|
|
Naina ShahEduRev Computer Science Engineering (CSE) |
|
|
Naina Shah
EduRev Computer Science Engineering (CSE)
|
Content, tests & courses saved by you for accessing later. (visible to you only)
Discussed Questions
Consider a simple undirected weighted graph G, all of whose edge weights are distinct. Which of the following statements about the MST of G is/are true? - a)Suppose S⊆V be such that S ≠ θ and S ≠ V. Consider the edge with min weight such that one of its vertices is in S and the other in V\S. Such an edge will always be part of any MST of G.
- b)G can have multiple spanning trees.
- c)One or both the edges with the third smallest and the fourth-smallest edges are part of any MST of G.
- d)The edge with the second-smallest weight is always part of any MST of G.
Correct answer is option 'A,C,D'. Can you explain this answer?
Consider a simple undirected weighted graph G, all of whose edge weights are distinct. Which of the following statements about the MST of G is/are true?
a)
Suppose S⊆V be such that S ≠ θ and S ≠ V. Consider the edge with min weight such that one of its vertices is in S and the other in V\S. Such an edge will always be part of any MST of G.
b)
G can have multiple spanning trees.
c)
One or both the edges with the third smallest and the fourth-smallest edges are part of any MST of G.
d)
The edge with the second-smallest weight is always part of any MST of G.
|
|
Naina Shah answered • Feb 09, 2025 |
Explanation of the Correct Answers
To understand why options A, C, and D are correct regarding the MST (Minimum Spanning Tree) of the graph G, let's break down each statement.
Option A: Cut Property
- If you have a subset S of vertices in graph G, and you consider the edge with the minimum weight that connects a vertex in S to a vertex in V\S (the rest of the vertices)... more
To understand why options A, C, and D are correct regarding the MST (Minimum Spanning Tree) of the graph G, let's break down each statement.
Option A: Cut Property
- If you have a subset S of vertices in graph G, and you consider the edge with the minimum weight that connects a vertex in S to a vertex in V\S (the rest of the vertices)... more
|
|
Naina Shah upvoted • Feb 07, 2025 |
What is the difference between the DROP and TRUNCATE commands in SQL?- a)DROP deletes the table, TRUNCATE deletes only the table data
- b)TRUNCATE deletes the table, DROP deletes only the table data
- c)No difference
- d)Both commands modify table data
Correct answer is option 'A'. Can you explain this answer?
What is the difference between the DROP and TRUNCATE commands in SQL?
a)
DROP deletes the table, TRUNCATE deletes only the table data
b)
TRUNCATE deletes the table, DROP deletes only the table data
c)
No difference
d)
Both commands modify table data

|
Machine Experts answered |
DROP deletes the entire table, while TRUNCATE removes only its data but keeps the table structure.
|
|
Naina Shah upvoted • Jan 17, 2025 |
The access times of the main memory and the Cache memory, in a computer system, are 500 n sec and 50 n sec, respectively. It is estimated that 80% of the main memory request are for read the rest for write. The hit ratio for the read access only is 0.9 and a write-through policy (where both main and cache memories are updated simultaneously) is used.
Determine the average time of the main memory.
Correct answer is '180ns'. Can you explain this answer?
The access times of the main memory and the Cache memory, in a computer system, are 500 n sec and 50 n sec, respectively. It is estimated that 80% of the main memory request are for read the rest for write. The hit ratio for the read access only is 0.9 and a write-through policy (where both main and cache memories are updated simultaneously) is used.
Determine the average time of the main memory.
Determine the average time of the main memory.

|
Bayshore Academy answered |
Average memory access time = Time spend for read + Time spend for write= Read time when cache hit + Read time when cache miss+Write time when cache hit + Write time when cache miss= 0.8 ⨯ 0.9 ⨯ 50 + 0.8 ⨯ 0.1 ⨯ (500+50) (assuming hierarchical read from memory and cache as only simultaneous write is mentioned in question)+ 0.2 ⨯ 0.9 ⨯ 500 + 0.2 ⨯ 0.1 ⨯ 500 (simultaneous write mentioned in question)= 36 + 44 + 90 + 10 = 180 ns
|
|
Naina Shah upvoted • Jan 01, 2025 |
Consider a three-level page table to translate a 39-bit virtual address to a physical address as shown below: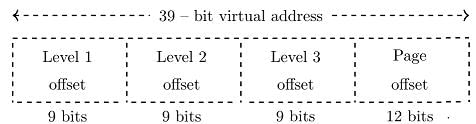 The page size is 4 KB(1 KB = 210 bytes ) and page table entry size at every level is 8 bytes. A process P is currently using 2 GB(1 GB = 230 bytes) virtual memory which is mapped to 2 GB of physical memory. The minimum amount of memory required for the page table of P across all levels is _____________ KB.
The page size is 4 KB(1 KB = 210 bytes ) and page table entry size at every level is 8 bytes. A process P is currently using 2 GB(1 GB = 230 bytes) virtual memory which is mapped to 2 GB of physical memory. The minimum amount of memory required for the page table of P across all levels is _____________ KB.- a) 4108
- b) 4110
- c) 3108
- d) 4008
Correct answer is option 'A'. Can you explain this answer?
Consider a three-level page table to translate a 39-bit virtual address to a physical address as shown below:

The page size is 4 KB(1 KB = 210 bytes ) and page table entry size at every level is 8 bytes. A process P is currently using 2 GB(1 GB = 230 bytes) virtual memory which is mapped to 2 GB of physical memory. The minimum amount of memory required for the page table of P across all levels is _____________ KB.
a)
4108
b)
4110
c)
3108
d)
4008

|
Riverdale Learning Institute answered |
Given,
- Virtual address (VA) = 39 bits
- Page size = 4 KB
- Physical address (PA) = 2 GB
- Page table entry size (PTE) = 8 B
- Three level pages tables with address division (9, 9, 9, 12)
Three level pages tables with address division (9, 9, 9, 12) means:
- 9 most significant bits for indexing into the level−1 (outer level).
- 9 bits for the level−2 index.
- 9 bits for the level−3 index.
- 12 bits for the offset within a page.
What is the output of given program if user enter value 99?#include<stdio.h>
void main()
{
int i;
printf("Enter a number:");
scanf("%d", &i); // 99 is given as input.
if(i%5 == 0){
printf("nNumber entered is divisible by 5");
}
}- a)Enter a number:99
- b)Enter a number:99 Number is divisible by 5
- c)complier error
- d)Run time error
Correct answer is option 'A'. Can you explain this answer?
What is the output of given program if user enter value 99?
#include<stdio.h>
void main()
{
int i;
printf("Enter a number:");
scanf("%d", &i); // 99 is given as input.
if(i%5 == 0){
printf("nNumber entered is divisible by 5");
}
}
void main()
{
int i;
printf("Enter a number:");
scanf("%d", &i); // 99 is given as input.
if(i%5 == 0){
printf("nNumber entered is divisible by 5");
}
}
a)
Enter a number:99
b)
Enter a number:99 Number is divisible by 5
c)
complier error
d)
Run time error
|
|
Naina Shah answered • Dec 05, 2024 |
Program Overview
The provided C program prompts the user to enter a number and checks if that number is divisible by 5. The main parts of the code include:
- Variable Declaration: An integer variable `i` is declared.
- Input Prompt: The user is asked to enter a number.
- Input Capture: The program captures the input using `scanf`.
- Divisibil... more: The program checks if the number is divisible by 5.
Input Analysis
When the user enters the value 99, the following occurs:
- The program prints: "Enter a number:"
- The input `99` is stored in the variable `i`.
Condition Evaluation
The critical part of the program is the `if` statement:
- Condition: `if(i % 5 == 0)`
- For `i = 99`, the calculation becomes `99 % 5`, which equals 4 (not divisible by 5).
Program Output
Since the condition evaluates to false, the code inside the `if` block does not execute. Therefore, there is no additional output related to divisibility.
Final Output
The only output from the program when the user enters 99 is:
- "Enter a number:99"
This leads us to conclude that the correct answer is option A: Enter a number:99.
Summary
- The program correctly prompts for input.
- Since 99 is not divisible by 5, no further message is printed.
- Hence, option A accurately reflects the output.
The provided C program prompts the user to enter a number and checks if that number is divisible by 5. The main parts of the code include:
- Variable Declaration: An integer variable `i` is declared.
- Input Prompt: The user is asked to enter a number.
- Input Capture: The program captures the input using `scanf`.
- Divisibil... more: The program checks if the number is divisible by 5.
Input Analysis
When the user enters the value 99, the following occurs:
- The program prints: "Enter a number:"
- The input `99` is stored in the variable `i`.
Condition Evaluation
The critical part of the program is the `if` statement:
- Condition: `if(i % 5 == 0)`
- For `i = 99`, the calculation becomes `99 % 5`, which equals 4 (not divisible by 5).
Program Output
Since the condition evaluates to false, the code inside the `if` block does not execute. Therefore, there is no additional output related to divisibility.
Final Output
The only output from the program when the user enters 99 is:
- "Enter a number:99"
This leads us to conclude that the correct answer is option A: Enter a number:99.
Summary
- The program correctly prompts for input.
- Since 99 is not divisible by 5, no further message is printed.
- Hence, option A accurately reflects the output.
|
|
Naina Shah upvoted • Oct 22, 2024 |
Which of the following is used to provide a baseline measure for comparison of IDSes?- a)Crossover error rate
- b)False negative rate
- c)False positive rate
- d)Bit error rate
Correct answer is option 'A'. Can you explain this answer?
Which of the following is used to provide a baseline measure for comparison of IDSes?
a)
Crossover error rate
b)
False negative rate
c)
False positive rate
d)
Bit error rate
|
|
Diya Chauhan answered |
Answer: a
Explanation: As the sensitivity of systems may cause the false positive/negative rates to vary, it’s critical to have some common measure that may be applied across the board.
Explanation: As the sensitivity of systems may cause the false positive/negative rates to vary, it’s critical to have some common measure that may be applied across the board.
|
|
Naina Shah upvoted • Oct 07, 2024 |
Let N be the set of natural numbers. Consider the following sets, P: Set of Rational numbers (positive and negative) Q: Set of functions from {0, 1} to N R: Set of functions from N to {0, 1} S: Set of finite subsets of N Which of the above sets are countable?- a)Q and S only
- b)P and S only
- c)P and R only
- d)P, Q and S only
Correct answer is option 'D'. Can you explain this answer?
Let N be the set of natural numbers. Consider the following sets, P: Set of Rational numbers (positive and negative) Q: Set of functions from {0, 1} to N R: Set of functions from N to {0, 1} S: Set of finite subsets of N Which of the above sets are countable?
a)
Q and S only
b)
P and S only
c)
P and R only
d)
P, Q and S only
|
|
Kalyan Menon answered |
Set of Rational numbers (+ve or -ve) are countable.. Set of functions from {0, 1} to N are countable because it has one to one correspondence to N. Set of functions from N to {0, 1} is uncountable, because it has one to one correspondence to set of real numbers between (0 and 1). Set of finite subsets of N is countable. Sets P, Q and S are countable, therefore option (D) is Correct.
A _________ Fc for F is a set of dependencies such that F logically implies all dependencies in Fc, and Fc logically implies all dependencies in F.- a)Canonical cover
- b)Complete cover
- c)Canonical dependency
- d)Canonical clause
Correct answer is option 'A'. Can you explain this answer?
A _________ Fc for F is a set of dependencies such that F logically implies all dependencies in Fc, and Fc logically implies all dependencies in F.
a)
Canonical cover
b)
Complete cover
c)
Canonical dependency
d)
Canonical clause
|
|
Naina Shah answered • Sep 16, 2024 |
Understanding Canonical Cover
A canonical cover is an essential concept in database theory, particularly in the context of functional dependencies. It serves to simplify a set of functional dependencies while preserving their meaning.
Definition of Canonical Cover
- A canonical cover for a set of functional dependencies \( F \) is a minimal set \( Fc \) such tha... more
A canonical cover is an essential concept in database theory, particularly in the context of functional dependencies. It serves to simplify a set of functional dependencies while preserving their meaning.
Definition of Canonical Cover
- A canonical cover for a set of functional dependencies \( F \) is a minimal set \( Fc \) such tha... more
Which of the following is standardised as IEEE 1364?- a)C
- b)C++
- c)FORTRAN
- d)Verilog
Correct answer is option 'D'. Can you explain this answer?
Which of the following is standardised as IEEE 1364?
a)
C
b)
C++
c)
FORTRAN
d)
Verilog
|
|
Naina Shah answered • Jun 24, 2024 |
IEEE 1364 Standardisation:
Verilog is standardised as IEEE 1364. Here is an explanation of this standardisation:
Verilog:
- Verilog is a hardware description language (HDL) used to model electronic systems. It allows designers to describe the behavior of electronic systems and verify them through simulation.
- Verilog is widely used in the design and verific... more
Verilog is standardised as IEEE 1364. Here is an explanation of this standardisation:
Verilog:
- Verilog is a hardware description language (HDL) used to model electronic systems. It allows designers to describe the behavior of electronic systems and verify them through simulation.
- Verilog is widely used in the design and verific... more
Consider the following intermediate program in three address codep = a - bq = p * cp = u * vq = p + qWhich one of the following corresponds to a static single assignment form of the above code?- a)p1 = a - bq1 = p1 * cp1 = u * vq1 = p1 + q1
- b)p3 = a - bq4 = p3 * cp4 = u * vq5 = p4 + q4
- c)p1 = a - bq1 = p2 * cp3 = u * vq2 = p4 + q3
- d)p1 = a - bq1 = p * cp2 = u * vq2 = p + q
Correct answer is option 'B'. Can you explain this answer?
Consider the following intermediate program in three address code
p = a - b
q = p * c
p = u * v
q = p + q
Which one of the following corresponds to a static single assignment form of the above code?
a)
p1 = a - b
q1 = p1 * c
p1 = u * v
q1 = p1 + q1
b)
p3 = a - b
q4 = p3 * c
p4 = u * v
q5 = p4 + q4
c)
p1 = a - b
q1 = p2 * c
p3 = u * v
q2 = p4 + q3
d)
p1 = a - b
q1 = p * c
p2 = u * v
q2 = p + q
|
|
Naina Shah answered • Apr 25, 2024 |
Explanation:
Static Single Assignment Form (SSA)
- SSA form is a type of intermediate representation where each variable is assigned exactly once.
- In the given code snippet, we need to transform the code into SSA form.
Transformation Steps:
Step 1:
- p = a - b
- Convert p to p3: p3 = a - b
Step 2:<... more
Static Single Assignment Form (SSA)
- SSA form is a type of intermediate representation where each variable is assigned exactly once.
- In the given code snippet, we need to transform the code into SSA form.
Transformation Steps:
Step 1:
- p = a - b
- Convert p to p3: p3 = a - b
Step 2:<... more
How is the status of the carry, auxiliary carry and parity flag affected if write instructionMOV A,#9CADD A,#64H- a)CY=0,AC=0,P=0
- b)CY=1,AC=1,P=0
- c)CY=0,AC=1,P=0
- d)CY=1,AC=1,P=1
Correct answer is option 'B'. Can you explain this answer?
How is the status of the carry, auxiliary carry and parity flag affected if write instructionMOV A,#9CADD A,#64H
a)
CY=0,AC=0,P=0
b)
CY=1,AC=1,P=0
c)
CY=0,AC=1,P=0
d)
CY=1,AC=1,P=1
|
|
Naina Shah answered • Mar 05, 2024 |
Explanation:
Initial values:
- Carry (CY) flag = 0
- Auxiliary carry (AC) flag = 0
- Parity (P) flag = 0
MOV A,#9C:
- Move immediate data 9C to register A
ADD A,#64H:
- Add immediate data 64H to register A
- Result: A = 9C + 64 = 00 (with carry)
Analysis:
- The CY flag is s... more
SMTP defines- a)message transport
- b)message encryption
- c)message content
- d)none of the mentioned
Correct answer is option 'A'. Can you explain this answer?
SMTP defines
a)
message transport
b)
message encryption
c)
message content
d)
none of the mentioned
|
|
Naina Shah answered • Feb 03, 2024 |
SMTP (Simple Mail Transfer Protocol) is a communication protocol used to transport electronic mail (email) messages between servers. It is mainly responsible for the message transport aspect of email communication. SMTP defines the process by which email messages are sent from the sender's mail server to the recipient's mail server.
1. Message Transport:
SMTP is prima... more
1. Message Transport:
SMTP is prima... more
A binary search tree is generated by inserting the following integers in order:50, 15, 62, 5, 20, 58, 91, 3, 8, 37, 60, 24How many nodes are there in the left sub-tree and the right sub-tree of the root, respectively?- a)(4, 7)
- b)(7, 4)
- c)(8, 3)
- d)(3, 8)
Correct answer is option 'B'. Can you explain this answer?
A binary search tree is generated by inserting the following integers in order:
50, 15, 62, 5, 20, 58, 91, 3, 8, 37, 60, 24
How many nodes are there in the left sub-tree and the right sub-tree of the root, respectively?
a)
(4, 7)
b)
(7, 4)
c)
(8, 3)
d)
(3, 8)
|
|
Naina Shah answered • Dec 06, 2023 |
Explanation:
To find the number of nodes in the left sub-tree and the right sub-tree of the root, we need to construct the binary search tree from the given integers.
Constructing the Binary Search Tree:
1. Start with an empty binary search tree.
2. Insert the integers in the given order: 50, 15, 62, 5, 20, 58, 91, 3, 8, 37, 60, 24.
The binary sea... more
To find the number of nodes in the left sub-tree and the right sub-tree of the root, we need to construct the binary search tree from the given integers.
Constructing the Binary Search Tree:
1. Start with an empty binary search tree.
2. Insert the integers in the given order: 50, 15, 62, 5, 20, 58, 91, 3, 8, 37, 60, 24.
The binary sea... more
Which among the following options are correct?Statement 1: TMs can accept languages that are not accepted by any PDA with one stack.Statement 2: But PDA with two stacks can accept any language that a TM can accept.- a)Statement 1 and 2, both are correct
- b)Statement 1 is correct but Statement 2 is false
- c)Statement 2 is correct while Statement 1 is false
- d)Statement 1 and 2, both are false
Correct answer is option 'A'. Can you explain this answer?
Which among the following options are correct?Statement 1: TMs can accept languages that are not accepted by any PDA with one stack.Statement 2: But PDA with two stacks can accept any language that a TM can accept.
a)
Statement 1 and 2, both are correct
b)
Statement 1 is correct but Statement 2 is false
c)
Statement 2 is correct while Statement 1 is false
d)
Statement 1 and 2, both are false
|
|
Naina Shah answered • Dec 06, 2023 |
Statement 1: TMs can accept languages that are not accepted by any PDA with one stack.
A Turing Machine (TM) is a theoretical computing machine that can simulate the logic of any computer algorithm. It consists of an input tape, a tape head, a set of states, and a transition function. TMs are more powerful than Pushdown Automata (PDA) because they have an infinite tape and can pe... more
A Turing Machine (TM) is a theoretical computing machine that can simulate the logic of any computer algorithm. It consists of an input tape, a tape head, a set of states, and a transition function. TMs are more powerful than Pushdown Automata (PDA) because they have an infinite tape and can pe... more
Let L1 be a recursive language. Let L2 and L3 be languages that are recursively enumerable but not recursive.
Which of the following statements is not necessarily true? - a)L2 – L1 is recursively enumerable
- b)L1 – L3 is recursively enumerable
- c)L2 ∩ L1 is recursively enumerable
- d)L2 ∪ L1 is recursively enumerable
Correct answer is option 'B'. Can you explain this answer?
Let L1 be a recursive language. Let L2 and L3 be languages that are recursively enumerable but not recursive.
Which of the following statements is not necessarily true?
Which of the following statements is not necessarily true?
a)
L2 – L1 is recursively enumerable
b)
L1 – L3 is recursively enumerable
c)
L2 ∩ L1 is recursively enumerable
d)
L2 ∪ L1 is recursively enumerable
|
|
Naina Shah answered • Dec 06, 2023 |
Explanation:
To understand why option B is not necessarily true, let's break down the properties of each type of language mentioned in the question.
Recursive Language (L1):
A recursive language is a language for which there exists a Turing machine that can decide whether a given input belongs to the language or not. In other words, there is an algorithm th... more
To understand why option B is not necessarily true, let's break down the properties of each type of language mentioned in the question.
Recursive Language (L1):
A recursive language is a language for which there exists a Turing machine that can decide whether a given input belongs to the language or not. In other words, there is an algorithm th... more
|
|
Naina Shah asked • Jan 20, 2023 |
A user by mistake writes an instruction to multiply, instead of divide. Which of the following devices can detect such error?- a)Compiler
- b)Interpreter
- c)Compiler or interpreter test
- d)None of these
Correct answer is option 'D'. Can you explain this answer?
A user by mistake writes an instruction to multiply, instead of divide. Which of the following devices can detect such error?
a)
Compiler
b)
Interpreter
c)
Compiler or interpreter test
d)
None of these
|
|
Eesha Bhat answered |
If it is a semantic error, it will not be detected by compiler. Since syntax of the instruction is correct, even interpreter will not be able to detect it and it will allow the instruction to be executed. The error will be pointed out by the TRAP interrupt generated by overflow condition.
|
|
Naina Shah asked • Jul 02, 2021 |
Given the relations employee (name, salary, dept-no), and department (dept-no, dept-name,address) Which of the following queries cannot be expressed using the basic relational algebra operations (σ, π, x, -, ∪, p)- a)Department address of every employee
- b)Employees whose name is the same as their department name
- c)The sum of all employees' salaries
- d)All employees of a given department
Correct answer is option 'C'. Can you explain this answer?
Given the relations employee (name, salary, dept-no), and department (dept-no, dept-name,address) Which of the following queries cannot be expressed using the basic relational algebra operations (σ, π, x, -, ∪, p)
a)
Department address of every employee
b)
Employees whose name is the same as their department name
c)
The sum of all employees' salaries
d)
All employees of a given department
|
|
Sanya Agarwal answered |
The sum of all employees' salaries can not be found using these above operations as to calculate sum we need aggregate functions and operators. So, option (C) is correct.
|
|
Naina Shah asked • Jun 17, 2021 |
Insert the characters of the string K R P C S N Y T J M into a hash table of size 10. Use the hash function
h(x) = ( ord(x) – ord("a") + 1 ) mod10
If linear probing is used to resolve collisions, then the following insertion causes collision- a)Y
- b)C
- c)M
- d)P
Correct answer is option 'C'. Can you explain this answer?
Insert the characters of the string K R P C S N Y T J M into a hash table of size 10. Use the hash function
h(x) = ( ord(x) – ord("a") + 1 ) mod10
If linear probing is used to resolve collisions, then the following insertion causes collision
h(x) = ( ord(x) – ord("a") + 1 ) mod10
If linear probing is used to resolve collisions, then the following insertion causes collision
a)
Y
b)
C
c)
M
d)
P
|
|
Sanya Agarwal answered |
(a) The hash table with size 10 will have index from 0 to 9. hash function = h(x) = ((ord(x) - ord(A) + 1)) mod 10 So for string K R P C S N Y T J M: K will be inserted at index : (11-1+1) mod 10 = 1 R at index: (18-1+1) mod 10 = 8 P at index: (16-1+1) mod 10 = 6 C at index: (3-1+1) mod 10 = 3 S at index: (19-1+1) mod 10 = 9 N at index: (14-1+1) mod 10 = 4 Y at index (25-1+1) mod 10 = 5 T at index (20-1+1) mod 10 = 0 J at index (10-1+1) mod 10 = 0 // first collision occurs. M at index (13-1+1) mod 10 = 3 //second collision occurs. Only J and M are causing the collision. (b) Final Hash table will be:
0 T
1 K
2 J
3 C
4 N
5 Y
6 P
7 M
8 R
9 S
0 T
1 K
2 J
3 C
4 N
5 Y
6 P
7 M
8 R
9 S
|
|
Naina Shah asked • Jun 03, 2021 |
Which of the following scheduling algorithms may cause starvation ? a. First-come-first-served b. Round Robin c. Priority d. Shortest process next e. Shortest remaining time first- a)a, c and e
- b)c, d and e
- c)b, d and e
- d)b, c and d
Correct answer is option 'B'. Can you explain this answer?
Which of the following scheduling algorithms may cause starvation ? a. First-come-first-served b. Round Robin c. Priority d. Shortest process next e. Shortest remaining time first
a)
a, c and e
b)
c, d and e
c)
b, d and e
d)
b, c and d
|
|
Sanya Agarwal answered |
- In First Come First Serve(FCFS) if a process with a very large Burst Time comes before other processes, the other process will have to wait for a long time but it is clear that other process will definitely get their chance to execute, so it will not suffer from starvation.
- In Round Robin there is a fixed time quant and every process will get their chance to be executed, so no starvation is here.
- In Priority based scheduling if higher priority process keep on coming then low priority process will suffer from starvation.
- In Shortest Job First(SJF) if process with short process time keep on coming continuously then process with higher burst time will do wait and suffer from starvation.
- In Shortest remaining time first(SRTF) process with shortest burst time will execute first because of this process with high burst time may suffer from starvation.
So, option (C) is correct.
|
|
Naina Shah asked • Jan 05, 2020 |
Which of the following languages is/are context free?
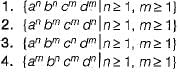
- a)1 and 2
- b)3 and 4
- c)2 and 4
- d)1, 2, 3 and 4
Correct answer is option 'A'. Can you explain this answer?
Which of the following languages is/are context free?
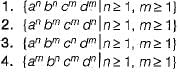
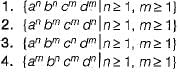
a)
1 and 2
b)
3 and 4
c)
2 and 4
d)
1, 2, 3 and 4
|
|
Avantika Shah answered |
Here for the languages (i) and (ii) we can design a PDA Hence they are CFL.
In (iii) and (iv) we cannot conclude whether number of (a) = number of (c) and number of (b) = number of (d) using only one stack memory so they aren’t CFL.
In (iii) and (iv) we cannot conclude whether number of (a) = number of (c) and number of (b) = number of (d) using only one stack memory so they aren’t CFL.
|
|
Naina Shah asked • Dec 29, 2019 |
The number of rotations required to insert a sequence of elements 9, 6, 5, 8, 7, 10 into an empty AVL tree is- a)0
- b)1
- c)2
- d)3
Correct answer is option 'D'. Can you explain this answer?
The number of rotations required to insert a sequence of elements 9, 6, 5, 8, 7, 10 into an empty AVL tree is
a)
0
b)
1
c)
2
d)
3
|
|
Vaibhav Banerjee answered |
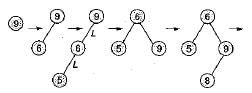
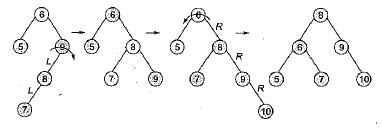
Number of rotations = 3
|
|
Naina Shah asked • Dec 22, 2019 |
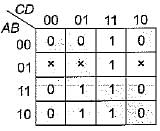
Which of the following functions implements the Karnaugh map shown below?
- a)
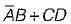
- b)D ( C + A )
- c)
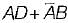
- d)
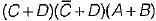
Correct answer is option 'B'. Can you explain this answer?
Which of the following functions implements the Karnaugh map shown below?


a)
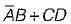
b)
D ( C + A )
c)
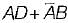
d)
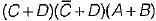
|
|
Palak Khanna answered |
Solving the given K-map we have
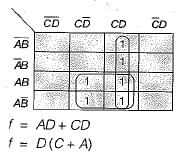
Hence (b) is correct option

Hence (b) is correct option
|
|
Naina Shah asked • Dec 15, 2019 |
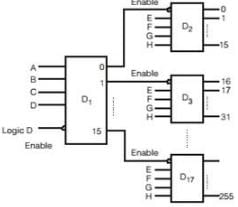
The number of 4 line to-16 line decoders required to make an 8-line-to-256 line decoder is
Correct answer is '17'. Can you explain this answer?
The number of 4 line to-16 line decoders required to make an 8-line-to-256 line decoder is
|
|
Asha Sharma answered |
8-line to-256-line decoder using 4-line to-16-line decoders is shown below:
Number of 4 x 16 MUX required

Number of 4 x 16 MUX required
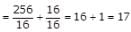
|
|
Naina Shah asked • Dec 08, 2019 |
Consider the translation scheme shown below:

Here num is a token that represents an integer and num.val represents the corresponding integer value. For an input string ‘9 + 5 + 2’, this translation scheme will print- a)9 + 5 + 2
- b)9 5 + 2 +
- c)9 5 2 + +
- d)+ + 9 5 2
Correct answer is option 'B'. Can you explain this answer?
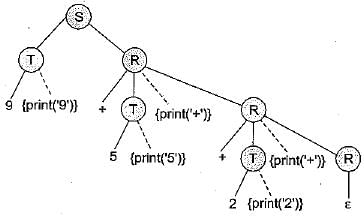
Consider the translation scheme shown below:

Here num is a token that represents an integer and num.val represents the corresponding integer value. For an input string ‘9 + 5 + 2’, this translation scheme will print

Here num is a token that represents an integer and num.val represents the corresponding integer value. For an input string ‘9 + 5 + 2’, this translation scheme will print
a)
9 + 5 + 2
b)
9 5 + 2 +
c)
9 5 2 + +
d)
+ + 9 5 2
|
|
Aditya Nair answered |
For the input ‘9 + 5 + 2’ the translation scheme is 95 + 2 + shown below:

|
|
Naina Shah asked • Nov 26, 2019 |
Which of the following languages are regular over ∑ = {a, b}?
L1 = { anbn | 0 < n ≤ 10}
L2 = { a2n | n ≥ 1}
L3 = { an! | n > 0}- a)L2 only.
- b)L1 only.
- c)L1 and L2.
- d)None of L1, L2 and L3.
Correct answer is option 'C'. Can you explain this answer?
Which of the following languages are regular over ∑ = {a, b}?
L1 = { anbn | 0 < n ≤ 10}
L2 = { a2n | n ≥ 1}
L3 = { an! | n > 0}
L1 = { anbn | 0 < n ≤ 10}
L2 = { a2n | n ≥ 1}
L3 = { an! | n > 0}
a)
L2 only.
b)
L1 only.
c)
L1 and L2.
d)
None of L1, L2 and L3.
|
|
Ravi Singh answered |
Any language for which we have a finite set or we can possibly have a DFA drawn for it is regular. L1: It gives a finite set generating string with equal number of a’s and equal number of b’s for range 0
Hence L2 is also regular. L3: It gives all possible strings with a’s such that number of a’s are in factorial values of 1,2,3,4 ……. i.e. {a1, a2, a6, a24 ……………}. The set is neither finite nor a DFA is possible for such set. Hence L3 is not regular.
Fetching relevant content for you






















