|
|
Raksha MishraEduRev Computer Science Engineering (CSE) |
|
|
Raksha Mishra
EduRev Computer Science Engineering (CSE)
|
Content, tests & courses saved by you for accessing later. (visible to you only)
Discussed Questions
|
|
Raksha Mishra upvoted • Feb 04, 2025 |
You have two bags of colored marbles. Bag A contains 3 red marbles and 2 green marbles, while Bag B contains 4 red marbles and 1 green marble. You choose one of the bags at random and then select a marble from that bag. What is the probability that you selected Bag A, given that you picked a red marble?
- a)3/5
- b)2/5
- c)4/7
- d)3/7
Correct answer is option 'D'. Can you explain this answer?
You have two bags of colored marbles. Bag A contains 3 red marbles and 2 green marbles, while Bag B contains 4 red marbles and 1 green marble. You choose one of the bags at random and then select a marble from that bag. What is the probability that you selected Bag A, given that you picked a red marble?
a)
3/5
b)
2/5
c)
4/7
d)
3/7

|
Engineers Adda answered |
Let's use conditional probability here. We want to find the probability of selecting Bag A given that a red marble was chosen.
P(A) is the probability of choosing Bag A, and P(R) is the probability of choosing a red marble.
We know that P(A) is 1/2 because we choose a bag at random, and there are two bags.
P(R|A) is the probability of choosing a red marble from Bag A, which is 3/5.
P(R|B) is the probability of choosing a red marble from Bag B, which is 4/5.
Now, we can use Bayes' theorem to find P(A|R), the probability of choosing Bag A given a red marble was picked:
P(A|R) = [P(R|A) * P(A)] / [P(R|A) * P(A) + P(R|B) * P(B)]
P(A|R) = (3/5 * 1/2) / [(3/5 * 1/2) + (4/5 * 1/2)]
P(A|R) = (3/10) / [(3/10) + (4/10)]
P(A|R) = (3/10) / (7/10)
P(A|R) = 3/7
So, the probability of selecting Bag A, given that a red marble was chosen, is 3/7, which corresponds to option D.
|
|
Raksha Mishra upvoted • Jan 17, 2025 |
In which of the following method does the code is written in a straight sequence?- a)method 1
- b)timing method
- c)sequence method
- d)spaghetti method
Correct answer is option 'D'. Can you explain this answer?
In which of the following method does the code is written in a straight sequence?
a)
method 1
b)
timing method
c)
sequence method
d)
spaghetti method
|
|
Jyoti Sengupta answered |
Explanation: In the spaghetti method, the code is written in a straight sequence in which the analysis software goes and polls the port to see if there is data.
|
|
Raksha Mishra upvoted • Dec 30, 2024 |
In which of the following no information hiding is done?- a)Compile prig 1, prig 2
- b)Run test, prog
- c)Load R1 , A
- d)001001000010101
Correct answer is option 'D'. Can you explain this answer?
In which of the following no information hiding is done?
a)
Compile prig 1, prig 2
b)
Run test, prog
c)
Load R1 , A
d)
001001000010101
|
|
Shubham Chaudhary answered |
The entire binary symbol gives the information.
|
|
Raksha Mishra upvoted • Oct 21, 2024 |
In reading the columns of a matrix, if no key is pressed we should get all in binary notation- a)0
- b)1
- c)F
- d)7
Correct answer is option 'B'. Can you explain this answer?
In reading the columns of a matrix, if no key is pressed we should get all in binary notation
a)
0
b)
1
c)
F
d)
7
|
|
Shruti Tiwari answered |
If no key is pressed, then all the keys show 1 as they are all connected to power supply.
|
|
Raksha Mishra upvoted • Oct 03, 2024 |
The chip 74LS245 is- a)bidirectional buffer
- b)8-bit input port
- c)one that has 8 buffers
- d)all of the mentioned
Correct answer is option 'D'. Can you explain this answer?
The chip 74LS245 is
a)
bidirectional buffer
b)
8-bit input port
c)
one that has 8 buffers
d)
all of the mentioned
|
|
Kiran Chakraborty answered |
The chip 74LS245 is a bidirectional buffer that contains 8 buffers and may be used as an 8-bit input port. But while using as an input device, only one direction is useful.
A common measure of performance is- a)Price/performance ratio
- b)Performance/price ratio
- c)Operation/price ratio
- d)None of the mentioned
Correct answer is option 'A'. Can you explain this answer?
A common measure of performance is
a)
Price/performance ratio
b)
Performance/price ratio
c)
Operation/price ratio
d)
None of the mentioned
|
|
Raksha Mishra answered • Sep 28, 2024 |
Understanding Price/Performance Ratio
The Price/Performance ratio is a crucial metric in evaluating the efficiency and value of a product, especially in fields such as Computer Science Engineering. Here’s a detailed explanation of why option 'A' is the correct measure of performance:
Definition of Price/Performance Ratio
- The Price/Performance ratio quantifies the cos... more
The Price/Performance ratio is a crucial metric in evaluating the efficiency and value of a product, especially in fields such as Computer Science Engineering. Here’s a detailed explanation of why option 'A' is the correct measure of performance:
Definition of Price/Performance Ratio
- The Price/Performance ratio quantifies the cos... more
The read and write operations usually start at ______ of the sector.- a)Center
- b)Middle
- c)From the last used point
- d)Boundaries
Correct answer is option 'D'. Can you explain this answer?
The read and write operations usually start at ______ of the sector.
a)
Center
b)
Middle
c)
From the last used point
d)
Boundaries
|
|
Raksha Mishra answered • Sep 28, 2024 |
Understanding Read and Write Operations in Disk Sectors
In computer storage, data is organized into sectors, which are the smallest units of storage on a disk. The way read and write operations are executed is crucial for data integrity and performance.
Starting Point of Operations
- Read and write operations typically begin at the boundaries of the sector. This... more
In computer storage, data is organized into sectors, which are the smallest units of storage on a disk. The way read and write operations are executed is crucial for data integrity and performance.
Starting Point of Operations
- Read and write operations typically begin at the boundaries of the sector. This... more
I'm asking if bubble sort a stable sort and please give me proof on it.?
|
|
Raksha Mishra answered • Jul 11, 2024 |
Is Bubble Sort a Stable Sort?
Definition of Stable Sort
- A stable sort is a sorting algorithm where the relative order of equal elements is preserved in the sorted output.
Proof that Bubble Sort is a Stable Sort
- In Bubble Sort, when two elements are swapped, the condition for swapping is that the element on the right is smaller than the eleme... more
Definition of Stable Sort
- A stable sort is a sorting algorithm where the relative order of equal elements is preserved in the sorted output.
Proof that Bubble Sort is a Stable Sort
- In Bubble Sort, when two elements are swapped, the condition for swapping is that the element on the right is smaller than the eleme... more
Which one of the following is an internet standard protocol for managing devices on IP network?- a)dynamic host configuration protocol
- b)simple network management protocol
- c)internet message access protocol
- d)media gateway protocol
Correct answer is option 'B'. Can you explain this answer?
Which one of the following is an internet standard protocol for managing devices on IP network?
a)
dynamic host configuration protocol
b)
simple network management protocol
c)
internet message access protocol
d)
media gateway protocol
|
|
Raksha Mishra answered • May 08, 2024 |
Simple Network Management Protocol (SNMP)
SNMP is an internet standard protocol used for managing devices on IP networks. Here is a detailed explanation of SNMP:
Overview
- SNMP is commonly used in network management systems to monitor network-attached devices for conditions that warrant administrative attention.
- It allows network administrators to manage ... more
SNMP is an internet standard protocol used for managing devices on IP networks. Here is a detailed explanation of SNMP:
Overview
- SNMP is commonly used in network management systems to monitor network-attached devices for conditions that warrant administrative attention.
- It allows network administrators to manage ... more
Which of the following is an efficient method of cache updating?- a)Snoopy writes
- b)Write through
- c)Write within
- d)Buffered write
Correct answer is option 'A'. Can you explain this answer?
Which of the following is an efficient method of cache updating?
a)
Snoopy writes
b)
Write through
c)
Write within
d)
Buffered write
|
|
Raksha Mishra answered • Mar 15, 2024 |
Explanation:
Snoopy writes:
- Snoopy write is an efficient method of cache updating where the cache controller monitors or snoops the bus for write requests to main memory.
- When a write request is detected, the cache controller updates the corresponding cache line to ensure data consistency between the cache and main memory.
- This method help... more
EE-ROM is- a)Electrically erasable
- b)Easily erasable
- c)Non-erasable
- d)Effective erasable
Correct answer is option 'A'. Can you explain this answer?
EE-ROM is
a)
Electrically erasable
b)
Easily erasable
c)
Non-erasable
d)
Effective erasable
|
|
Raksha Mishra answered • Feb 06, 2024 |
Introduction:
EE-ROM stands for Electrically Erasable Read-Only Memory. It is a type of non-volatile memory that can be electrically erased and reprogrammed. In this response, we will explain why option 'A' is the correct answer.
Explanation:
EE-ROM is a type of memory that combines the features of ROM (Read-Only Memory) and EPROM (Erasable Programmable Read-Only... more
EE-ROM stands for Electrically Erasable Read-Only Memory. It is a type of non-volatile memory that can be electrically erased and reprogrammed. In this response, we will explain why option 'A' is the correct answer.
Explanation:
EE-ROM is a type of memory that combines the features of ROM (Read-Only Memory) and EPROM (Erasable Programmable Read-Only... more
The instruction that pushes the contents of the specified register/memory location on to the stack is- a)PUSHF
- b)POPF
- c)PUSH
- d)POP
Correct answer is option 'C'. Can you explain this answer?
The instruction that pushes the contents of the specified register/memory location on to the stack is
a)
PUSHF
b)
POPF
c)
PUSH
d)
POP
|
|
Raksha Mishra answered • Jan 14, 2024 |
Explanation:
In computer architecture, the stack is a region of memory used for temporary storage. It follows the Last-In-First-Out (LIFO) principle, which means that the last item pushed onto the stack is the first one to be popped off.
The instruction that pushes the contents of the specified register or memory location onto the stack is the PUSH instruction.
<... more
In computer architecture, the stack is a region of memory used for temporary storage. It follows the Last-In-First-Out (LIFO) principle, which means that the last item pushed onto the stack is the first one to be popped off.
The instruction that pushes the contents of the specified register or memory location onto the stack is the PUSH instruction.
<... more
ANSI stands for __________- a)American National Standards Institute
- b)American National Standard Interface
- c)American Network Standard Interfacing
- d)American Network Security Interrupt
Correct answer is option 'A'. Can you explain this answer?
ANSI stands for __________
a)
American National Standards Institute
b)
American National Standard Interface
c)
American Network Standard Interfacing
d)
American Network Security Interrupt
|
|
Raksha Mishra answered • Dec 30, 2023 |
Introduction:
ANSI stands for the American National Standards Institute. It is a non-profit organization that oversees the development of voluntary consensus standards for products, services, processes, and systems in the United States.
Explanation:
The correct answer to the given question is option 'A' - American National Standards Institute.
Ameri... more
The American National Standards Institute (ANSI) is a private, non-profit organization that administers and coordinates the United States' voluntary standards and conformity assessment system. It brings together stakeholders from industry, government, and academia to develop consensus-based standards that promote innovation, enhance competitiveness, and ensure the safety and health of consumers and the environment.
Development of Standards:
ANSI facilitates the development of standards across various sectors, including technology, manufacturing, energy, telecommunications, and more. These standards are developed by committees consisting of experts in the relevant fields who participate in a consensus-based process. ANSI provides oversight and coordination to ensure that the process is fair, open, and transparent.
Voluntary Consensus Standards:
ANSI standards are voluntary consensus standards, meaning they are developed through a collaborative process that involves input and agreement from all interested stakeholders. This ensures that the resulting standards reflect the needs and perspectives of the industry, government, and consumers. Voluntary consensus standards are widely adopted and serve as a benchmark for quality, safety, and interoperability.
Benefits of ANSI Standards:
ANSI standards play a crucial role in fostering innovation, improving product quality, and enhancing safety. They provide a level playing field for businesses, promote interoperability between different systems and products, and facilitate trade by eliminating technical barriers. ANSI standards also help protect the environment, promote sustainability, and ensure the health and well-being of consumers.
Conclusion:
In conclusion, ANSI stands for the American National Standards Institute. It is a non-profit organization responsible for overseeing the development of voluntary consensus standards in the United States. These standards play a vital role in promoting innovation, enhancing competitiveness, and ensuring the safety and health of consumers and the environment.
ANSI stands for the American National Standards Institute. It is a non-profit organization that oversees the development of voluntary consensus standards for products, services, processes, and systems in the United States.
Explanation:
The correct answer to the given question is option 'A' - American National Standards Institute.
Ameri... more
The American National Standards Institute (ANSI) is a private, non-profit organization that administers and coordinates the United States' voluntary standards and conformity assessment system. It brings together stakeholders from industry, government, and academia to develop consensus-based standards that promote innovation, enhance competitiveness, and ensure the safety and health of consumers and the environment.
Development of Standards:
ANSI facilitates the development of standards across various sectors, including technology, manufacturing, energy, telecommunications, and more. These standards are developed by committees consisting of experts in the relevant fields who participate in a consensus-based process. ANSI provides oversight and coordination to ensure that the process is fair, open, and transparent.
Voluntary Consensus Standards:
ANSI standards are voluntary consensus standards, meaning they are developed through a collaborative process that involves input and agreement from all interested stakeholders. This ensures that the resulting standards reflect the needs and perspectives of the industry, government, and consumers. Voluntary consensus standards are widely adopted and serve as a benchmark for quality, safety, and interoperability.
Benefits of ANSI Standards:
ANSI standards play a crucial role in fostering innovation, improving product quality, and enhancing safety. They provide a level playing field for businesses, promote interoperability between different systems and products, and facilitate trade by eliminating technical barriers. ANSI standards also help protect the environment, promote sustainability, and ensure the health and well-being of consumers.
Conclusion:
In conclusion, ANSI stands for the American National Standards Institute. It is a non-profit organization responsible for overseeing the development of voluntary consensus standards in the United States. These standards play a vital role in promoting innovation, enhancing competitiveness, and ensuring the safety and health of consumers and the environment.
A regular language over an alphabet ∑ is one that cannot be obtained from the basic languages using the operation- a)Union
- b)Concatenation
- c)Kleene*
- d)All of the mentioned
Correct answer is option 'D'. Can you explain this answer?
A regular language over an alphabet ∑ is one that cannot be obtained from the basic languages using the operation
a)
Union
b)
Concatenation
c)
Kleene*
d)
All of the mentioned
|
|
Raksha Mishra answered • Dec 08, 2023 |
An alphabet is a set of symbols or characters that are used to form words or strings in a language. A regular language is a type of formal language that can be described and recognized by a regular expression, a deterministic finite automaton (DFA), a non-deterministic finite automaton (NFA), or a regular grammar.
In the context of regular languages, an alphabet refers to the set of sym... more
In the context of regular languages, an alphabet refers to the set of sym... more
A processor X1 operating at 2 GHz has a standard 5-stage RISC instruction pipeline having a base CPI (cycles per instruction) of one without any pipeline hazards. For a given program P that has 30% branch instructions, control hazards incur 2 cycles stall for every branch. A new version of the processor X2 operating at same clock frequency has an additional branch predictor unit (BPU) that completely eliminates stalls for correctly predicted branches. There is neither any savings nor any additional stalls for wrong predictions. There are no structural hazards and data hazards for X1 and X2. If the BPU has a prediction accuracy of 80%, the speed up (rounded off to two decimal places) obtained by X2 over X1 in executing P is ______.
Correct answer is between '1.42,1.43'. Can you explain this answer?
A processor X1 operating at 2 GHz has a standard 5-stage RISC instruction pipeline having a base CPI (cycles per instruction) of one without any pipeline hazards. For a given program P that has 30% branch instructions, control hazards incur 2 cycles stall for every branch. A new version of the processor X2 operating at same clock frequency has an additional branch predictor unit (BPU) that completely eliminates stalls for correctly predicted branches. There is neither any savings nor any additional stalls for wrong predictions. There are no structural hazards and data hazards for X1 and X2. If the BPU has a prediction accuracy of 80%, the speed up (rounded off to two decimal places) obtained by X2 over X1 in executing P is ______.
|
|
Raksha Mishra answered • Nov 22, 2023 |
Given Information:
- Processor X1 operates at 2 GHz (clock frequency).
- X1 has a 5-stage RISC instruction pipeline with a base CPI of 1 (without any pipeline hazards).
- Program P has 30% branch instructions, and control hazards incur a 2-cycle stall for every branch.
Calculating Execution Time for X1:
The execution time for a program can be calculated... more
- Processor X1 operates at 2 GHz (clock frequency).
- X1 has a 5-stage RISC instruction pipeline with a base CPI of 1 (without any pipeline hazards).
- Program P has 30% branch instructions, and control hazards incur a 2-cycle stall for every branch.
Calculating Execution Time for X1:
The execution time for a program can be calculated... more
|
|
Raksha Mishra asked • Sep 28, 2022 |
The ratio of the area of the inscribed circle to the area of the circumscribed circle of an equilateral triangle is _____
- a)1/8
- b)1/6
- c)1/2
- d)1/4
Correct answer is option 'D'. Can you explain this answer?
The ratio of the area of the inscribed circle to the area of the circumscribed circle of an equilateral triangle is _____

a)
1/8
b)
1/6
c)
1/2
d)
1/4
|
|
Sudhir Patel answered |
Let the radius of the circumscribed circle is R, and the radius of the inscribed circle is r.
Then area of circumscribed circle = πR2
Then the area of the inscribed circle = πr2
We know the angle between two adjacent sides in an equilateral triangle is 60°.
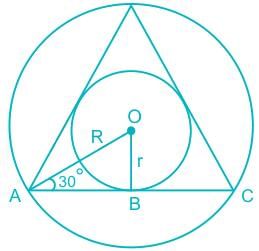
ΔOAB, Sin30 = r / R
R = 2r
The ratio of the area of the inscribed circle to the area of the circumscribed circle
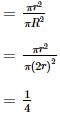
|
|
Raksha Mishra asked • Jul 01, 2021 |
Three concurrent processes X, Y, and Z execute three different code segments that access and update certain shared variables. Process X executes the P operation (i.e., wait) on semaphores a, b and c; process Y executes the P operation on semaphores b, c and d; process Z executes the P operation on semaphores c, d, and a before entering the respective code segments. After completing the execution of its code segment, each process invokes the V operation (i.e., signal) on its three semaphores. All semaphores are binary semaphores initialized to one. Which one of the following represents a deadlock-free order of invoking the P operations by the processes?- a)X: P(a)P(b)P(c) Y: P(b)P(c)P(d) Z: P(c)P(d)P(a)
- b)X: P(b)P(a)P(c) Y: P(b)P(c)P(d) Z: P(a)P(c)P(d)
- c)X: P(b)P(a)P(c) Y: P(c)P(b)P(d) Z: P(a)P(c)P(d)
- d)X: P(a)P(b)P(c) Y: P(c)P(b)P(d) Z: P(c)P(d)P(a)
Correct answer is option 'B'. Can you explain this answer?
Three concurrent processes X, Y, and Z execute three different code segments that access and update certain shared variables. Process X executes the P operation (i.e., wait) on semaphores a, b and c; process Y executes the P operation on semaphores b, c and d; process Z executes the P operation on semaphores c, d, and a before entering the respective code segments. After completing the execution of its code segment, each process invokes the V operation (i.e., signal) on its three semaphores. All semaphores are binary semaphores initialized to one. Which one of the following represents a deadlock-free order of invoking the P operations by the processes?
a)
X: P(a)P(b)P(c) Y: P(b)P(c)P(d) Z: P(c)P(d)P(a)
b)
X: P(b)P(a)P(c) Y: P(b)P(c)P(d) Z: P(a)P(c)P(d)
c)
X: P(b)P(a)P(c) Y: P(c)P(b)P(d) Z: P(a)P(c)P(d)
d)
X: P(a)P(b)P(c) Y: P(c)P(b)P(d) Z: P(c)P(d)P(a)
|
|
Sanya Agarwal answered |
Option A can cause deadlock. Imagine a situation process X has acquired a, process Y has acquired b and process Z has acquired c and d. There is circular wait now. Option C can also cause deadlock. Imagine a situation process X has acquired b, process Y has acquired c and process Z has acquired a. There is circular wait now. Option D can also cause deadlock. Imagine a situation process X has acquired a and b, process Y has acquired c. X and Y circularly waiting for each other.Consider option A) for example here all 3 processes are concurrent so X will get semaphore a, Y will get b and Z will get c, now X is blocked for b, Y is blocked for c, Z gets d and blocked for a. Thus it will lead to deadlock. Similarly one can figure out that for B) completion order is Z,X then Y.
|
|
Raksha Mishra asked • Jun 13, 2021 |
What is the time complexity for the following C module? Assume that n>0 . int module(int n) { if (n == 1) return 1; else return (n + module(n-1)); }- a)O(n)
- b)O(log n)
- c)O(n2)
- d)O(n!)
Correct answer is option 'A'. Can you explain this answer?
What is the time complexity for the following C module? Assume that n>0 . int module(int n) { if (n == 1) return 1; else return (n + module(n-1)); }
a)
O(n)
b)
O(log n)
c)
O(n2)
d)
O(n!)
|
|
Tanishq Yadav answered |
The time complexity of the following C module would be O(n), where n is the input size.
```c
void printNumbers(int n) {
for (int i = 0; i < n;="" i++)="" />
printf("%d ", i);
}
}
```
In this module, the function `printNumbers` iterates over the numbers from 0 to n-1 using a for loop. The loop runs n times, where n is the input siz... more
```c
void printNumbers(int n) {
for (int i = 0; i < n;="" i++)="" />
printf("%d ", i);
}
}
```
In this module, the function `printNumbers` iterates over the numbers from 0 to n-1 using a for loop. The loop runs n times, where n is the input siz... more
|
|
Raksha Mishra asked • Dec 30, 2020 |
Let x and y be positive real numbers such that log5(x + y) + log5(x - y) = 3, and log2y - log2x = 1 - log23. Then xy equals- a)25
- b)150
- c)250
- d)100
Correct answer is option 'B'. Can you explain this answer?
Let x and y be positive real numbers such that log5(x + y) + log5(x - y) = 3, and log2y - log2x = 1 - log23. Then xy equals
a)
25
b)
150
c)
250
d)
100
|
|
Vaibhav Banerjee answered |
Given that, log5(x + y) + log5(x - y) = 3
We know log A + log B = log (A x B)
log5(x + y) + log5(x - y) = log5(x2 - y2)
log5(x2 - y2) = 3
x2 - y2 = 53
x2 - y2 = 125
Similarly, log2y - log2x = 1 - log23
log2 y/x = log22 - log23
log2 y/x = log2 2/3
3y = 2x
(3/2 y)2 - y2 = 125
9/2 y2 - y2 = 125
5/4 y2 = 125
y2 = 100
y = 10
x = 15
So, xy = 15 × 10 = 150
We know log A + log B = log (A x B)
log5(x + y) + log5(x - y) = log5(x2 - y2)
log5(x2 - y2) = 3
x2 - y2 = 53
x2 - y2 = 125
Similarly, log2y - log2x = 1 - log23
log2 y/x = log22 - log23
log2 y/x = log2 2/3
3y = 2x
(3/2 y)2 - y2 = 125
9/2 y2 - y2 = 125
5/4 y2 = 125
y2 = 100
y = 10
x = 15
So, xy = 15 × 10 = 150
|
|
Raksha Mishra asked • Jan 02, 2020 |
What is the maximum height of any AVL-tree with 7 nodes? Assume that the height of a tree with a single node is 0.- a)2
- b)3
- c)4
- d)5
Correct answer is option 'B'. Can you explain this answer?
What is the maximum height of any AVL-tree with 7 nodes? Assume that the height of a tree with a single node is 0.
a)
2
b)
3
c)
4
d)
5
|
|
Dishani Bajaj answered |
Maximum height of any AVL-tree with 7.
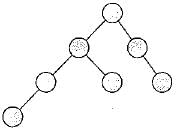
(There may be different way to draw AVL with 7 nodes).

(There may be different way to draw AVL with 7 nodes).
|
|
Raksha Mishra asked • Dec 25, 2019 |
'm' processes share 'n' resources of the same type. The maximum need of each process does not exceed 'n' and the sum all their maximum needs is always less than m + n. In this set up deadlock- a)Has to occur
- b)May occur
- c)Can never occur
- d)None of the these
Correct answer is option 'C'. Can you explain this answer?
'm' processes share 'n' resources of the same type. The maximum need of each process does not exceed 'n' and the sum all their maximum needs is always less than m + n. In this set up deadlock
a)
Has to occur
b)
May occur
c)
Can never occur
d)
None of the these
|
|
Rajesh Malik answered |
Assume m = 5 and n = 10
That means, 5 processes are sharing 10 resources and worst case will be if everyone is demanding equal number of cases.
So, for deadlock to be there every process must be holding 2 resources and seeking 1 more resource. This will make total demand to 15, which is nothing but 10 + 5 (m + n).
However, as given maximum demand is always less than (m + n), so we can say there will never be a deadlock.
That means, 5 processes are sharing 10 resources and worst case will be if everyone is demanding equal number of cases.
So, for deadlock to be there every process must be holding 2 resources and seeking 1 more resource. This will make total demand to 15, which is nothing but 10 + 5 (m + n).
However, as given maximum demand is always less than (m + n), so we can say there will never be a deadlock.
|
|
Raksha Mishra asked • Dec 11, 2019 |
What is the maximum number of edges in an acyclic undirected graph with n vertices?- a)n - 1
- b)n
- c)n + 1
- d)2n - 1
Correct answer is option 'A'. Can you explain this answer?
What is the maximum number of edges in an acyclic undirected graph with n vertices?
a)
n - 1
b)
n
c)
n + 1
d)
2n - 1
|
|
Tushar Unni answered |
n * (n – 1) / 2 when cyclic. But acyclic graph with the maximum number of edges is actually a spanning tree and therefore, correct answer is n-1 edges.
|
|
Raksha Mishra asked • Nov 30, 2019 |
A girl entered a store and bought x flowers for y dollars (x and y are integers). When she was about to leave, the clerk said, “If you buy 10 more flowers I will give you all for $$2, and you will save 80 cents a dozen”. The values of x and y are?- a)(15,1)
- b)(10,1)
- c)(5,1)
- d)Cannot be determined from the given information.
Correct answer is option 'C'. Can you explain this answer?
A girl entered a store and bought x flowers for y dollars (x and y are integers). When she was about to leave, the clerk said, “If you buy 10 more flowers I will give you all for $$2, and you will save 80 cents a dozen”. The values of x and y are?
a)
(15,1)
b)
(10,1)
c)
(5,1)
d)
Cannot be determined from the given information.
|
|
Sandeep Majumdar answered |
Given she bought xx flowers for yy dollars.
So 1 flower cost = yxyx
flowers or 1 dozen cost = 12yx12yx
Again, xx+10 cost = 2 dollars
1 flower cost = 210+x210+x
12 flowers or 1 dozen cost = 2×1210+x=2410+x2×1210+x=2410+x
Given that this new dozen cost is 80 cents or 4/5 dollar less than original cost.
⇒12yx−2410+x=45⇒12yx−2410+x=45
From the given options, c satisfies this.
|
|
Raksha Mishra asked • Nov 25, 2019 |
Match the protocols with the port numbers.
- a)P – W, Q – Z, R – Y, S – X
- b)P – X, Q – W, R – Z, S – Y
- c)P – Y, Q – X, R – W, S – Z
- d)P – Y, Q – X, R – Z, S – W
Correct answer is option 'D'. Can you explain this answer?
Match the protocols with the port numbers.
a)
P – W, Q – Z, R – Y, S – X
b)
P – X, Q – W, R – Z, S – Y
c)
P – Y, Q – X, R – W, S – Z
d)
P – Y, Q – X, R – Z, S – W
|
|
Swara Basak answered |
HTTPS – 443
SNMP – 161
SMB – 445
POP3 – 110
SNMP – 161
SMB – 445
POP3 – 110
Fetching relevant content for you