 bytes, and the block size is 512 bytes. What is the order of the internal node?- a)24
- b)25
- c)26
- d)27
Correct answer is option 'C'. Can you explain this answer?
The order of an internal node in a B+ tree index is the maximum number of children it can have. Suppose that a child pointer takes 6 bytes, the search field value takes 14 bytes, and the block size is 512 bytes. What is the order of the internal node?
a)
24
b)
25
c)
26
d)
27
|
|
Palak Shah answered |
To determine the order of the internal node in a B-tree index, we need to consider the following factors:
1. Block size: The block size is given as 512 bytes.
2. Child pointer size: Each child pointer takes 6 bytes.
3. Search field value size: The search field value takes 14 bytes.
We can calculate the order of the internal node by considering the maximum number of children that can fit within a block.
Let's assume the order of the internal node is 'o', and the number of child pointers is 'o-1' (since there is one less child pointer than the order).
To calculate the total space occupied by the child pointers and the search field values, we need to consider the following:
- Each child pointer takes 6 bytes.
- Each search field value takes 14 bytes.
Therefore, the total space occupied by 'o-1' child pointers and 'o-1' search field values is:
Total space = (6 * (o-1)) + (14 * (o-1))
We need to find the maximum order 'o' such that the total space occupied is less than or equal to the block size (512 bytes).
Hence, we have the following equation:
(6 * (o-1)) + (14 * (o-1)) <=>
Simplifying the equation, we get:
20o - 20 <=>
20o <=>
o <=>
Since the order 'o' needs to be an integer, the maximum order is 26.
Therefore, the correct answer is option 'C' (26).
1. Block size: The block size is given as 512 bytes.
2. Child pointer size: Each child pointer takes 6 bytes.
3. Search field value size: The search field value takes 14 bytes.
We can calculate the order of the internal node by considering the maximum number of children that can fit within a block.
Let's assume the order of the internal node is 'o', and the number of child pointers is 'o-1' (since there is one less child pointer than the order).
To calculate the total space occupied by the child pointers and the search field values, we need to consider the following:
- Each child pointer takes 6 bytes.
- Each search field value takes 14 bytes.
Therefore, the total space occupied by 'o-1' child pointers and 'o-1' search field values is:
Total space = (6 * (o-1)) + (14 * (o-1))
We need to find the maximum order 'o' such that the total space occupied is less than or equal to the block size (512 bytes).
Hence, we have the following equation:
(6 * (o-1)) + (14 * (o-1)) <=>
Simplifying the equation, we get:
20o - 20 <=>
20o <=>
o <=>
Since the order 'o' needs to be an integer, the maximum order is 26.
Therefore, the correct answer is option 'C' (26).
Which of the following sorting algorithms can be used to sort a random linked list with minimum time complexity?- a)Insertion Sort
- b)Quick Sort
- c)Heap Sort
- d)Merge Sort
Correct answer is option 'D'. Can you explain this answer?
Which of the following sorting algorithms can be used to sort a random linked list with minimum time complexity?
a)
Insertion Sort
b)
Quick Sort
c)
Heap Sort
d)
Merge Sort
|
|
Rishabh Sharma answered |
Understanding Sorting Algorithms for Linked Lists
When sorting a random linked list, choosing the right algorithm is crucial for achieving optimal time complexity. Here's why Merge Sort is the best option:
1. Time Complexity
- Merge Sort has a time complexity of O(n log n) in the average, worst, and best cases.
- In contrast, other algorithms like Insertion Sort can perform poorly on linked lists, averaging O(n^2).
2. Stability
- Merge Sort is a stable sorting algorithm, meaning it maintains the relative order of equal elements.
- This is particularly beneficial for linked lists, as it preserves the integrity of data.
3. Linked List Compatibility
- Merge Sort works exceptionally well with linked lists since it doesn't require random access to elements.
- The merging process can be efficiently executed by rearranging pointers, avoiding the need for additional space.
4. In-Place Sorting
- Although Merge Sort is not in-place (requiring O(n) additional space), it is still more efficient for linked lists than others like Quick Sort or Heap Sort, which may involve more overhead.
5. Other Algorithms' Limitations
- Insertion Sort: While it can be efficient for nearly sorted lists, it suffers in performance with random data.
- Quick Sort: This algorithm relies on random access, making it less efficient for linked lists.
- Heap Sort: It also requires a random-access structure, leading to potential inefficiencies with linked lists.
In summary, Merge Sort stands out as the optimal choice for sorting a random linked list due to its efficient time complexity, stability, and compatibility with linked structures.
When sorting a random linked list, choosing the right algorithm is crucial for achieving optimal time complexity. Here's why Merge Sort is the best option:
1. Time Complexity
- Merge Sort has a time complexity of O(n log n) in the average, worst, and best cases.
- In contrast, other algorithms like Insertion Sort can perform poorly on linked lists, averaging O(n^2).
2. Stability
- Merge Sort is a stable sorting algorithm, meaning it maintains the relative order of equal elements.
- This is particularly beneficial for linked lists, as it preserves the integrity of data.
3. Linked List Compatibility
- Merge Sort works exceptionally well with linked lists since it doesn't require random access to elements.
- The merging process can be efficiently executed by rearranging pointers, avoiding the need for additional space.
4. In-Place Sorting
- Although Merge Sort is not in-place (requiring O(n) additional space), it is still more efficient for linked lists than others like Quick Sort or Heap Sort, which may involve more overhead.
5. Other Algorithms' Limitations
- Insertion Sort: While it can be efficient for nearly sorted lists, it suffers in performance with random data.
- Quick Sort: This algorithm relies on random access, making it less efficient for linked lists.
- Heap Sort: It also requires a random-access structure, leading to potential inefficiencies with linked lists.
In summary, Merge Sort stands out as the optimal choice for sorting a random linked list due to its efficient time complexity, stability, and compatibility with linked structures.
Which of the following regex states the character set of FORTRAN?- a)[a-z0-9_]
- b)[a-zA-Z0-9]
- c)[A-Z0-9_]
- d)[0-9A-Z_a-z]
Correct answer is option 'D'. Can you explain this answer?
Which of the following regex states the character set of FORTRAN?
a)
[a-z0-9_]
b)
[a-zA-Z0-9]
c)
[A-Z0-9_]
d)
[0-9A-Z_a-z]
|
|
Nilotpal Das answered |
The Correct Answer is Option D - [0-9A-Z_a-z]
Explanation:
1. FORTRAN Character Set:
FORTRAN is a programming language that was developed in the 1950s and is commonly used in scientific and engineering applications. The character set of FORTRAN consists of the following:
- Uppercase letters from A to Z
- Digits from 0 to 9
- Underscore (_)
2. Regular Expressions:
Regular expressions are patterns used to match and manipulate strings. They are used in programming languages, text editors, and other tools to perform operations like searching, matching, and replacing strings.
3. Understanding Regular Expression Options:
Let's analyze the given options for the FORTRAN character set:
a) [a-z0-9_]
- This option matches lowercase letters from a to z, digits from 0 to 9, and underscore (_).
- It does not include uppercase letters.
b) [a-zA-Z0-9]
- This option matches both lowercase and uppercase letters from a to z and digits from 0 to 9.
- However, it does not include the underscore (_).
c) [A-Z0-9_]
- This option matches uppercase letters from A to Z, digits from 0 to 9, and underscore (_).
- It does not include lowercase letters.
d) [0-9A-Z_a-z]
- This option matches digits from 0 to 9, uppercase letters from A to Z, lowercase letters from a to z, and underscore (_).
- It includes all the characters in the FORTRAN character set.
4. Conclusion:
Option D - [0-9A-Z_a-z] is the correct regular expression for the FORTRAN character set because it includes all the required characters: uppercase letters, lowercase letters, digits, and underscore. The other options either miss uppercase letters or the underscore.
Explanation:
1. FORTRAN Character Set:
FORTRAN is a programming language that was developed in the 1950s and is commonly used in scientific and engineering applications. The character set of FORTRAN consists of the following:
- Uppercase letters from A to Z
- Digits from 0 to 9
- Underscore (_)
2. Regular Expressions:
Regular expressions are patterns used to match and manipulate strings. They are used in programming languages, text editors, and other tools to perform operations like searching, matching, and replacing strings.
3. Understanding Regular Expression Options:
Let's analyze the given options for the FORTRAN character set:
a) [a-z0-9_]
- This option matches lowercase letters from a to z, digits from 0 to 9, and underscore (_).
- It does not include uppercase letters.
b) [a-zA-Z0-9]
- This option matches both lowercase and uppercase letters from a to z and digits from 0 to 9.
- However, it does not include the underscore (_).
c) [A-Z0-9_]
- This option matches uppercase letters from A to Z, digits from 0 to 9, and underscore (_).
- It does not include lowercase letters.
d) [0-9A-Z_a-z]
- This option matches digits from 0 to 9, uppercase letters from A to Z, lowercase letters from a to z, and underscore (_).
- It includes all the characters in the FORTRAN character set.
4. Conclusion:
Option D - [0-9A-Z_a-z] is the correct regular expression for the FORTRAN character set because it includes all the required characters: uppercase letters, lowercase letters, digits, and underscore. The other options either miss uppercase letters or the underscore.
Which of the following is FALSE about B/B+ tree- a)B/B+ trees grow upward while Binary Search Trees grow downward.
- b)Time complexity of search operation in B/B+ tree is better than Red Black Trees in general.
- c)Number of child pointers in a B/B+ tree node is always equals to number of keys in it plus one.
- d)A B/B+ tree is defined by a term minimum degree. And minimum degree depends on hard disk block size, key and address sizes.
Correct answer is option 'B'. Can you explain this answer?
Which of the following is FALSE about B/B+ tree
a)
B/B+ trees grow upward while Binary Search Trees grow downward.
b)
Time complexity of search operation in B/B+ tree is better than Red Black Trees in general.
c)
Number of child pointers in a B/B+ tree node is always equals to number of keys in it plus one.
d)
A B/B+ tree is defined by a term minimum degree. And minimum degree depends on hard disk block size, key and address sizes.
|
|
Sudhir Patel answered |
Asymptotic time complexity of both is of order logn.
Suppose a circular queue of capacity (n – 1) elements is implemented with an array of n elements. Assume that the insertion and deletion operation are carried out using REAR and FRONT as array index variables, respectively. Initially, REAR = FRONT = 0. The conditions to detect queue full and queue empty are- a)Full: (REAR+1) mod n == FRONT, empty: REAR == FRONT
- b)Full: (REAR+1) mod n == FRONT, empty: (FRONT+1) mod n == REAR
- c)Full: REAR == FRONT, empty: (REAR+1) mod n == FRONT
- d)Full: (FRONT+1) mod n == REAR, empty: REAR == FRONT
Correct answer is option 'A'. Can you explain this answer?
Suppose a circular queue of capacity (n – 1) elements is implemented with an array of n elements. Assume that the insertion and deletion operation are carried out using REAR and FRONT as array index variables, respectively. Initially, REAR = FRONT = 0. The conditions to detect queue full and queue empty are
a)
Full: (REAR+1) mod n == FRONT, empty: REAR == FRONT
b)
Full: (REAR+1) mod n == FRONT, empty: (FRONT+1) mod n == REAR
c)
Full: REAR == FRONT, empty: (REAR+1) mod n == FRONT
d)
Full: (FRONT+1) mod n == REAR, empty: REAR == FRONT
|
|
Varun Sen answered |
A circular queue is a data structure that follows the FIFO (First In First Out) principle and has a fixed capacity. It is implemented using a circular array, which means that the last element is connected to the first element, forming a circle.
To implement a circular queue of capacity (n), we need to define the following:
1. A circular array of size n to hold the elements of the queue.
2. Two pointers - front and rear, to keep track of the elements in the queue.
3. A variable - count, to keep track of the number of elements in the queue.
Initially, both front and rear pointers are set to -1, indicating an empty queue. Whenever an element is added to the queue, the rear pointer is incremented by 1, and the element is added to the array at the rear index. If the rear pointer exceeds the array size, it is set to 0, indicating that the queue has wrapped around.
Similarly, whenever an element is removed from the queue, the front pointer is incremented by 1, and the element at the front index is removed from the array. If the front pointer exceeds the array size, it is set to 0, indicating that the queue has wrapped around.
To check if the queue is full, we need to compare the count variable with the capacity (n). If count is equal to n, the queue is full. To check if the queue is empty, we need to check if both front and rear pointers are -1. If they are, the queue is empty.
Here is the implementation of a circular queue of capacity (n) in Python:
```
class CircularQueue:
def __init__(self, capacity):
self.capacity = capacity
self.queue = [None] * capacity
self.front = -1
self.rear = -1
self.count = 0
def enqueue(self, item):
if self.is_full():
print("Queue is full")
return
if self.front == -1:
self.front = 0
self.rear = (self.rear + 1) % self.capacity
self.queue[self.rear] = item
self.count += 1
def dequeue(self):
if self.is_empty():
print("Queue is empty")
return
item = self.queue[self.front]
self.queue[self.front] = None
if self.front == self.rear:
self.front = -1
self.rear = -1
else:
self.front = (self.front + 1) % self.capacity
self.count -= 1
return item
def is_full(self):
return self.count == self.capacity
def is_empty(self):
return self.front == -1
def size(self):
return self.count
```
In this implementation, the enqueue() function adds an element to the rear of the queue, and the dequeue() function removes an element from the front of the queue. The is_full() function checks if the queue is full, and the is_empty() function checks if the queue is empty. The size() function returns the number of elements in the queue.
Note that the modulo operator (%) is used to wrap around the rear and front pointers when they exceed the array size. This ensures that the circular queue works correctly even if the front pointer is ahead of the rear pointer in
To implement a circular queue of capacity (n), we need to define the following:
1. A circular array of size n to hold the elements of the queue.
2. Two pointers - front and rear, to keep track of the elements in the queue.
3. A variable - count, to keep track of the number of elements in the queue.
Initially, both front and rear pointers are set to -1, indicating an empty queue. Whenever an element is added to the queue, the rear pointer is incremented by 1, and the element is added to the array at the rear index. If the rear pointer exceeds the array size, it is set to 0, indicating that the queue has wrapped around.
Similarly, whenever an element is removed from the queue, the front pointer is incremented by 1, and the element at the front index is removed from the array. If the front pointer exceeds the array size, it is set to 0, indicating that the queue has wrapped around.
To check if the queue is full, we need to compare the count variable with the capacity (n). If count is equal to n, the queue is full. To check if the queue is empty, we need to check if both front and rear pointers are -1. If they are, the queue is empty.
Here is the implementation of a circular queue of capacity (n) in Python:
```
class CircularQueue:
def __init__(self, capacity):
self.capacity = capacity
self.queue = [None] * capacity
self.front = -1
self.rear = -1
self.count = 0
def enqueue(self, item):
if self.is_full():
print("Queue is full")
return
if self.front == -1:
self.front = 0
self.rear = (self.rear + 1) % self.capacity
self.queue[self.rear] = item
self.count += 1
def dequeue(self):
if self.is_empty():
print("Queue is empty")
return
item = self.queue[self.front]
self.queue[self.front] = None
if self.front == self.rear:
self.front = -1
self.rear = -1
else:
self.front = (self.front + 1) % self.capacity
self.count -= 1
return item
def is_full(self):
return self.count == self.capacity
def is_empty(self):
return self.front == -1
def size(self):
return self.count
```
In this implementation, the enqueue() function adds an element to the rear of the queue, and the dequeue() function removes an element from the front of the queue. The is_full() function checks if the queue is full, and the is_empty() function checks if the queue is empty. The size() function returns the number of elements in the queue.
Note that the modulo operator (%) is used to wrap around the rear and front pointers when they exceed the array size. This ensures that the circular queue works correctly even if the front pointer is ahead of the rear pointer in
Suppose the numbers 7, 5, 1, 8, 3, 6, 0, 9, 4, 2 are inserted in that order into an initially empty binary search tree. The binary search tree uses the usual ordering on natural numbers. What is the in-order traversal sequence of the resultant tree?- a)7 5 1 0 3 2 4 6 8 9
- b)0 2 4 3 1 6 5 9 8 7
- c)0 1 2 3 4 5 6 7 8 9
- d)9 8 6 4 2 3 0 1 5 7
Correct answer is option 'C'. Can you explain this answer?
Suppose the numbers 7, 5, 1, 8, 3, 6, 0, 9, 4, 2 are inserted in that order into an initially empty binary search tree. The binary search tree uses the usual ordering on natural numbers. What is the in-order traversal sequence of the resultant tree?
a)
7 5 1 0 3 2 4 6 8 9
b)
0 2 4 3 1 6 5 9 8 7
c)
0 1 2 3 4 5 6 7 8 9
d)
9 8 6 4 2 3 0 1 5 7
|
|
Sudhir Patel answered |
In-order traversal of a BST gives elements in increasing order. So answer c is correct without any doubt.
Let A be a square matrix of size n x n. Consider the following program. What is the expected output?C = 100for i = 1 to n do for j = 1 to n do { Temp = A[i][j] + C A[i][j] = A[j][i] A[j][i] = Temp - C } for i = 1 to n do for j = 1 to n do Output(A[i][j]);- a)The matrix A itself
- b)Transpose of matrix A
- c)Adding 100 to the upper diagonal elements and subtracting 100 from diagonal elements of A
- d)None of the above
Correct answer is option 'A'. Can you explain this answer?
Let A be a square matrix of size n x n. Consider the following program. What is the expected output?
C = 100
for i = 1 to n do
for j = 1 to n do
{
Temp = A[i][j] + C
A[i][j] = A[j][i]
A[j][i] = Temp - C
}
for i = 1 to n do
for j = 1 to n do
Output(A[i][j]);
a)
The matrix A itself
b)
Transpose of matrix A
c)
Adding 100 to the upper diagonal elements and subtracting 100 from diagonal elements of A
d)
None of the above
|
|
Sudhir Patel answered |
If we take look at the inner statements of first loops, we can notice that the statements swap A[i][j] and A[j][i] for all i and j. Since the loop runs for all elements, every element A[l][m] would be swapped twice, once for i = l and j = m and then for i = m and j = l. Swapping twice means the matrix doesn’t change.
What is the use of 'javac' command?- a)Execute a java program
- b)Debug a java program
- c)Interpret a java program
- d)Compile a java program
Correct answer is option 'D'. Can you explain this answer?
What is the use of 'javac' command?
a)
Execute a java program
b)
Debug a java program
c)
Interpret a java program
d)
Compile a java program
|
|
Eesha Bhat answered |
Concept
The javac command in Java compiles a program from a command prompt.
It reads a Java source program from a text file and creates a compiled Java class file.
Syntax
javac filename [options]
For example, to compile a program named Abc.java, use this command:
javac Abc.java
Which of the following is true about linked list implementation of stack?- a)In push operation, if new nodes are inserted at the beginning of linked list, then in pop operation, nodes must be removed from end.
- b)In push operation, if new nodes are inserted at the end, then in pop operation, nodes must be removed from the beginning.
- c)Both of the above
- d)None of the above
Correct answer is option 'D'. Can you explain this answer?
Which of the following is true about linked list implementation of stack?
a)
In push operation, if new nodes are inserted at the beginning of linked list, then in pop operation, nodes must be removed from end.
b)
In push operation, if new nodes are inserted at the end, then in pop operation, nodes must be removed from the beginning.
c)
Both of the above
d)
None of the above
|
|
Dipika Chavan answered |
Linked List Implementation of Stack
- Stack is a data structure in which elements are inserted and removed from the same end, called the top of the stack.
- Linked list is a dynamic data structure in which each element is a separate object, called a node, that contains a value and a reference to the next node.
- Linked list implementation of stack involves creating a linked list where the top of the stack is represented by the head node of the linked list.
Push Operation
- In push operation, a new node is inserted at the beginning of the linked list.
- This is because the top of the stack is always the first node of the linked list.
- The steps involved in push operation are:
1. Create a new node with the given value.
2. Set the next pointer of the new node to the current head of the linked list.
3. Set the head of the linked list to the new node.
Pop Operation
- In pop operation, the top node of the linked list is removed.
- This is because the top of the stack is always the first node of the linked list.
- The steps involved in pop operation are:
1. Check if the linked list is empty. If it is, return an error.
2. Store the value of the head node in a variable.
3. Set the head of the linked list to the next node.
4. Delete the previous head node.
5. Return the stored value.
Answer
- Neither option (a) nor option (b) is true for linked list implementation of stack.
- In linked list implementation of stack, new nodes are inserted at the beginning of the linked list in push operation and the top node of the linked list is removed in pop operation.
- Stack is a data structure in which elements are inserted and removed from the same end, called the top of the stack.
- Linked list is a dynamic data structure in which each element is a separate object, called a node, that contains a value and a reference to the next node.
- Linked list implementation of stack involves creating a linked list where the top of the stack is represented by the head node of the linked list.
Push Operation
- In push operation, a new node is inserted at the beginning of the linked list.
- This is because the top of the stack is always the first node of the linked list.
- The steps involved in push operation are:
1. Create a new node with the given value.
2. Set the next pointer of the new node to the current head of the linked list.
3. Set the head of the linked list to the new node.
Pop Operation
- In pop operation, the top node of the linked list is removed.
- This is because the top of the stack is always the first node of the linked list.
- The steps involved in pop operation are:
1. Check if the linked list is empty. If it is, return an error.
2. Store the value of the head node in a variable.
3. Set the head of the linked list to the next node.
4. Delete the previous head node.
5. Return the stored value.
Answer
- Neither option (a) nor option (b) is true for linked list implementation of stack.
- In linked list implementation of stack, new nodes are inserted at the beginning of the linked list in push operation and the top node of the linked list is removed in pop operation.
Let P be a singly linked list. Let Q be the pointer to an intermediate node x in the list. What is the worst-case time complexity of the best known algorithm to delete the node x from the list?- a)0(n)
- b)0(log2 n)
- c)0(logn)
- d)0(1)
Correct answer is option 'D'. Can you explain this answer?
Let P be a singly linked list. Let Q be the pointer to an intermediate node x in the list. What is the worst-case time complexity of the best known algorithm to delete the node x from the list?
a)
0(n)
b)
0(log2 n)
c)
0(logn)
d)
0(1)
|
|
Aarav Malik answered |
Worst-case Time Complexity of Deleting a Node x from a Singly Linked List
To understand the worst-case time complexity of deleting a node x from a singly linked list, let's analyze the steps involved in the process.
Traversing to the Node x
1. Initially, we have a pointer Q pointing to the node x in the list.
2. To delete node x, we need to find its previous node (let's call it prev).
3. We can traverse the linked list starting from the head until we find the node whose next node is x.
4. This traversal requires iterating through all the nodes until we reach the node x or the end of the list.
Deleting the Node x
1. Once we have the previous node (prev) of x, we can update the next pointer of prev to skip the node x.
2. This operation involves changing the next pointer of prev to point to the node after x.
3. We also need to free the memory occupied by the node x.
Worst-case Time Complexity
The worst-case time complexity of the best known algorithm to delete the node x from a singly linked list is O(1).
- Traversing to the Node x: The time complexity of this step is O(n) in the worst case, as we may need to traverse the entire linked list to reach the node x.
- Deleting the Node x: Once we have the previous node (prev) of x, deleting the node x and updating the pointers can be done in constant time, regardless of the size of the linked list.
Since the second step (deleting the node x) can be done in constant time, it dominates the time complexity. Therefore, the overall worst-case time complexity is O(1).
Conclusion
The best known algorithm to delete a node x from a singly linked list has a worst-case time complexity of O(1). This means that the time taken to delete the node x is constant and does not depend on the size of the linked list.
To understand the worst-case time complexity of deleting a node x from a singly linked list, let's analyze the steps involved in the process.
Traversing to the Node x
1. Initially, we have a pointer Q pointing to the node x in the list.
2. To delete node x, we need to find its previous node (let's call it prev).
3. We can traverse the linked list starting from the head until we find the node whose next node is x.
4. This traversal requires iterating through all the nodes until we reach the node x or the end of the list.
Deleting the Node x
1. Once we have the previous node (prev) of x, we can update the next pointer of prev to skip the node x.
2. This operation involves changing the next pointer of prev to point to the node after x.
3. We also need to free the memory occupied by the node x.
Worst-case Time Complexity
The worst-case time complexity of the best known algorithm to delete the node x from a singly linked list is O(1).
- Traversing to the Node x: The time complexity of this step is O(n) in the worst case, as we may need to traverse the entire linked list to reach the node x.
- Deleting the Node x: Once we have the previous node (prev) of x, deleting the node x and updating the pointers can be done in constant time, regardless of the size of the linked list.
Since the second step (deleting the node x) can be done in constant time, it dominates the time complexity. Therefore, the overall worst-case time complexity is O(1).
Conclusion
The best known algorithm to delete a node x from a singly linked list has a worst-case time complexity of O(1). This means that the time taken to delete the node x is constant and does not depend on the size of the linked list.
In the worst case, the number of comparisons needed to search a singly linked list of length n for a given element is- a)log 2 n
- b)n/2
- c)log 2 n – 1
- d)n
Correct answer is option 'D'. Can you explain this answer?
In the worst case, the number of comparisons needed to search a singly linked list of length n for a given element is
a)
log 2 n
b)
n/2
c)
log 2 n – 1
d)
n
|
|
Subhankar Chawla answered |
The worst case scenario for searching a singly linked list of length n is when the desired element is not present in the list. In this case, we have to traverse the entire list and compare each element until we reach the end. Therefore, the number of comparisons needed in the worst case is equal to the length of the list, which is n.
So the correct answer is b) n/2.
So the correct answer is b) n/2.
The five items: A, B, C, D, and E are pushed in a stack, one after other starting from A. The stack is popped four items and each element is inserted in a queue. The two elements are deleted from the queue and pushed back on the stack. Now one item is popped from the stack. The popped item is- a)A
- b)B
- c)C
- d)D
Correct answer is option 'D'. Can you explain this answer?
The five items: A, B, C, D, and E are pushed in a stack, one after other starting from A. The stack is popped four items and each element is inserted in a queue. The two elements are deleted from the queue and pushed back on the stack. Now one item is popped from the stack. The popped item is
a)
A
b)
B
c)
C
d)
D
|
|
Sudhir Patel answered |
When five items: A, B, C, D, and E are pushed in a stack: Order of stack becomes: A, B, C, D, and E (A at the bottom and E at the top.) stack is popped four items and each element is inserted in a queue: Order of queue: B, C, D, E (B at rear and E at the front) Order of stack after pop operations = A Two elements deleted from the queue and pushed back on the stack: New order of stack = A, E, D(A at the bottom, D at the top) As D is on the top so when pop operation occurs D will be popped out.
So, correct option is (D).
So, correct option is (D).
Consider the following conditions:
(a)The solution must be feasible, i.e. it must satisfy all the supply and demand constraints.
(b)The number of positive allocations must be equal to m1n21, where m is the number of rows and n is the number of columns.
(c) All the positive allocations must be in independent positions.
The initial solution of a transportation problem is said to be non-degenerate basic feasible solution if it satisfies:
Codes:- a)(a) and (b) only
- b)(a) and (c) only
- c)(b) and (c) only
- d)(a), (b) and (c)
Correct answer is option 'D'. Can you explain this answer?
Consider the following conditions:
(a)The solution must be feasible, i.e. it must satisfy all the supply and demand constraints.
(b)The number of positive allocations must be equal to m1n21, where m is the number of rows and n is the number of columns.
(c) All the positive allocations must be in independent positions.
The initial solution of a transportation problem is said to be non-degenerate basic feasible solution if it satisfies:
Codes:
(a)The solution must be feasible, i.e. it must satisfy all the supply and demand constraints.
(b)The number of positive allocations must be equal to m1n21, where m is the number of rows and n is the number of columns.
(c) All the positive allocations must be in independent positions.
The initial solution of a transportation problem is said to be non-degenerate basic feasible solution if it satisfies:
Codes:
a)
(a) and (b) only
b)
(a) and (c) only
c)
(b) and (c) only
d)
(a), (b) and (c)
|
|
Ashwini Ghoshal answered |
Non-Degenerate Basic Feasible Solution in Transportation Problem
Conditions for a Feasible Solution:
- A feasible solution must satisfy all the supply and demand constraints.
Conditions for Positive Allocations:
- The number of positive allocations must be equal to m*n.
- All the positive allocations must be in independent positions.
Non-Degenerate Basic Feasible Solution:
- A non-degenerate basic feasible solution satisfies all the conditions for a feasible solution and positive allocations.
- In addition, it must also meet the following conditions:
- The number of positive allocations must be equal to m*n and the number of basic variables must be equal to m+n-1.
- The basic variables must be independent, i.e. no two basic variables can come from the same row or column.
- The non-basic variables must be zero.
- Non-degenerate basic feasible solutions are preferred over degenerate basic feasible solutions as they help in finding the optimal solution faster.
Conditions for a Feasible Solution:
- A feasible solution must satisfy all the supply and demand constraints.
Conditions for Positive Allocations:
- The number of positive allocations must be equal to m*n.
- All the positive allocations must be in independent positions.
Non-Degenerate Basic Feasible Solution:
- A non-degenerate basic feasible solution satisfies all the conditions for a feasible solution and positive allocations.
- In addition, it must also meet the following conditions:
- The number of positive allocations must be equal to m*n and the number of basic variables must be equal to m+n-1.
- The basic variables must be independent, i.e. no two basic variables can come from the same row or column.
- The non-basic variables must be zero.
- Non-degenerate basic feasible solutions are preferred over degenerate basic feasible solutions as they help in finding the optimal solution faster.
Given a hash table T with 25 slots that stores 2000 elements, the load factor α for T is __________- a)80
- b)0.0125
- c)8000
- d)1.25
Correct answer is option 'A'. Can you explain this answer?
Given a hash table T with 25 slots that stores 2000 elements, the load factor α for T is __________
a)
80
b)
0.0125
c)
8000
d)
1.25
|
|
Gitanjali Singh answered |
Can be calculated by dividing the number of elements stored in the hash table by the total number of slots.
In this case, the load factor would be 2000 / 25 = 80.
This means that, on average, each slot in the hash table is storing 80 elements.
In this case, the load factor would be 2000 / 25 = 80.
This means that, on average, each slot in the hash table is storing 80 elements.
Consider the following C declarationstruct {short s[5];union {float y;long z;}u;}t;Assume that objects of type short, float and long occupy 2 bytes, 4 bytes and 8 bytes, respectively. The memory requirement for variable t, ignoring alignment considerations, is- a)22 bytes
- b)18 bytes
- c)14 bytes
- d)10 bytes
Correct answer is option 'B'. Can you explain this answer?
Consider the following C declaration
struct {
short s[5];
union {
float y;
long z;
}u;
}t;
Assume that objects of type short, float and long occupy 2 bytes, 4 bytes and 8 bytes, respectively. The memory requirement for variable t, ignoring alignment considerations, is
a)
22 bytes
b)
18 bytes
c)
14 bytes
d)
10 bytes
|
|
Akshara Dasgupta answered |
Understanding the Structure Size
To determine the memory requirement for the variable `t`, we need to analyze the components of the structure and union it contains.
Components of the Structure
- Array of Short:
- The structure contains an array `s` of 5 `short` integers.
- Each `short` occupies 2 bytes.
- Total memory for the array:
5 * 2 bytes = 10 bytes
- Union:
- The union `u` can hold either a `float` or a `long`.
- A `float` occupies 4 bytes.
- A `long` occupies 8 bytes.
- The size of the union is determined by the larger of its members:
Max(4 bytes, 8 bytes) = 8 bytes
Calculating Total Memory
- Total size of the structure `t`:
Size of `s` (10 bytes) + Size of `u` (8 bytes) = 10 bytes + 8 bytes = 18 bytes
Conclusion
Thus, the total memory requirement for the variable `t`, ignoring alignment considerations, is 18 bytes. Therefore, the correct answer is option B.
To determine the memory requirement for the variable `t`, we need to analyze the components of the structure and union it contains.
Components of the Structure
- Array of Short:
- The structure contains an array `s` of 5 `short` integers.
- Each `short` occupies 2 bytes.
- Total memory for the array:
5 * 2 bytes = 10 bytes
- Union:
- The union `u` can hold either a `float` or a `long`.
- A `float` occupies 4 bytes.
- A `long` occupies 8 bytes.
- The size of the union is determined by the larger of its members:
Max(4 bytes, 8 bytes) = 8 bytes
Calculating Total Memory
- Total size of the structure `t`:
Size of `s` (10 bytes) + Size of `u` (8 bytes) = 10 bytes + 8 bytes = 18 bytes
Conclusion
Thus, the total memory requirement for the variable `t`, ignoring alignment considerations, is 18 bytes. Therefore, the correct answer is option B.
Which of the following is not a computer language?I. C++II. JavaIII. Linux- a)Only I
- b)Only III
- c)II and III
- d)I and II
Correct answer is option 'B'. Can you explain this answer?
Which of the following is not a computer language?
I. C++
II. Java
III. Linux
a)
Only I
b)
Only III
c)
II and III
d)
I and II
|
|
Eesha Bhat answered |
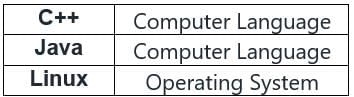
Additional Information
- Computer Language - A programming language is a vocabulary and set of grammatical rules for instructing a computer or computing device to perform specific tasks.
- Operating System - is system software that manages computer hardware and software resources and provides common services for other computer programs.
An advantage of chained hash table (external hashing) over the open addressing scheme is- a)Worst case complexity of search operations is less
- b)Space used is less
- c)Deletion is easier
- d)None of the above
Correct answer is option 'C'. Can you explain this answer?
An advantage of chained hash table (external hashing) over the open addressing scheme is
a)
Worst case complexity of search operations is less
b)
Space used is less
c)
Deletion is easier
d)
None of the above
|
|
Eesha Bhat answered |
In Open Addressing scheme sometimes though element is present we can't delete it if empty bucket comes in between while searching for that element. External hashing scheme is free from this limitations. Hence, Option c is correct answer.
Which programming language is called the mother of programming languages?- a)C++
- b)C
- c)Java
- d)COBOL
Correct answer is option 'B'. Can you explain this answer?
Which programming language is called the mother of programming languages?
a)
C++
b)
C
c)
Java
d)
COBOL
|
|
Sudhir Patel answered |
- The C language is also known as the mother of all programming languages.
- C is a general-purpose programming language that is used for creating a variety of applications.
- C language was originally developed for writing operating systems. Unix Kernel and all of its supporting tools and libraries are written in C language.
- The C language is used for the following operations :
- Operating systems
- Development of new languages
- Computation platforms
- Embedded systems
- Graphics and Games
- C++ and Java are the high-level languages and COBOL is a compiled English-like computer programming language.
Which file sets the Unix environment for the user when the user logs into his HOME directory?- a).exrc
- b).profile
- c).lastlogin
- d).mbox
Correct answer is option 'B'. Can you explain this answer?
Which file sets the Unix environment for the user when the user logs into his HOME directory?
a)
.exrc
b)
.profile
c)
.lastlogin
d)
.mbox
|
|
Sudhir Patel answered |
.exrc: It reads the file and applies the settings in the file being opened.
.profile: It contains your individual profile that overrides the variables set in the /etc/profile file, hence, setting the environment for the user.
.lastlogin: There is no such file.
.mbox: It contains the family of related file formats used for holding collections of email messages.
Chapter doubts & questions for Programming & Data Structures - GATE Computer Science Engineering(CSE) 2026 Mock Test Series 2025 is part of Computer Science Engineering (CSE) exam preparation. The chapters have been prepared according to the Computer Science Engineering (CSE) exam syllabus. The Chapter doubts & questions, notes, tests & MCQs are made for Computer Science Engineering (CSE) 2025 Exam. Find important definitions, questions, notes, meanings, examples, exercises, MCQs and online tests here.
Chapter doubts & questions of Programming & Data Structures - GATE Computer Science Engineering(CSE) 2026 Mock Test Series in English & Hindi are available as part of Computer Science Engineering (CSE) exam.
Download more important topics, notes, lectures and mock test series for Computer Science Engineering (CSE) Exam by signing up for free.

Contact Support
Our team is online on weekdays between 10 AM - 7 PM
Typical reply within 3 hours
|
Free Exam Preparation
at your Fingertips!
Access Free Study Material - Test Series, Structured Courses, Free Videos & Study Notes and Prepare for Your Exam With Ease

 Join the 10M+ students on EduRev
Join the 10M+ students on EduRev
|

|
Create your account for free
OR
Forgot Password
OR
Signup to see your scores
go up within 7 days!
Access 1000+ FREE Docs, Videos and Tests
Takes less than 10 seconds to signup









