All Exams >
Computer Science Engineering (CSE) >
6 Months Preparation for GATE CSE >
All Questions
All questions of Machine Instructions & Addressing Modes for Computer Science Engineering (CSE) Exam
The computer architecture aimed at reducing the time of execution of instructions is ________- a)CISC
- b)RISC
- c)ISA
- d)ANNA
Correct answer is option 'B'. Can you explain this answer?
The computer architecture aimed at reducing the time of execution of instructions is ________
a)
CISC
b)
RISC
c)
ISA
d)
ANNA
|
|
Sanya Agarwal answered |
Answer: b
Explanation: The RISC stands for Reduced Instruction Set Computer.
Explanation: The RISC stands for Reduced Instruction Set Computer.
Which of the architecture is power efficient?- a)CISC
- b)RISC
- c)ISA
- d)IANA
Correct answer is option 'B'. Can you explain this answer?
Which of the architecture is power efficient?
a)
CISC
b)
RISC
c)
ISA
d)
IANA
|
|
Sanya Agarwal answered |
Answer: b
Explanation: Hence the RISC architecture is followed in the design of mobile devices.
Explanation: Hence the RISC architecture is followed in the design of mobile devices.
Consider a three word machine instructionADD A[R0], @BThe first operand (destination) “A[R0]” uses indexed addressing mode with R0 as the index register. The second operand(source) “@B” uses indirect addressing mode. A and B are memory addresses residing at the second and third words,respectively. The first word of the instruction specifies the opcode, the index register designation and the source anddestination addressing modes. During execution of ADD instruction, the two operands are added and stored in thedestination (first operand).The number of memory cycles needed during the execution cycle of the instruction is:- a)3
- b)4
- c)5
- d)6
Correct answer is option 'B'. Can you explain this answer?
Consider a three word machine instruction
ADD A[R0], @B
The first operand (destination) “A[R0]” uses indexed addressing mode with R0 as the index register. The second operand(source) “@B” uses indirect addressing mode. A and B are memory addresses residing at the second and third words,respectively. The first word of the instruction specifies the opcode, the index register designation and the source anddestination addressing modes. During execution of ADD instruction, the two operands are added and stored in thedestination (first operand).
The number of memory cycles needed during the execution cycle of the instruction is:
a)
3
b)
4
c)
5
d)
6
|
|
Neha Choudhury answered |
In Indexed addressing mode, the base address is already in the instruction i.e A and to fetch the index data from R0 no memory access is required because it’s a register. So, to fetch the operand only 1 memory cycle is required.
Indirect Addressing mode requires 2 memory cycles only.
When we use auto increment or auto decrements, which of the following is/are true?
1) In both, the address is used to retrieve the operand and then the address gets altered
2) In auto increment the operand is retrieved first and then the address altered
3) Both of them can be used on general purpose registers as well as memory locations- a)1, 2, 3
- b)2
- c)1, 3
- d)2, 3
Correct answer is option 'D'. Can you explain this answer?
When we use auto increment or auto decrements, which of the following is/are true?
1) In both, the address is used to retrieve the operand and then the address gets altered
2) In auto increment the operand is retrieved first and then the address altered
3) Both of them can be used on general purpose registers as well as memory locations
1) In both, the address is used to retrieve the operand and then the address gets altered
2) In auto increment the operand is retrieved first and then the address altered
3) Both of them can be used on general purpose registers as well as memory locations
a)
1, 2, 3
b)
2
c)
1, 3
d)
2, 3
|
|
Yash Patel answered |
In the case of, auto increment the increment is done afterward and in auto decrement the decrement is done first.
The correct matching for the following pairs is:
(A) DMA I/O (1) High speed RAM
(B) Cache (2) Disk
(C) Interrupt I/O (3) Printer
(D) Condition Code Register (4) ALU
- a)A-4 B-3 C-1 D-2
- b)A-2 B-1 C-3 D-4
- c)A-4 B-3 C-2 D-1
- d)A-2 B-3 C-4 D-1
Correct answer is option 'B'. Can you explain this answer?
The correct matching for the following pairs is:
(A) DMA I/O (1) High speed RAM
(B) Cache (2) Disk
(C) Interrupt I/O (3) Printer
(D) Condition Code Register (4) ALU
(A) DMA I/O (1) High speed RAM
(B) Cache (2) Disk
(C) Interrupt I/O (3) Printer
(D) Condition Code Register (4) ALU
a)
A-4 B-3 C-1 D-2
b)
A-2 B-1 C-3 D-4
c)
A-4 B-3 C-2 D-1
d)
A-2 B-3 C-4 D-1

|
Machine Experts answered |
Explanation:
- DMA I/O (1) High speed RAM: DMA (Direct Memory Access) is used for transferring data between peripherals and memory without involving the CPU. It is commonly used for high-speed data transfers to and from high-speed RAM.
- Cache (2) Disk: Cache memory is a small, fast type of volatile computer memory used to temporarily store data that is frequently accessed. It helps in reducing the access time to data stored on slower storage devices like disks.
- Interrupt I/O (3) Printer: Interrupt I/O involves the use of interrupts to signal the CPU that a peripheral device needs attention. This is commonly used for devices like printers where the CPU needs to be informed when data is ready to be printed.
- Condition Code Register (4) ALU: The Condition Code Register (CCR) is a register used to store the condition codes generated by the ALU (Arithmetic Logic Unit) during arithmetic and logical operations. These codes are used to determine the outcome of operations and make decisions based on them.
- DMA I/O (1) High speed RAM: DMA (Direct Memory Access) is used for transferring data between peripherals and memory without involving the CPU. It is commonly used for high-speed data transfers to and from high-speed RAM.
- Cache (2) Disk: Cache memory is a small, fast type of volatile computer memory used to temporarily store data that is frequently accessed. It helps in reducing the access time to data stored on slower storage devices like disks.
- Interrupt I/O (3) Printer: Interrupt I/O involves the use of interrupts to signal the CPU that a peripheral device needs attention. This is commonly used for devices like printers where the CPU needs to be informed when data is ready to be printed.
- Condition Code Register (4) ALU: The Condition Code Register (CCR) is a register used to store the condition codes generated by the ALU (Arithmetic Logic Unit) during arithmetic and logical operations. These codes are used to determine the outcome of operations and make decisions based on them.
What does VLIW stands for?- a)Very Long Instruction Width
- b)Very Large Instruction Word
- c)Very Long Instruction Word
- d)None of the above
Correct answer is option 'C'. Can you explain this answer?
What does VLIW stands for?
a)
Very Long Instruction Width
b)
Very Large Instruction Word
c)
Very Long Instruction Word
d)
None of the above
|
|
Sudhir Patel answered |
It is the architecture designed to perform multiple operations in parallel.
In IA-32 architecture along with the general flags, which of the following conditional flags are provided?- a)TF
- b)IOPL
- c)IF
- d)All of the mentioned
Correct answer is option 'D'. Can you explain this answer?
In IA-32 architecture along with the general flags, which of the following conditional flags are provided?
a)
TF
b)
IOPL
c)
IF
d)
All of the mentioned
|
|
Milan Rane answered |
Conditional flags in IA-32 architecture
The IA-32 architecture, also known as the x86 architecture, is a widely used computer architecture that forms the basis for most of the modern desktop and server processors. In addition to the general flags, which are used for various purposes, there are several conditional flags provided in the IA-32 architecture.
1. TF (Trap Flag)
The TF flag is a conditional flag that controls the operation of the processor's single-step mode. When the TF flag is set, the processor operates in single-step mode, which means that it executes one instruction at a time and then generates an interrupt. This is commonly used for debugging purposes, allowing developers to step through their code and examine the state of the processor at each step.
2. IOPL (I/O Privilege Level)
The IOPL flag is a conditional flag that determines the privilege level at which I/O operations can be performed. It has two bits, which can be set to either 0, 1, 2, or 3. The IOPL flag is used in conjunction with the IOPL field in the EFLAGS register to control access to I/O instructions. Higher privilege levels (larger IOPL values) have more access to I/O instructions, while lower privilege levels have restricted access.
3. IF (Interrupt Flag)
The IF flag is a conditional flag that controls the generation of interrupts. When the IF flag is set, interrupts are enabled, and the processor can respond to external interrupts. On the other hand, when the IF flag is cleared, interrupts are disabled, and the processor ignores external interrupts. The IF flag is often used to control the handling of interrupts in a system.
Conclusion
In the IA-32 architecture, along with the general flags, which are used for various purposes, the conditional flags provided include the TF (Trap Flag), IOPL (I/O Privilege Level), and IF (Interrupt Flag). These flags play a crucial role in controlling the behavior of the processor, such as enabling single-step mode, managing I/O privilege levels, and controlling the generation of interrupts.
The IA-32 architecture, also known as the x86 architecture, is a widely used computer architecture that forms the basis for most of the modern desktop and server processors. In addition to the general flags, which are used for various purposes, there are several conditional flags provided in the IA-32 architecture.
1. TF (Trap Flag)
The TF flag is a conditional flag that controls the operation of the processor's single-step mode. When the TF flag is set, the processor operates in single-step mode, which means that it executes one instruction at a time and then generates an interrupt. This is commonly used for debugging purposes, allowing developers to step through their code and examine the state of the processor at each step.
2. IOPL (I/O Privilege Level)
The IOPL flag is a conditional flag that determines the privilege level at which I/O operations can be performed. It has two bits, which can be set to either 0, 1, 2, or 3. The IOPL flag is used in conjunction with the IOPL field in the EFLAGS register to control access to I/O instructions. Higher privilege levels (larger IOPL values) have more access to I/O instructions, while lower privilege levels have restricted access.
3. IF (Interrupt Flag)
The IF flag is a conditional flag that controls the generation of interrupts. When the IF flag is set, interrupts are enabled, and the processor can respond to external interrupts. On the other hand, when the IF flag is cleared, interrupts are disabled, and the processor ignores external interrupts. The IF flag is often used to control the handling of interrupts in a system.
Conclusion
In the IA-32 architecture, along with the general flags, which are used for various purposes, the conditional flags provided include the TF (Trap Flag), IOPL (I/O Privilege Level), and IF (Interrupt Flag). These flags play a crucial role in controlling the behavior of the processor, such as enabling single-step mode, managing I/O privilege levels, and controlling the generation of interrupts.
________ are the different type/s of generating control signals.- a)Hardwired
- b)Micro-instruction
- c)Micro-programmed
- d)Both Micro-programmed and Hardwired
Correct answer is option 'D'. Can you explain this answer?
________ are the different type/s of generating control signals.
a)
Hardwired
b)
Micro-instruction
c)
Micro-programmed
d)
Both Micro-programmed and Hardwired
|
|
Amar Majumdar answered |
Generating Control Signals
There are different types of generating control signals, which are as follows:
1. Hardwired Control Signals:
Hardwired control signals are generated by using the combinational logic circuits. These circuits are designed using logic gates, such as AND, OR, NOT gates, etc. The control signals generated by these circuits are directly applied to the control unit.
2. Micro-instruction Control Signals:
Micro-instruction control signals are generated by using micro-instructions. These micro-instructions are stored in the control memory. The control unit reads these micro-instructions and generates the control signals accordingly.
3. Micro-programmed Control Signals:
Micro-programmed control signals are generated by using micro-programs. Micro-programs are stored in the control memory. These programs are written in machine language and are executed by the control unit. The control unit reads these programs and generates the control signals accordingly.
Both Micro-programmed and Hardwired:
Both micro-programmed and hardwired control signals are used in modern computing systems. Some control signals are generated by using combinational logic circuits, while others are generated by using micro-instructions or micro-programs.
Conclusion:
In conclusion, generating control signals is an important aspect of computer architecture. The choice of control signal generation method depends on the specific requirements of the system. Hardwired, micro-instruction, and micro-programmed control signals are the different types of generating control signals.
There are different types of generating control signals, which are as follows:
1. Hardwired Control Signals:
Hardwired control signals are generated by using the combinational logic circuits. These circuits are designed using logic gates, such as AND, OR, NOT gates, etc. The control signals generated by these circuits are directly applied to the control unit.
2. Micro-instruction Control Signals:
Micro-instruction control signals are generated by using micro-instructions. These micro-instructions are stored in the control memory. The control unit reads these micro-instructions and generates the control signals accordingly.
3. Micro-programmed Control Signals:
Micro-programmed control signals are generated by using micro-programs. Micro-programs are stored in the control memory. These programs are written in machine language and are executed by the control unit. The control unit reads these programs and generates the control signals accordingly.
Both Micro-programmed and Hardwired:
Both micro-programmed and hardwired control signals are used in modern computing systems. Some control signals are generated by using combinational logic circuits, while others are generated by using micro-instructions or micro-programs.
Conclusion:
In conclusion, generating control signals is an important aspect of computer architecture. The choice of control signal generation method depends on the specific requirements of the system. Hardwired, micro-instruction, and micro-programmed control signals are the different types of generating control signals.
Addressing mode is ______.- a)Explicitly specified
- b)Implied by the instruction
- c)Both (a) and (b)
- d)Neither (a) nor (b)
Correct answer is option 'C'. Can you explain this answer?
Addressing mode is ______.
a)
Explicitly specified
b)
Implied by the instruction
c)
Both (a) and (b)
d)
Neither (a) nor (b)
|
|
Tejas Ghoshal answered |
Addressing modes are either explicitly specified or implied by the instruction.
Out of the following which is not a CISC machine.- a)IBM 370/168
- b)VAX 11/780
- c)Intel 80486
- d)Motorola A567
Correct answer is option 'D'. Can you explain this answer?
Out of the following which is not a CISC machine.
a)
IBM 370/168
b)
VAX 11/780
c)
Intel 80486
d)
Motorola A567
|
|
Shanaya Chopra answered |
CISC Machines
CISC stands for Complex Instruction Set Computing. A CISC machine has a large set of complex instructions that can perform a variety of tasks in a single instruction. Some of the popular CISC machines are IBM 370/168, VAX 11/780, and Intel 80486.
Explanation
Among the given options, only the Motorola A567 is not a CISC machine. Motorola A567 is a RISC (Reduced Instruction Set Computing) machine. RISC machines have a smaller instruction set and each instruction performs a simple operation. RISC machines require more instructions to perform complex tasks than CISC machines.
Conclusion
In conclusion, the correct answer is option 'D' because Motorola A567 is not a CISC machine.
CISC stands for Complex Instruction Set Computing. A CISC machine has a large set of complex instructions that can perform a variety of tasks in a single instruction. Some of the popular CISC machines are IBM 370/168, VAX 11/780, and Intel 80486.
Explanation
Among the given options, only the Motorola A567 is not a CISC machine. Motorola A567 is a RISC (Reduced Instruction Set Computing) machine. RISC machines have a smaller instruction set and each instruction performs a simple operation. RISC machines require more instructions to perform complex tasks than CISC machines.
Conclusion
In conclusion, the correct answer is option 'D' because Motorola A567 is not a CISC machine.
Which of the following addressing modes permits relocation without any change whatsoever in the code?
- a)Indirect addressing
- b)Indexed addressing
- c)PC relative addressing
- d)PC relative addressing
Correct answer is option 'D'. Can you explain this answer?
Which of the following addressing modes permits relocation without any change whatsoever in the code?
a)
Indirect addressing
b)
Indexed addressing
c)
PC relative addressing
d)
PC relative addressing

|
Swara Dasgupta answered |
PC relative addressing mode:
The effective memory address is obtained by computing an offset from the current PC. No matter where the code is loaded in memory, the offsets are always the same so the code needs no modification. In this addressing, there is absolutely no change in code needed.
Therefore the answer is Option 4 i.e, PC relative Addressing
System calls are usually invoked by using
1. An indirect jump
2. A software interrupt
3. Polling
4. A privileged instruction- a)2 and 3
- b)1 and 3
- c)1, 2, 3 and 4
- d)3 and 4
Correct answer is option 'A'. Can you explain this answer?
System calls are usually invoked by using
1. An indirect jump
2. A software interrupt
3. Polling
4. A privileged instruction
1. An indirect jump
2. A software interrupt
3. Polling
4. A privileged instruction
a)
2 and 3
b)
1 and 3
c)
1, 2, 3 and 4
d)
3 and 4
|
|
Harshitha Banerjee answered |
System call is a request in unit like operating system made via software interrupt by an active process for a service performed by the Kernal.
The CISC stands for ___________- a)Computer Instruction Set Compliment
- b)Complete Instruction Set Compliment
- c)Computer Indexed Set Components
- d)Complex Instruction set computer
Correct answer is option 'D'. Can you explain this answer?
The CISC stands for ___________
a)
Computer Instruction Set Compliment
b)
Complete Instruction Set Compliment
c)
Computer Indexed Set Components
d)
Complex Instruction set computer
|
|
Rishabh Sharma answered |
Answer: d
Explanation: CISC is an computer architecture where in the processor performs more complex operations in one step.
Explanation: CISC is an computer architecture where in the processor performs more complex operations in one step.
What is computer architecture?- a)set of categories and methods that specify the functioning, organisation, and implementation of computer systems
- b)set of principles and methods that specify the functioning, organisation, and implementation of computer systems
- c)set of functions and methods that specify the functioning, organisation, and implementation of computer systems
- d)None of the mentioned
Correct answer is option 'B'. Can you explain this answer?
What is computer architecture?
a)
set of categories and methods that specify the functioning, organisation, and implementation of computer systems
b)
set of principles and methods that specify the functioning, organisation, and implementation of computer systems
c)
set of functions and methods that specify the functioning, organisation, and implementation of computer systems
d)
None of the mentioned
|
|
Rohan Patel answered |
Computer architecture refers to the set of principles and methods that specify the functioning, organization, and implementation of computer systems. It encompasses the structure, behavior, and design of computers, including the hardware components and the software systems that control and coordinate their operation.
Key Points:
- Set of principles and methods: Computer architecture defines the fundamental principles and techniques for designing and implementing computer systems. It provides a framework for understanding how different components of a computer system interact and work together.
- Functioning: Computer architecture determines how the various components of a computer system, such as the CPU, memory, and input/output devices, function and interact with each other. It specifies the operations and functionalities that can be performed by the system.
- Organization: Computer architecture involves the organization and arrangement of the components within a computer system. It defines the structure and hierarchy of the various hardware components and their connections, as well as the organization of data and instructions in memory.
- Implementation: Computer architecture also deals with the implementation of computer systems, including the design and construction of the hardware components and the development of the software systems that run on them. It encompasses both the physical aspects of computer systems, such as the circuits and chips, as well as the software layers that enable their operation.
Importance of Computer Architecture:
- Performance: Computer architecture plays a crucial role in determining the performance of a computer system. By optimizing the design and organization of the components, it can enhance the speed and efficiency of computations and data processing.
- Scalability: Computer architecture also enables the scalability of computer systems, allowing them to handle larger workloads and accommodate future technological advancements. It provides a foundation for building systems that can be easily upgraded and expanded.
- Compatibility: Computer architecture ensures compatibility between different hardware and software components, allowing them to work together seamlessly. It defines standard interfaces and protocols that enable interoperability and easy integration of various system components.
- Reliability: A well-designed computer architecture enhances the reliability and fault tolerance of a system. By incorporating redundancy and error detection mechanisms, it can prevent and recover from hardware and software failures.
- Power Efficiency: Computer architecture also considers power efficiency and energy consumption. It aims to minimize power usage while maintaining optimal performance, especially in mobile and embedded systems.
In conclusion, computer architecture is a set of principles and methods that define the functioning, organization, and implementation of computer systems. It provides the foundation for designing and building efficient, scalable, and reliable computer systems.
Key Points:
- Set of principles and methods: Computer architecture defines the fundamental principles and techniques for designing and implementing computer systems. It provides a framework for understanding how different components of a computer system interact and work together.
- Functioning: Computer architecture determines how the various components of a computer system, such as the CPU, memory, and input/output devices, function and interact with each other. It specifies the operations and functionalities that can be performed by the system.
- Organization: Computer architecture involves the organization and arrangement of the components within a computer system. It defines the structure and hierarchy of the various hardware components and their connections, as well as the organization of data and instructions in memory.
- Implementation: Computer architecture also deals with the implementation of computer systems, including the design and construction of the hardware components and the development of the software systems that run on them. It encompasses both the physical aspects of computer systems, such as the circuits and chips, as well as the software layers that enable their operation.
Importance of Computer Architecture:
- Performance: Computer architecture plays a crucial role in determining the performance of a computer system. By optimizing the design and organization of the components, it can enhance the speed and efficiency of computations and data processing.
- Scalability: Computer architecture also enables the scalability of computer systems, allowing them to handle larger workloads and accommodate future technological advancements. It provides a foundation for building systems that can be easily upgraded and expanded.
- Compatibility: Computer architecture ensures compatibility between different hardware and software components, allowing them to work together seamlessly. It defines standard interfaces and protocols that enable interoperability and easy integration of various system components.
- Reliability: A well-designed computer architecture enhances the reliability and fault tolerance of a system. By incorporating redundancy and error detection mechanisms, it can prevent and recover from hardware and software failures.
- Power Efficiency: Computer architecture also considers power efficiency and energy consumption. It aims to minimize power usage while maintaining optimal performance, especially in mobile and embedded systems.
In conclusion, computer architecture is a set of principles and methods that define the functioning, organization, and implementation of computer systems. It provides the foundation for designing and building efficient, scalable, and reliable computer systems.
In four-address instruction format, the number of bytes required to encode an instruction is (assume each address requires 24 bits, and 1 byte is required for operation code)- a)9
- b)13
- c)14
- d)12
Correct answer is option 'B'. Can you explain this answer?
In four-address instruction format, the number of bytes required to encode an instruction is (assume each address requires 24 bits, and 1 byte is required for operation code)
a)
9
b)
13
c)
14
d)
12
|
|
Mahi Yadav answered |
Four address instruction format:
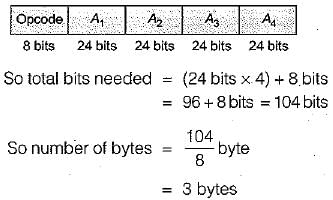

Which of the following architecture is suitable for a wide range of data types?- a)IA-32
- b)ARM
- c)ASUS firebird
- d)68000
Correct answer is option 'A'. Can you explain this answer?
Which of the following architecture is suitable for a wide range of data types?
a)
IA-32
b)
ARM
c)
ASUS firebird
d)
68000
|
|
Alok Desai answered |
IA-32 architecture
The IA-32 architecture, also known as x86, is a widely used architecture for microprocessors. It is developed by Intel and has been in use since the 1980s. The IA-32 architecture is suitable for a wide range of data types due to its versatility and compatibility with various software applications.
Key features:
1. Variable-length instruction set: The IA-32 architecture supports variable-length instructions, which allows for efficient encoding of instructions for different data types.
2. Large addressable memory: IA-32 processors can access a large amount of memory, allowing for efficient handling of different data types and large datasets.
3. General-purpose registers: IA-32 architecture provides a set of general-purpose registers that can be used for storing and manipulating different data types.
4. Support for different data formats: IA-32 architecture supports various data formats, including integers, floating-point numbers, and character data. It provides instructions for performing arithmetic, logical, and data conversion operations on these data types.
5. Instruction set extensions: Over the years, Intel has introduced several instruction set extensions to the IA-32 architecture, such as SSE (Streaming SIMD Extensions) and AVX (Advanced Vector Extensions). These extensions provide additional instructions and capabilities for handling specialized data types, such as multimedia and vector data.
Advantages:
- Compatibility: The IA-32 architecture is widely supported by operating systems, compilers, and software applications, making it easy to develop and run programs on IA-32 processors.
- Performance: IA-32 processors are known for their high-performance capabilities, especially in tasks that involve intensive data processing. They have a large number of instructions optimized for different data types, allowing for efficient execution of diverse computational tasks.
- Wide range of software libraries: Due to the popularity of IA-32 architecture, there are numerous software libraries and frameworks available that are optimized for this architecture. This makes it easier to utilize existing software components and libraries for different data types.
Conclusion:
The IA-32 architecture is suitable for a wide range of data types due to its versatility, compatibility, and support for various data formats. Its variable-length instruction set, large addressable memory, and extensive instruction set extensions make it a suitable choice for handling diverse data types and performing complex computations.
The IA-32 architecture, also known as x86, is a widely used architecture for microprocessors. It is developed by Intel and has been in use since the 1980s. The IA-32 architecture is suitable for a wide range of data types due to its versatility and compatibility with various software applications.
Key features:
1. Variable-length instruction set: The IA-32 architecture supports variable-length instructions, which allows for efficient encoding of instructions for different data types.
2. Large addressable memory: IA-32 processors can access a large amount of memory, allowing for efficient handling of different data types and large datasets.
3. General-purpose registers: IA-32 architecture provides a set of general-purpose registers that can be used for storing and manipulating different data types.
4. Support for different data formats: IA-32 architecture supports various data formats, including integers, floating-point numbers, and character data. It provides instructions for performing arithmetic, logical, and data conversion operations on these data types.
5. Instruction set extensions: Over the years, Intel has introduced several instruction set extensions to the IA-32 architecture, such as SSE (Streaming SIMD Extensions) and AVX (Advanced Vector Extensions). These extensions provide additional instructions and capabilities for handling specialized data types, such as multimedia and vector data.
Advantages:
- Compatibility: The IA-32 architecture is widely supported by operating systems, compilers, and software applications, making it easy to develop and run programs on IA-32 processors.
- Performance: IA-32 processors are known for their high-performance capabilities, especially in tasks that involve intensive data processing. They have a large number of instructions optimized for different data types, allowing for efficient execution of diverse computational tasks.
- Wide range of software libraries: Due to the popularity of IA-32 architecture, there are numerous software libraries and frameworks available that are optimized for this architecture. This makes it easier to utilize existing software components and libraries for different data types.
Conclusion:
The IA-32 architecture is suitable for a wide range of data types due to its versatility, compatibility, and support for various data formats. Its variable-length instruction set, large addressable memory, and extensive instruction set extensions make it a suitable choice for handling diverse data types and performing complex computations.
The VLIW architecture follows _____ approach to achieve parallelism.- a)SISD
- b)MIMD
- c)MISD
- d)SIMD
Correct answer is option 'B'. Can you explain this answer?
The VLIW architecture follows _____ approach to achieve parallelism.
a)
SISD
b)
MIMD
c)
MISD
d)
SIMD
|
|
Mrinalini Menon answered |
Explanation:
VLIW Architecture and Parallelism:
VLIW (Very Long Instruction Word) architecture is designed to achieve parallelism by packing multiple operations into a single instruction word. By doing so, VLIW processors can execute these operations simultaneously without the need for complex hardware to detect dependencies between instructions.
Approach to Achieve Parallelism:
MIMD (Multiple Instruction, Multiple Data) is the approach followed by VLIW architecture to achieve parallelism. In MIMD architecture, multiple processors or processing elements execute different instructions on different sets of data simultaneously. Each processing element operates independently, allowing for true parallelism in task execution.
Comparison with other Architectures:
- SISD (Single Instruction, Single Data): In SISD architecture, a single processor executes a single instruction on a single piece of data at a time, lacking parallelism.
- MISD (Multiple Instruction, Single Data): In MISD architecture, multiple processors execute different instructions on the same data stream, which is not commonly used due to limited practical applications.
- SIMD (Single Instruction, Multiple Data): In SIMD architecture, a single instruction is executed on multiple pieces of data simultaneously, which is different from VLIW's approach of packing multiple operations in a single instruction word.
Conclusion:
Overall, VLIW architecture's MIMD approach allows for efficient utilization of resources and high levels of parallelism, making it suitable for tasks that require multiple operations to be executed concurrently.
Relative mode of addressing is most relevant to writing- a)Co-routines
- b)Position – independent code
- c)Shareable code
- d)Interrupt Handlers
Correct answer is option 'B'. Can you explain this answer?
Relative mode of addressing is most relevant to writing
a)
Co-routines
b)
Position – independent code
c)
Shareable code
d)
Interrupt Handlers
|
|
Pranab Banerjee answered |
Answer: B
Relative mode addressing is most relevant to writing a position-independent code.
Relative mode addressing is most relevant to writing a position-independent code.
Which of the following is the subcategories of computer architecture?
- a)All of the mentioned
- b)Instruction set architecture
- c)Systems design
- d)Microarchitecture
Correct answer is option 'A'. Can you explain this answer?
Which of the following is the subcategories of computer architecture?
a)
All of the mentioned
b)
Instruction set architecture
c)
Systems design
d)
Microarchitecture
|
|
Rohan Patel answered |
Introduction:
Computer architecture refers to the design and organization of the various components (hardware and software) in a computer system. It encompasses the structure, behavior, and functionality of a computer system. There are several subcategories of computer architecture that focus on different aspects of the design and implementation of a computer system.
Microarchitecture:
Microarchitecture, also known as computer organization, is a subcategory of computer architecture that deals with the internal structure and design of a computer processor. It focuses on how the processor implements the instructions specified by the instruction set architecture. Microarchitecture includes components such as the control unit, arithmetic logic unit, memory hierarchy, and data paths.
Instruction Set Architecture:
Instruction Set Architecture (ISA) is another subcategory of computer architecture. It defines the set of instructions that a computer can understand and execute. It specifies the operations that can be performed, the data types supported, the addressing modes, and the format of instructions. The ISA acts as an interface between the hardware and software layers of a computer system.
Systems Design:
Systems design is a broader subcategory of computer architecture that encompasses the overall design and organization of a computer system. It includes considerations such as the selection of hardware components, the design of the memory hierarchy, the interconnection of components, and the configuration of the system. Systems design takes into account factors such as performance, reliability, scalability, and cost.
Conclusion:
In summary, microarchitecture, instruction set architecture, and systems design are all subcategories of computer architecture. Microarchitecture focuses on the internal structure of a computer processor, instruction set architecture defines the instructions that a computer can understand, and systems design encompasses the overall design and organization of a computer system.
Computer architecture refers to the design and organization of the various components (hardware and software) in a computer system. It encompasses the structure, behavior, and functionality of a computer system. There are several subcategories of computer architecture that focus on different aspects of the design and implementation of a computer system.
Microarchitecture:
Microarchitecture, also known as computer organization, is a subcategory of computer architecture that deals with the internal structure and design of a computer processor. It focuses on how the processor implements the instructions specified by the instruction set architecture. Microarchitecture includes components such as the control unit, arithmetic logic unit, memory hierarchy, and data paths.
Instruction Set Architecture:
Instruction Set Architecture (ISA) is another subcategory of computer architecture. It defines the set of instructions that a computer can understand and execute. It specifies the operations that can be performed, the data types supported, the addressing modes, and the format of instructions. The ISA acts as an interface between the hardware and software layers of a computer system.
Systems Design:
Systems design is a broader subcategory of computer architecture that encompasses the overall design and organization of a computer system. It includes considerations such as the selection of hardware components, the design of the memory hierarchy, the interconnection of components, and the configuration of the system. Systems design takes into account factors such as performance, reliability, scalability, and cost.
Conclusion:
In summary, microarchitecture, instruction set architecture, and systems design are all subcategories of computer architecture. Microarchitecture focuses on the internal structure of a computer processor, instruction set architecture defines the instructions that a computer can understand, and systems design encompasses the overall design and organization of a computer system.
To reduce the memory access time we generally make use of ______- a)SDRAM’s
- b)Heaps
- c)Cache’s
- d)Higher capacity RAM’s
Correct answer is option 'C'. Can you explain this answer?
To reduce the memory access time we generally make use of ______
a)
SDRAM’s
b)
Heaps
c)
Cache’s
d)
Higher capacity RAM’s
|
|
Sudhir Patel answered |
The time required to access a part of the memory for data retrieval.
The most appropriate matching for the following pairs
X: Indirect addressing 1: Loops
Y: Immediate addressing 2: Pointers
Z: Auto decrement addressing 3: Constantsis- a)X - 3 Y - 2 Z - 1
- b)X - 1 Y - 3 Z - 2
- c)X - 2 Y - 3 Z - 1
- d)X - 3 Y - 1 Z - 2
Correct answer is option 'C'. Can you explain this answer?
The most appropriate matching for the following pairs
X: Indirect addressing 1: Loops
Y: Immediate addressing 2: Pointers
Z: Auto decrement addressing 3: Constantsis
X: Indirect addressing 1: Loops
Y: Immediate addressing 2: Pointers
Z: Auto decrement addressing 3: Constantsis
a)
X - 3 Y - 2 Z - 1
b)
X - 1 Y - 3 Z - 2
c)
X - 2 Y - 3 Z - 1
d)
X - 3 Y - 1 Z - 2
|
|
Rashi Singh answered |
Explanation:
To determine the correct matching for the given pairs, let's understand the concepts of indirect addressing, immediate addressing, and auto decrement addressing.
Indirect Addressing:
In indirect addressing, the address of the operand is specified by a register or a memory location. It involves accessing the operand indirectly through an intermediate address. It is commonly used for accessing data structures like arrays and linked lists.
Immediate Addressing:
In immediate addressing, the operand itself is specified in the instruction. It means that the data to be operated on is directly given as a constant value in the instruction itself.
Auto Decrement Addressing:
In auto decrement addressing, the address of the operand is decremented automatically after each access. It is often used in stack operations where the top of the stack pointer is decremented after each pop operation.
Now, let's match the given pairs with their corresponding addressing modes:
X: Indirect addressing
Indirect addressing involves accessing the operand indirectly through an intermediate address. It is similar to accessing data structures like arrays and linked lists. Therefore, X matches with 2: Pointers.
Y: Immediate addressing
Immediate addressing means that the operand itself is specified in the instruction. It is directly given as a constant value in the instruction. Therefore, Y matches with 3: Constants.
Z: Auto decrement addressing
Auto decrement addressing involves automatically decrementing the address of the operand after each access. It is commonly used in stack operations. Therefore, Z matches with 1: Loops.
Correct matching:
X - 2
Y - 3
Z - 1
Therefore, the correct matching for the given pairs is option 'C':
X - 2
Y - 3
Z - 1
To determine the correct matching for the given pairs, let's understand the concepts of indirect addressing, immediate addressing, and auto decrement addressing.
Indirect Addressing:
In indirect addressing, the address of the operand is specified by a register or a memory location. It involves accessing the operand indirectly through an intermediate address. It is commonly used for accessing data structures like arrays and linked lists.
Immediate Addressing:
In immediate addressing, the operand itself is specified in the instruction. It means that the data to be operated on is directly given as a constant value in the instruction itself.
Auto Decrement Addressing:
In auto decrement addressing, the address of the operand is decremented automatically after each access. It is often used in stack operations where the top of the stack pointer is decremented after each pop operation.
Now, let's match the given pairs with their corresponding addressing modes:
X: Indirect addressing
Indirect addressing involves accessing the operand indirectly through an intermediate address. It is similar to accessing data structures like arrays and linked lists. Therefore, X matches with 2: Pointers.
Y: Immediate addressing
Immediate addressing means that the operand itself is specified in the instruction. It is directly given as a constant value in the instruction. Therefore, Y matches with 3: Constants.
Z: Auto decrement addressing
Auto decrement addressing involves automatically decrementing the address of the operand after each access. It is commonly used in stack operations. Therefore, Z matches with 1: Loops.
Correct matching:
X - 2
Y - 3
Z - 1
Therefore, the correct matching for the given pairs is option 'C':
X - 2
Y - 3
Z - 1
The iconic feature of the RISC machine among the following are- a)Reduced number of addressing modes
- b)Increased memory size
- c)Having a branch delay slot
- d)All of the mentioned
Correct answer is option 'C'. Can you explain this answer?
The iconic feature of the RISC machine among the following are
a)
Reduced number of addressing modes
b)
Increased memory size
c)
Having a branch delay slot
d)
All of the mentioned
|
|
Prashanth Patel answered |
Answer: c
Explanation: A branch delay slot is an instruction space immediately following a jump or branch.
Explanation: A branch delay slot is an instruction space immediately following a jump or branch.
Pipe-lining is a unique feature of _______- a)RISC
- b)CISC
- c)ISA
- d)IANA
Correct answer is option 'A'. Can you explain this answer?
Pipe-lining is a unique feature of _______
a)
RISC
b)
CISC
c)
ISA
d)
IANA
|
|
Ayush Basu answered |
- The RISC machine architecture was the first to implement pipe-lining.
- A Reduced Instruction Set Computer is a type of microprocessor architecture that utilizes a small, highly-optimized set of instructions rather than the highly-specialized set of instructions typically found in other architectures.
- RISC is an alternative to the Complex Instruction Set Computing (CISC) architecture and is often considered the most efficient CPU architecture technology available today.
Hence, the correct answer is Option A
You can attempt more such questions by going through the link:
Microinstruction length is determined by _____.
1. The maximum number of simultaneous micro operations that must be specified.
2. The way in which the control information is represented or encoded.
3. The way in which the next microinstruction address is specified.- a)1 and 2
- b)2 and 3
- c)1 and 3
- d)All of these
Correct answer is option 'D'. Can you explain this answer?
Microinstruction length is determined by _____.
1. The maximum number of simultaneous micro operations that must be specified.
2. The way in which the control information is represented or encoded.
3. The way in which the next microinstruction address is specified.
1. The maximum number of simultaneous micro operations that must be specified.
2. The way in which the control information is represented or encoded.
3. The way in which the next microinstruction address is specified.
a)
1 and 2
b)
2 and 3
c)
1 and 3
d)
All of these
|
|
Maitri Bose answered |
The correct answer is option 'D', which means that all of the given options are factors that determine the microinstruction length. Let's explore each of these factors in detail.
1. The maximum number of simultaneous microoperations that must be specified:
Microinstructions are used to control the operations of a microprogrammed control unit (MCU) within a CPU. These microinstructions typically specify a set of microoperations that need to be executed simultaneously during each machine cycle. The number of microoperations that must be specified in each microinstruction determines the length of the microinstruction. If there are a large number of simultaneous microoperations, the microinstruction length will be longer.
2. The way in which the control information is represented or encoded:
Control information in a microprogrammed control unit is represented using encoding schemes such as binary or one-hot encoding. The choice of encoding scheme affects the number of bits required to represent each control signal. The length of the microinstruction is determined by the total number of bits needed to represent all the control signals. Different encoding schemes may require different lengths of microinstructions.
3. The way in which the next microinstruction address is specified:
Microprograms are typically organized as a sequence of microinstructions stored in a control memory. The next microinstruction to be executed is determined by the address specified in the current microinstruction. The method used to specify the next microinstruction address can vary. It could be a direct address, an indirect address, or an address calculated based on some condition. The way in which the next microinstruction address is specified affects the number of bits required to represent the address, thereby impacting the microinstruction length.
In conclusion, the length of a microinstruction is determined by the maximum number of simultaneous microoperations that must be specified, the encoding scheme used for control information, and the method used to specify the next microinstruction address. All of these factors have an impact on the overall length of the microinstruction.
1. The maximum number of simultaneous microoperations that must be specified:
Microinstructions are used to control the operations of a microprogrammed control unit (MCU) within a CPU. These microinstructions typically specify a set of microoperations that need to be executed simultaneously during each machine cycle. The number of microoperations that must be specified in each microinstruction determines the length of the microinstruction. If there are a large number of simultaneous microoperations, the microinstruction length will be longer.
2. The way in which the control information is represented or encoded:
Control information in a microprogrammed control unit is represented using encoding schemes such as binary or one-hot encoding. The choice of encoding scheme affects the number of bits required to represent each control signal. The length of the microinstruction is determined by the total number of bits needed to represent all the control signals. Different encoding schemes may require different lengths of microinstructions.
3. The way in which the next microinstruction address is specified:
Microprograms are typically organized as a sequence of microinstructions stored in a control memory. The next microinstruction to be executed is determined by the address specified in the current microinstruction. The method used to specify the next microinstruction address can vary. It could be a direct address, an indirect address, or an address calculated based on some condition. The way in which the next microinstruction address is specified affects the number of bits required to represent the address, thereby impacting the microinstruction length.
In conclusion, the length of a microinstruction is determined by the maximum number of simultaneous microoperations that must be specified, the encoding scheme used for control information, and the method used to specify the next microinstruction address. All of these factors have an impact on the overall length of the microinstruction.
The most relevant addressing mode to write position-independent codes is:- a)Direct mode
- b)Indirect mode
- c)Relative mode
- d)Indexed mode
Correct answer is option 'C'. Can you explain this answer?
The most relevant addressing mode to write position-independent codes is:
a)
Direct mode
b)
Indirect mode
c)
Relative mode
d)
Indexed mode

|
Rutuja Deshpande answered |
C) Relative Mode since we can just change the content of base register if we wish to relocate.
The immediate addressing modes can be used for ______
1. Loading internal registers with initial value.
2. Perform arithmetic or logical operation on immediate data.- a) Only 1
- b)Only 2
- c) Either 1 or 2
- d)Neither 1 nor 2
Correct answer is option 'C'. Can you explain this answer?
The immediate addressing modes can be used for ______
1. Loading internal registers with initial value.
2. Perform arithmetic or logical operation on immediate data.
1. Loading internal registers with initial value.
2. Perform arithmetic or logical operation on immediate data.
a)
Only 1
b)
Only 2
c)
Either 1 or 2
d)
Neither 1 nor 2
|
|
Sagar Dasgupta answered |
Immediate addressing modes can be used for either loading internal register with initial value or perform arithmetic or logical operation on immediate data.
For the daisy chain scheme of connecting I/O devices, which of the following statements is true?- a)It gives non-uniform priority to various devices
- b)It gives uniform priority to all devices
- c)It is only useful for connecting slow devices to a processor device
- d)It requires a separate interrupt pin on the processor for each device
Correct answer is option 'A'. Can you explain this answer?
For the daisy chain scheme of connecting I/O devices, which of the following statements is true?
a)
It gives non-uniform priority to various devices
b)
It gives uniform priority to all devices
c)
It is only useful for connecting slow devices to a processor device
d)
It requires a separate interrupt pin on the processor for each device
|
|
Saikat Basu answered |
daisy chaining approach tell the processor i which order the interrupt should be handled by providing priority to the devices
In daisy chaining method all the devices are connected in serial. The device with the highest priority is placed in the first position, followed by lower priority devices . interrupt pin is common to all
so answer is a
In daisy chaining method all the devices are connected in serial. The device with the highest priority is placed in the first position, followed by lower priority devices . interrupt pin is common to all
so answer is a
In CISC architecture most of the complex instructions are stored in _____- a)Register
- b)Diodes
- c)CMOS
- d)Transistors
Correct answer is option 'D'. Can you explain this answer?
In CISC architecture most of the complex instructions are stored in _____
a)
Register
b)
Diodes
c)
CMOS
d)
Transistors
|
|
Rishabh Sharma answered |
Answer: d
Explanation: In CISC architecture more emphasis is given on the instruction set and the instructions take over a cycle to complete.
Explanation: In CISC architecture more emphasis is given on the instruction set and the instructions take over a cycle to complete.
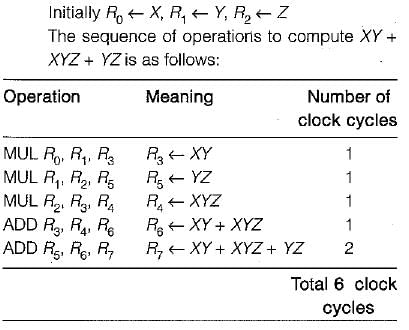
Consider a CPU has 8 general-purpose registers
R0, R1..., R7 and supports the following operations.
ADD Ra, Rb, Rc Add Ra to Rb and store the result to Rc.
MUL Ra, Rb, Rc Multiply Ra to Rb and store the result to Rc.
An operation normally takes one clock cycles, an operation takes two clock cycles if it produces a result required by the immediately following operations. Consider the expression XY + XYZ + YZ, where variables X, Y and Z are initially located in the registers R0, R1 and R2. If contents these registers must not be modified, what is the minimum number of clock cycles required for an operation sequence that computes the value of XY + XYZ + YZ?- a)4
- b)5
- c)6
- d)7
Correct answer is option 'C'. Can you explain this answer?
Consider a CPU has 8 general-purpose registers
R0, R1..., R7 and supports the following operations.
ADD Ra, Rb, Rc Add Ra to Rb and store the result to Rc.
MUL Ra, Rb, Rc Multiply Ra to Rb and store the result to Rc.
An operation normally takes one clock cycles, an operation takes two clock cycles if it produces a result required by the immediately following operations. Consider the expression XY + XYZ + YZ, where variables X, Y and Z are initially located in the registers R0, R1 and R2. If contents these registers must not be modified, what is the minimum number of clock cycles required for an operation sequence that computes the value of XY + XYZ + YZ?
R0, R1..., R7 and supports the following operations.
ADD Ra, Rb, Rc Add Ra to Rb and store the result to Rc.
MUL Ra, Rb, Rc Multiply Ra to Rb and store the result to Rc.
An operation normally takes one clock cycles, an operation takes two clock cycles if it produces a result required by the immediately following operations. Consider the expression XY + XYZ + YZ, where variables X, Y and Z are initially located in the registers R0, R1 and R2. If contents these registers must not be modified, what is the minimum number of clock cycles required for an operation sequence that computes the value of XY + XYZ + YZ?
a)
4
b)
5
c)
6
d)
7
|
|
Jatin Joshi answered |
Which of the following is a type of computer architecture?- a)Microarchitecture
- b)Harvard Architecture
- c)Von-Neumann Architecture
- d)All of the mentioned
Correct answer is option 'D'. Can you explain this answer?
Which of the following is a type of computer architecture?
a)
Microarchitecture
b)
Harvard Architecture
c)
Von-Neumann Architecture
d)
All of the mentioned
|
|
Kaavya Deshpande answered |
Computer Architecture:
Computer architecture refers to the design and organization of a computer system, including its components and how they interact. It defines the structure, behavior, and functionality of a computer system and determines how the hardware and software components work together to perform tasks.
Types of Computer Architecture:
There are different types of computer architecture, each with its own characteristics and design principles. The options provided in the question are all types of computer architecture.
a) Microarchitecture:
Microarchitecture, also known as computer organization, deals with the internal structure and design of a computer system. It focuses on implementing the architecture's specifications and includes the design of the CPU, memory, and other components. Microarchitecture defines the way instructions are executed and data is processed within the system.
b) Harvard Architecture:
Harvard Architecture is a computer architecture that separates the instruction and data memory. It has separate buses for instruction and data, allowing simultaneous access to both. This architecture is commonly found in embedded systems and microcontrollers.
c) Von-Neumann Architecture:
Von-Neumann Architecture is a computer architecture that uses a single bus to connect the CPU, memory, and other components. It stores both instructions and data in the same memory, and the CPU fetches, decodes, and executes instructions sequentially. This architecture is widely used in modern computers.
d) All of the mentioned:
The correct answer, option 'D', states that all the mentioned options (Microarchitecture, Harvard Architecture, and Von-Neumann Architecture) are types of computer architecture. This is true as each option represents a different approach to organizing and designing a computer system.
In summary, computer architecture encompasses different design principles and structures. Microarchitecture focuses on the internal design, Harvard Architecture separates instruction and data memory, and Von-Neumann Architecture uses a single memory for both instructions and data. All three options mentioned in the question are types of computer architecture.
Computer architecture refers to the design and organization of a computer system, including its components and how they interact. It defines the structure, behavior, and functionality of a computer system and determines how the hardware and software components work together to perform tasks.
Types of Computer Architecture:
There are different types of computer architecture, each with its own characteristics and design principles. The options provided in the question are all types of computer architecture.
a) Microarchitecture:
Microarchitecture, also known as computer organization, deals with the internal structure and design of a computer system. It focuses on implementing the architecture's specifications and includes the design of the CPU, memory, and other components. Microarchitecture defines the way instructions are executed and data is processed within the system.
b) Harvard Architecture:
Harvard Architecture is a computer architecture that separates the instruction and data memory. It has separate buses for instruction and data, allowing simultaneous access to both. This architecture is commonly found in embedded systems and microcontrollers.
c) Von-Neumann Architecture:
Von-Neumann Architecture is a computer architecture that uses a single bus to connect the CPU, memory, and other components. It stores both instructions and data in the same memory, and the CPU fetches, decodes, and executes instructions sequentially. This architecture is widely used in modern computers.
d) All of the mentioned:
The correct answer, option 'D', states that all the mentioned options (Microarchitecture, Harvard Architecture, and Von-Neumann Architecture) are types of computer architecture. This is true as each option represents a different approach to organizing and designing a computer system.
In summary, computer architecture encompasses different design principles and structures. Microarchitecture focuses on the internal design, Harvard Architecture separates instruction and data memory, and Von-Neumann Architecture uses a single memory for both instructions and data. All three options mentioned in the question are types of computer architecture.
Processor XYZ supports only the immediate and the direct addressing modes. Which of the following programming language data structures cannot be implemented on this processors?
1. Pointers
2. Arrays
3. Record- a)1,2 and 3
- b)2 and 3
- c)1 and 2
- d)Only 1
Correct answer is option 'A'. Can you explain this answer?
Processor XYZ supports only the immediate and the direct addressing modes. Which of the following programming language data structures cannot be implemented on this processors?
1. Pointers
2. Arrays
3. Record
1. Pointers
2. Arrays
3. Record
a)
1,2 and 3
b)
2 and 3
c)
1 and 2
d)
Only 1
|
|
Preethi Basu answered |
To access pointer, arrays and records we need indirect addressing modes, so with direct and immediate addressing modes we cannot implement these.
If an exception is raised and the succeeding instructions are executed completely, then the processor is said to have ______- a)Generation word
- b)Exception handling
- c)Imprecise exceptions
- d)None of the mentioned
Correct answer is option 'C'. Can you explain this answer?
If an exception is raised and the succeeding instructions are executed completely, then the processor is said to have ______
a)
Generation word
b)
Exception handling
c)
Imprecise exceptions
d)
None of the mentioned
|
|
Sudhir Patel answered |
The processor since as executed the following instructions even though an exception was raised, hence the exception is treated as imprecise.
Which of the following is a type of architecture used in the computers nowadays?- a)Microarchitecture
- b)Harvard Architecture
- c)Von-Neumann Architecture
- d)System Design
Correct answer is option 'C'. Can you explain this answer?
Which of the following is a type of architecture used in the computers nowadays?
a)
Microarchitecture
b)
Harvard Architecture
c)
Von-Neumann Architecture
d)
System Design
|
|
Manisha Sharma answered |
Von-Neumann Architecture
Von-Neumann Architecture is a type of computer architecture that is widely used in modern computers. It is named after John Von-Neumann, who first proposed this architecture in the late 1940s. This architecture has two main components: the Central Processing Unit (CPU) and the Memory.
CPU
The CPU is responsible for executing instructions and performing calculations. It has three main components:
1. Control Unit: It fetches the instructions from the memory and decodes them into a form that the CPU can understand. It also directs the execution of these instructions.
2. Arithmetic and Logic Unit (ALU): It performs arithmetic and logical operations, such as addition, subtraction, multiplication, division, and comparison.
3. Registers: These are small, temporary storage locations inside the CPU that hold data while the CPU processes it.
Memory
Memory is the storage area where data and program instructions are stored. It is divided into two main types:
1. Random Access Memory (RAM): This is the main memory of the computer, where the operating system and programs are loaded. It is volatile, which means that its contents are lost when the computer is turned off.
2. Read-Only Memory (ROM): This is a type of memory that is pre-programmed with instructions that cannot be changed. It is used to store the firmware that controls the computer's boot process.
Advantages of Von-Neumann Architecture
1. It is a simple and easy-to-understand architecture.
2. It allows programs to be stored in memory and executed by the CPU, which makes it possible to run complex programs.
3. It is flexible and can be used in a wide range of applications, from small embedded systems to large mainframe computers.
Conclusion
Von-Neumann Architecture is a widely used computer architecture that is based on the concept of storing program instructions and data in the same memory. It is simple, flexible, and can be used in a wide range of applications.
Von-Neumann Architecture is a type of computer architecture that is widely used in modern computers. It is named after John Von-Neumann, who first proposed this architecture in the late 1940s. This architecture has two main components: the Central Processing Unit (CPU) and the Memory.
CPU
The CPU is responsible for executing instructions and performing calculations. It has three main components:
1. Control Unit: It fetches the instructions from the memory and decodes them into a form that the CPU can understand. It also directs the execution of these instructions.
2. Arithmetic and Logic Unit (ALU): It performs arithmetic and logical operations, such as addition, subtraction, multiplication, division, and comparison.
3. Registers: These are small, temporary storage locations inside the CPU that hold data while the CPU processes it.
Memory
Memory is the storage area where data and program instructions are stored. It is divided into two main types:
1. Random Access Memory (RAM): This is the main memory of the computer, where the operating system and programs are loaded. It is volatile, which means that its contents are lost when the computer is turned off.
2. Read-Only Memory (ROM): This is a type of memory that is pre-programmed with instructions that cannot be changed. It is used to store the firmware that controls the computer's boot process.
Advantages of Von-Neumann Architecture
1. It is a simple and easy-to-understand architecture.
2. It allows programs to be stored in memory and executed by the CPU, which makes it possible to run complex programs.
3. It is flexible and can be used in a wide range of applications, from small embedded systems to large mainframe computers.
Conclusion
Von-Neumann Architecture is a widely used computer architecture that is based on the concept of storing program instructions and data in the same memory. It is simple, flexible, and can be used in a wide range of applications.
Given below are some statements associated with the registers of a CPU. Identify the false statement.- a)The program counter holds the memory address of the instruction in execution.
- b)Only opcode is transferred to the control unit.
- c)An instruction in the instruction register consists of the opcode and the operand.
- d)The value of the program counter is incremented by 1 once its value has been read to the memory address register.
Correct answer is option 'A'. Can you explain this answer?
Given below are some statements associated with the registers of a CPU. Identify the false statement.
a)
The program counter holds the memory address of the instruction in execution.
b)
Only opcode is transferred to the control unit.
c)
An instruction in the instruction register consists of the opcode and the operand.
d)
The value of the program counter is incremented by 1 once its value has been read to the memory address register.
|
|
Rohit Mukherjee answered |
Program counter contain the address of next instruction to be fetched but not address of executed instruction.
The register which keeps track of the execution of a program and which contains the memory address of the instruction which is to be executed next is known as ______ .- a)Index-Register
- b)Memory address register
- c)Program counter .
- d)Instruction registers
Correct answer is option 'C'. Can you explain this answer?
The register which keeps track of the execution of a program and which contains the memory address of the instruction which is to be executed next is known as ______ .
a)
Index-Register
b)
Memory address register
c)
Program counter .
d)
Instruction registers

|
Rutuja Pillai answered |
The register which keeps track of the execution of a program and which contains the memory address of the instruction currently being executed is known as Program counter. A program counter is a register in a computer processor that contains the address (location) of the instruction being executed at the current time.
In case of vectored interrupt, interrupt vector means- a)The branch information from the source which interrupts the system
- b)An address that points to a location in memory where the beginning address of the I/O service routine is stored
- c)Both (a) and (b)
- d)None of these
Correct answer is option 'C'. Can you explain this answer?
In case of vectored interrupt, interrupt vector means
a)
The branch information from the source which interrupts the system
b)
An address that points to a location in memory where the beginning address of the I/O service routine is stored
c)
Both (a) and (b)
d)
None of these
|
|
Shounak Das answered |
In a vectored interrupt, the source that interrupts supplies the branch information to the computer. This information is called the interrupt vector. In. some computers the interrupt vector is an address that points to a location in memory where the beginning address of the Input Output service routine is stored.
Consider a hypothetical processor with an instruction of type, which during execution reads a 32-bit word from memory and stores it in a 32-bit register. The effective address of the memory location is obtained by the addition of a constant 20 and the contents of register. Which of the following best reflects the addressing mode implemented by this instruction for the operand in memory?- a)Immediate addressing
- b)Register addressing
- c)Register Indirect Scaled Addressing
- d)Base Indexed Addressing
Correct answer is option 'D'. Can you explain this answer?
Consider a hypothetical processor with an instruction of type, which during execution reads a 32-bit word from memory and stores it in a 32-bit register. The effective address of the memory location is obtained by the addition of a constant 20 and the contents of register. Which of the following best reflects the addressing mode implemented by this instruction for the operand in memory?
a)
Immediate addressing
b)
Register addressing
c)
Register Indirect Scaled Addressing
d)
Base Indexed Addressing
|
|
Saanvi Bajaj answered |
Answer: D
Base Index Addressing, as the content of register R2 will serve as the index and 20 will be the Base address.
Base Index Addressing, as the content of register R2 will serve as the index and 20 will be the Base address.
Which is the most appropriate match for the items in the first column with the items in the second column
X. Indirect Addressing I. Array implementation
Y. Indexed addressing II. Writing relocatable code
Z. Base Register Addressing III. Passing array as parameter - a)(X, III) (Y, I) (Z, II)
- b)(X, II) (Y, III) (Z, I)
- c)(X, III) (Y, II) (Z, I)
- d)(X, I) (Y, III) (Z, II)
Correct answer is option 'A'. Can you explain this answer?
Which is the most appropriate match for the items in the first column with the items in the second column
X. Indirect Addressing I. Array implementation
Y. Indexed addressing II. Writing relocatable code
Z. Base Register Addressing III. Passing array as parameter
X. Indirect Addressing I. Array implementation
Y. Indexed addressing II. Writing relocatable code
Z. Base Register Addressing III. Passing array as parameter
a)
(X, III) (Y, I) (Z, II)
b)
(X, II) (Y, III) (Z, I)
c)
(X, III) (Y, II) (Z, I)
d)
(X, I) (Y, III) (Z, II)
|
|
Prateek Khanna answered |
(A) is the answer.
Array implementation can use Indexed addressing
While passing array as parameter we can make use of a pointer (as in C) and hence can use Indirect addressing
Base Register addressing can be used to write relocatable code by changing the content of Base Register.
Array implementation can use Indexed addressing
While passing array as parameter we can make use of a pointer (as in C) and hence can use Indirect addressing
Base Register addressing can be used to write relocatable code by changing the content of Base Register.
Both the CISC and RISC architectures have been developed to reduce the ______- a)Cost
- b)Time delay
- c)Semantic gap
- d)All of the mentioned
Correct answer is option 'C'. Can you explain this answer?
Both the CISC and RISC architectures have been developed to reduce the ______
a)
Cost
b)
Time delay
c)
Semantic gap
d)
All of the mentioned
|
|
Rishabh Sharma answered |
Answer: c
Explanation: The semantic gap is the gap between the high level language and the low level language.
Explanation: The semantic gap is the gap between the high level language and the low level language.
Which of the following affects processing power?- a)Data bus capacity
- b)Addressing scheme
- c)Clockspeed
- d)All of these
Correct answer is option 'D'. Can you explain this answer?
Which of the following affects processing power?
a)
Data bus capacity
b)
Addressing scheme
c)
Clockspeed
d)
All of these
|
|
Ameya Basak answered |
Processing power depends on clock speed, data bus capacity and addressing scheme.
If the instruction Add R1, R2, R3 is executed in a system which is pipelined, then the value of S is (Where S is term of the Basic performance equation).- a)2
- b)~1
- c)~7
- d)None of the above
Correct answer is option 'B'. Can you explain this answer?
If the instruction Add R1, R2, R3 is executed in a system which is pipelined, then the value of S is (Where S is term of the Basic performance equation).
a)
2
b)
~1
c)
~7
d)
None of the above
|
|
Milan Mukherjee answered |
Pipelining and Basic Performance Equation
Pipelining is a technique used in computer architecture to improve the performance of instruction execution by overlapping the execution of multiple instructions. It breaks down the instruction execution into multiple stages, and each stage can process a different instruction simultaneously.
The basic performance equation is given by:
S = 1 / (1 + p + (p^2)/n)
Where,
S = Speedup
p = Pipeline stages
n = Number of instructions
Given Instruction: Add R1, R2, R3
The instruction Add R1, R2, R3 is a typical arithmetic instruction that adds the contents of registers R2 and R3 and stores the result in register R1. Let's analyze the execution of this instruction in a pipelined system.
Pipeline Stages
In a basic 5-stage pipeline, the instruction execution is divided into the following stages:
1. Instruction Fetch (IF): Fetch the instruction from memory.
2. Instruction Decode (ID): Decode the instruction and read the operands from registers.
3. Execution (EX): Perform the arithmetic operation.
4. Memory Access (MEM): Access memory if required.
5. Write Back (WB): Write the result back to a register.
Pipelined Execution
Let's assume that the pipeline is initially empty and the first instruction enters the pipeline.
1. Cycle 1: IF stage of the first instruction (Add R1, R2, R3) is executed.
2. Cycle 2: ID stage of the first instruction is executed.
3. Cycle 3: EX stage of the first instruction is executed.
4. Cycle 4: MEM stage of the first instruction is executed.
5. Cycle 5: WB stage of the first instruction is executed.
At this point, the first instruction is completed. However, the subsequent stages of the pipeline are still processing the instruction.
Effect on the Basic Performance Equation
Since the pipeline introduces a delay due to the pipeline stages, the value of p (pipeline stages) increases. As a result, the overall performance of the system decreases.
In the given instruction Add R1, R2, R3, there are no dependencies on the result of previous instructions. Hence, the pipeline can operate at its maximum efficiency.
When the pipeline stages are fully utilized, the value of p approaches infinity in the performance equation. Therefore, the equation simplifies to:
S = 1 / (1 + 1/infinity + (1/infinity)^2/n)
S ≈ 1
Hence, the value of S is approximately 1, which corresponds to option B.
Pipelining is a technique used in computer architecture to improve the performance of instruction execution by overlapping the execution of multiple instructions. It breaks down the instruction execution into multiple stages, and each stage can process a different instruction simultaneously.
The basic performance equation is given by:
S = 1 / (1 + p + (p^2)/n)
Where,
S = Speedup
p = Pipeline stages
n = Number of instructions
Given Instruction: Add R1, R2, R3
The instruction Add R1, R2, R3 is a typical arithmetic instruction that adds the contents of registers R2 and R3 and stores the result in register R1. Let's analyze the execution of this instruction in a pipelined system.
Pipeline Stages
In a basic 5-stage pipeline, the instruction execution is divided into the following stages:
1. Instruction Fetch (IF): Fetch the instruction from memory.
2. Instruction Decode (ID): Decode the instruction and read the operands from registers.
3. Execution (EX): Perform the arithmetic operation.
4. Memory Access (MEM): Access memory if required.
5. Write Back (WB): Write the result back to a register.
Pipelined Execution
Let's assume that the pipeline is initially empty and the first instruction enters the pipeline.
1. Cycle 1: IF stage of the first instruction (Add R1, R2, R3) is executed.
2. Cycle 2: ID stage of the first instruction is executed.
3. Cycle 3: EX stage of the first instruction is executed.
4. Cycle 4: MEM stage of the first instruction is executed.
5. Cycle 5: WB stage of the first instruction is executed.
At this point, the first instruction is completed. However, the subsequent stages of the pipeline are still processing the instruction.
Effect on the Basic Performance Equation
Since the pipeline introduces a delay due to the pipeline stages, the value of p (pipeline stages) increases. As a result, the overall performance of the system decreases.
In the given instruction Add R1, R2, R3, there are no dependencies on the result of previous instructions. Hence, the pipeline can operate at its maximum efficiency.
When the pipeline stages are fully utilized, the value of p approaches infinity in the performance equation. Therefore, the equation simplifies to:
S = 1 / (1 + 1/infinity + (1/infinity)^2/n)
S ≈ 1
Hence, the value of S is approximately 1, which corresponds to option B.
Which of the architecture is power efficient?- a)RISC
- b)ISA
- c)IANA
- d)CISC
Correct answer is option 'A'. Can you explain this answer?
Which of the architecture is power efficient?
a)
RISC
b)
ISA
c)
IANA
d)
CISC
|
|
Sudhir Patel answered |
Hence the RISC architecture is followed in the design of mobile devices.
Which of the following addressing modes are suitable for program relocation at run time?
I. Absolute addressing
II. Based addressing
III. Relative addressing
IV. Indirect addressing- a)I and IV
- b)I and II
- c)II and III
- d)I, II and IV
Correct answer is option 'C'. Can you explain this answer?
Which of the following addressing modes are suitable for program relocation at run time?
I. Absolute addressing
II. Based addressing
III. Relative addressing
IV. Indirect addressing
I. Absolute addressing
II. Based addressing
III. Relative addressing
IV. Indirect addressing
a)
I and IV
b)
I and II
c)
II and III
d)
I, II and IV
|
|
Kiran Reddy answered |
Answer: C
A displacement type addressing should be preferred. So, I is not the answer.
Indirect Addressing leads to extra memory reference which is not preferable at run time. So, IV is not the answer.
A displacement type addressing should be preferred. So, I is not the answer.
Indirect Addressing leads to extra memory reference which is not preferable at run time. So, IV is not the answer.
Consider the C struct defined below:
struct data {
int marks [100];
char grade;
int cnumber;
};
struct data student;
The base address of student is available in register R1. The field student.grade can be accessed efficiently using- a)Post-increment addressing mode, (R1)+
- b)Pre-decrement addressing mode, -(R1)
- c)Register direct addressing mode, R1
- d)Index addressing mode, X(R1), where X is an offset represented in 2's complement 16-bit representation.
Correct answer is option 'D'. Can you explain this answer?
Consider the C struct defined below:
struct data {
int marks [100];
char grade;
int cnumber;
};
struct data student;
The base address of student is available in register R1. The field student.grade can be accessed efficiently using
struct data {
int marks [100];
char grade;
int cnumber;
};
struct data student;
The base address of student is available in register R1. The field student.grade can be accessed efficiently using
a)
Post-increment addressing mode, (R1)+
b)
Pre-decrement addressing mode, -(R1)
c)
Register direct addressing mode, R1
d)
Index addressing mode, X(R1), where X is an offset represented in 2's complement 16-bit representation.
|
|
Anagha Choudhary answered |
Option (D)
Displacement Mode :-
Similar to index mode, except instead of a index register a base register will be used. Base register contains a pointer to a memory location. An integer (constant) is also referred to as a displacement. The address of the operand is obtained by
adding the contents of the base register plus the constant. The difference between index mode and displacement mode is in the number of bits used to represent the constant. When the constant is represented a number of bits to access the
memory, then we have index mode. Index mode is more appropriate for array accessing; displacement mode is more appropriate for structure (records) accessing.
Similar to index mode, except instead of a index register a base register will be used. Base register contains a pointer to a memory location. An integer (constant) is also referred to as a displacement. The address of the operand is obtained by
adding the contents of the base register plus the constant. The difference between index mode and displacement mode is in the number of bits used to represent the constant. When the constant is represented a number of bits to access the
memory, then we have index mode. Index mode is more appropriate for array accessing; displacement mode is more appropriate for structure (records) accessing.
Match the pairs in the following questions:
(A) Base addressing (p) Reentranecy
(B) Indexed addressing (q) Accumulator
(C) Stack addressing (r) Array
(D) Implied addressing (s) Position independent- a)A-S, B-R, C-P, D-Q
- b)A-S, B-R, C-Q, D-P
- c)A-R, B-S, C-Q, D-P
- d)A-R, B-S, C-P, D-Q
Correct answer is option 'A'. Can you explain this answer?
Match the pairs in the following questions:
(A) Base addressing (p) Reentranecy
(B) Indexed addressing (q) Accumulator
(C) Stack addressing (r) Array
(D) Implied addressing (s) Position independent
(A) Base addressing (p) Reentranecy
(B) Indexed addressing (q) Accumulator
(C) Stack addressing (r) Array
(D) Implied addressing (s) Position independent
a)
A-S, B-R, C-P, D-Q
b)
A-S, B-R, C-Q, D-P
c)
A-R, B-S, C-Q, D-P
d)
A-R, B-S, C-P, D-Q
|
|
Keerthana Sarkar answered |
(A) Base addressing - Position independent (By changing value in Base register location of address can be changed)
(B) Indexed addressing - Array
(C) Stack addressing - Reentranecy (Whenever code happens to be used again, address need not be the same)
(D) Implied addressing - Accumulator (If an address is not specified, it is assumed/implied to be the Accumulator)
in a certain processor, a 2 byte Jump instruction is encountered at memory address 3010 H, the Jump instruction is in PC relative mode. The instruction is JMP - 7 where - 7 is signed byte. Determine the Branch Target Address - a)3005 H
- b)3009 H
- c)3003 H
- d)3007 H
Correct answer is option 'A'. Can you explain this answer?
in a certain processor, a 2 byte Jump instruction is encountered at memory address 3010 H, the Jump instruction is in PC relative mode. The instruction is JMP - 7 where - 7 is signed byte. Determine the Branch Target Address
a)
3005 H
b)
3009 H
c)
3003 H
d)
3007 H
|
|
Malavika Sarkar answered |
The Jump instruction is at address 3010 H and instruction is 2 bytes. Therefore, PC points to 3012 H on execution of this instruction.
Now Branch Target PC
= PC + (-7)
= 3012 H - 7 H = 3005 H
Now Branch Target PC
= PC + (-7)
= 3012 H - 7 H = 3005 H
The Sun micro systems processors usually follow _____ architecture.- a)CISC
- b)ISA
- c)ULTRA SPARC
- d)RISC
Correct answer is option 'D'. Can you explain this answer?
The Sun micro systems processors usually follow _____ architecture.
a)
CISC
b)
ISA
c)
ULTRA SPARC
d)
RISC
|
|
Palak Khanna answered |
Answer: d
Explanation: The Risc machine aims at reducing the instruction set of the computer.
Explanation: The Risc machine aims at reducing the instruction set of the computer.
What is computer organization?- a)structure and behaviour of a computer system as observed by the user
- b)structure of a computer system as observed by the developer
- c)structure and behaviour of a computer system as observed by the developer
- d)All of the mentioned
Correct answer is option 'A'. Can you explain this answer?
What is computer organization?
a)
structure and behaviour of a computer system as observed by the user
b)
structure of a computer system as observed by the developer
c)
structure and behaviour of a computer system as observed by the developer
d)
All of the mentioned
|
|
Rohan Patel answered |
Computer Organization:
Computer organization refers to the structure and behavior of a computer system as observed by the user. It involves understanding how the various components of a computer system are organized and how they interact with each other to perform tasks.
Components of a Computer System:
To better understand computer organization, let's look at the key components of a computer system:
1. Central Processing Unit (CPU): The CPU is the brain of the computer, responsible for executing instructions and performing calculations. It consists of the control unit, arithmetic logic unit (ALU), and registers.
2. Memory: Memory is used to store data and instructions that the CPU needs to access quickly. It includes primary memory (RAM) and secondary memory (hard drives, solid-state drives, etc.).
3. Input/Output (I/O) Devices: These devices allow users to input data and receive output from the computer. Examples include keyboards, mice, monitors, printers, and storage devices.
4. Bus: The bus is a communication pathway that allows data to be transferred between the CPU, memory, and I/O devices.
5. Control Unit: The control unit coordinates and controls the operations of the CPU and other hardware components. It fetches instructions from memory, decodes them, and directs the necessary actions.
6. Instruction Set Architecture (ISA): ISA is the interface between the hardware and software. It defines the instructions that a CPU can execute and the format in which they are encoded.
Structure and Behavior:
The structure of a computer system refers to how the different components are organized and interconnected. It includes the physical arrangement of the hardware components and the logical relationships between them.
The behavior of a computer system refers to how it operates and responds to user instructions. It encompasses the execution of instructions, data processing, and the flow of information between different components.
User Perspective:
From a user's perspective, computer organization is the way a computer system appears and functions. It involves understanding the user interface, input/output capabilities, and general operation of the system. Users interact with the computer through applications and software, and they rely on the system to perform tasks efficiently and reliably.
By studying computer organization, users can gain a deeper understanding of how their computer systems work and make informed decisions about hardware upgrades, system configurations, and software compatibility.
In conclusion, computer organization focuses on the structure and behavior of a computer system as observed by the user. It encompasses the arrangement of hardware components, their interactions, and the overall functionality of the system. Understanding computer organization is crucial for both users and developers to effectively utilize and optimize computer systems.
Computer organization refers to the structure and behavior of a computer system as observed by the user. It involves understanding how the various components of a computer system are organized and how they interact with each other to perform tasks.
Components of a Computer System:
To better understand computer organization, let's look at the key components of a computer system:
1. Central Processing Unit (CPU): The CPU is the brain of the computer, responsible for executing instructions and performing calculations. It consists of the control unit, arithmetic logic unit (ALU), and registers.
2. Memory: Memory is used to store data and instructions that the CPU needs to access quickly. It includes primary memory (RAM) and secondary memory (hard drives, solid-state drives, etc.).
3. Input/Output (I/O) Devices: These devices allow users to input data and receive output from the computer. Examples include keyboards, mice, monitors, printers, and storage devices.
4. Bus: The bus is a communication pathway that allows data to be transferred between the CPU, memory, and I/O devices.
5. Control Unit: The control unit coordinates and controls the operations of the CPU and other hardware components. It fetches instructions from memory, decodes them, and directs the necessary actions.
6. Instruction Set Architecture (ISA): ISA is the interface between the hardware and software. It defines the instructions that a CPU can execute and the format in which they are encoded.
Structure and Behavior:
The structure of a computer system refers to how the different components are organized and interconnected. It includes the physical arrangement of the hardware components and the logical relationships between them.
The behavior of a computer system refers to how it operates and responds to user instructions. It encompasses the execution of instructions, data processing, and the flow of information between different components.
User Perspective:
From a user's perspective, computer organization is the way a computer system appears and functions. It involves understanding the user interface, input/output capabilities, and general operation of the system. Users interact with the computer through applications and software, and they rely on the system to perform tasks efficiently and reliably.
By studying computer organization, users can gain a deeper understanding of how their computer systems work and make informed decisions about hardware upgrades, system configurations, and software compatibility.
In conclusion, computer organization focuses on the structure and behavior of a computer system as observed by the user. It encompasses the arrangement of hardware components, their interactions, and the overall functionality of the system. Understanding computer organization is crucial for both users and developers to effectively utilize and optimize computer systems.
Both the CISC and RISC architectures have been developed to reduce the ______- a)Time delay
- b)Semantic gap
- c)Cost
- d)All of the mentioned
Correct answer is option 'B'. Can you explain this answer?
Both the CISC and RISC architectures have been developed to reduce the ______
a)
Time delay
b)
Semantic gap
c)
Cost
d)
All of the mentioned
|
|
Partho Joshi answered |
Reducing the Semantic Gap with CISC and RISC Architectures
One of the primary goals of both Complex Instruction Set Computing (CISC) and Reduced Instruction Set Computing (RISC) architectures is to reduce the semantic gap between the high-level programming languages and the actual hardware instructions executed by the computer. This is crucial for improving the efficiency and performance of computer systems.
CISC Architecture
- CISC architectures are designed with a large set of complex instructions that can perform multiple operations in a single instruction. This helps in reducing the number of instructions needed to execute a program, thus potentially reducing the time delay in program execution.
- By providing a wide variety of instructions, CISC architectures aim to bridge the semantic gap by allowing programmers to write code in a more natural and high-level manner.
RISC Architecture
- RISC architectures, on the other hand, focus on a simpler set of instructions that are optimized for specific tasks. This simplicity allows for faster execution of instructions and reduces the complexity of the hardware, leading to a more efficient system.
- RISC architectures aim to reduce the semantic gap by encouraging programmers to write more optimized code that directly maps to the hardware instructions, thus improving performance.
Reducing the Semantic Gap
- By reducing the semantic gap, both CISC and RISC architectures aim to make programming more efficient and improve the overall performance of computer systems.
- While CISC architectures provide more flexibility and ease of programming, RISC architectures offer better performance and efficiency by simplifying the instruction set.
In conclusion, both CISC and RISC architectures have been developed with the goal of reducing the semantic gap between high-level programming languages and hardware instructions, ultimately leading to more efficient and optimized computer systems.
For a given FINITE number of instructions to be executed, which architecture of the processor provides for a faster execution?- a)ANSA
- b)Super-scalar
- c)ISA
- d)All of the mentioned
Correct answer is option 'B'. Can you explain this answer?
For a given FINITE number of instructions to be executed, which architecture of the processor provides for a faster execution?
a)
ANSA
b)
Super-scalar
c)
ISA
d)
All of the mentioned
|
|
Sudhir Patel answered |
In super-scalar architecture, the instructions are set in groups and they’re decoded and executed together reducing the amount of time required to process them.
Chapter doubts & questions for Machine Instructions & Addressing Modes - 6 Months Preparation for GATE CSE 2025 is part of Computer Science Engineering (CSE) exam preparation. The chapters have been prepared according to the Computer Science Engineering (CSE) exam syllabus. The Chapter doubts & questions, notes, tests & MCQs are made for Computer Science Engineering (CSE) 2025 Exam. Find important definitions, questions, notes, meanings, examples, exercises, MCQs and online tests here.
Chapter doubts & questions of Machine Instructions & Addressing Modes - 6 Months Preparation for GATE CSE in English & Hindi are available as part of Computer Science Engineering (CSE) exam.
Download more important topics, notes, lectures and mock test series for Computer Science Engineering (CSE) Exam by signing up for free.
6 Months Preparation for GATE CSE
459 videos|1398 docs|786 tests
|

Contact Support
Our team is online on weekdays between 10 AM - 7 PM
Typical reply within 3 hours
|
Free Exam Preparation
at your Fingertips!
Access Free Study Material - Test Series, Structured Courses, Free Videos & Study Notes and Prepare for Your Exam With Ease

 Join the 10M+ students on EduRev
Join the 10M+ students on EduRev
|

|
Create your account for free
OR
Forgot Password
OR
Signup to see your scores
go up within 7 days!
Access 1000+ FREE Docs, Videos and Tests
Takes less than 10 seconds to signup











