Awareness in Field of IT & Computers- 2 | Science & Technology for UPSC CSE PDF Download
Big Data
Big data is a term used to refer to the study and applications of data sets that are so big and complex that traditional data-processing application software is inadequate to deal with them. Big data challenges include capturing data, data storage, data analysis, search, sharing, transfer, visualization, querying, updating, information privacy, and data source.
There are a number of concepts associated with big data: originally there were three concepts volume, variety, velocity. Other concepts later attributed to big data are veracity (i.e., how much noise is in the data) and value.
Big data can be described by the following characteristics:
- Volume – The quantity of generated and stored data. The size of the data determines the value and potential insight, and whether it can be considered big data or not.
- Variety – The type and nature of the data. This helps people who analyze it to effectively use the resulting insight. Big data draws from text, images, audio, video; plus it completes missing pieces through data fusion.
- Velocity – In this context, the speed at which the data is generated and processed to meet the demands and challenges that lie in the path of growth and development. Big data is often available in real-time.
- Veracity – The data quality of captured data can vary greatly, affecting the accurate analysis.
Applications
Government: Big data is being increasingly used by the government in policy formation. The use and adoption of big data within governmental processes allow efficiencies in terms of cost, productivity, and innovation, but does not come without its flaws.
International development: Research on the effective usage of information and communication technologies for development (also known as ICT4D) suggests that big data technology can make important contributions but also present unique challenges to International development. Advancements in big data analysis offer cost-effective opportunities to improve decision-making in critical development areas such as health care, employment, economic productivity, crime, security, and natural disaster and resource management.
Manufacturing: A conceptual framework of predictive manufacturing begins with data acquisition where different type of sensory data is available to acquire such as acoustics, vibration, pressure, current, voltage, and controller data. The vast amount of sensory data in addition to historical data construct big data in manufacturing. The generated big data acts as the input into predictive tools and preventive strategies such as Prognostics and Health Management (PHM).
Healthcare: Big data analytics has helped healthcare improve by providing personalized medicine and prescriptive analytics, clinical risk intervention and predictive analytics, waste and care variability reduction, automated external and internal reporting of patient data, standardized medical terms, and patient registries and fragmented point solutions.
Education: A McKinsey Global Institute study found a shortage of 1.5 million highly trained data professionals and managers and a number of universities including the University of Tennessee and UC Berkeley, have created master’s programs to meet this demand. Private boot camps have also developed programs to meet that demand, including free programs like The Data Incubator or paid programs like General Assembly.
Media–
- Targeting of consumers (for advertising by marketers)
- Data capture
- Data journalism: publishers and journalists use big data tools to provide unique and innovative insights and infographics.
Insurance: Health insurance providers are collecting data on social “determinants of health” such as food and TV consumption, marital status, clothing size and purchasing habits, from which they make predictions on health costs, in order to spot health issues in their clients. It is controversial whether these predictions are currently being used for pricing.
Internet of Things (IoT)
Big data and the IoT work in conjunction. Data extracted from IoT devices provides a mapping of device interconnectivity. Such mappings have been used by the media industry, companies, and governments to more accurately target their audience and increase media efficiency. IoT is also increasingly adopted as a means of gathering sensory data, and this sensory data has been used in medical, manufacturing, and transportation contexts.
End-to-end encryption (E2EE)
End-to-end encryption (E2EE) is a system of communication where only communicating users can read the messages. In principle, it prevents potential eavesdroppers – including telecom providers, Internet providers, and even the provider of the communication service – from being able to access the cryptographic keys needed to decrypt the conversation.
Point-to-point encryption (P2PE)
Point-to-point encryption (P2PE) is a standard established by the PCI Security Standards Council. Payment solutions that offer similar encryption but do not meet the P2Pe standard are referred to as end-to-end encryption (E2Ee) solutions. The objective of P2Pe and E2Ee is to provide a payment security solution that instantaneously converts confidential payment card (credit and debit card) data and information into indecipherable code at the time the card is swiped to prevent hacking and fraud. It is designed to maximize the security of payment card transactions in an increasingly complex regulatory environment.
Deep Web
The deep web, invisible web, or hidden webs are parts of the World Wide Web whose contents are not indexed by standard web search engines for any reason. The opposite term to the deep web is the surface web, which is accessible to anyone using the Internet. Computer scientist Michael K. Bergman is credited with coining the term deep web in 2001 as a search indexing term.
The content of the deep web is hidden behind HTTP forms and includes many very common uses such as webmail, online banking, and services that users must pay for, and which is protected by a paywall, such as a video on demand, some online magazines, and newspapers, and many more.
Content of the deep web can be located and accessed by a direct URL or IP address and may require a password or other security access past the public website page.
Dark Web
The dark web is the World Wide Web content that exists on darknets, overlay networks that use the Internet but require specific software, configurations, or authorization to access. The dark web forms a small part of the deep web, the part of the Web not indexed by web search engines, although sometimes the term deep web is mistakenly used to refer specifically to the dark web.
The darknets which constitute the dark web include small, friend-to-friend peer-to-peer networks, as well as large, popular networks like Tor, Freenet, I2P, and Riffle operated by public organizations and individuals. Users of the dark web refer to the regular web as Clearnet due to its unencrypted nature.
The Tor dark web may be referred to as Onionland, a reference to the network’s top-level domain suffix. onion and the traffic anonymization technique of onion routing.
 Types of Web
Types of Web
Wannacry
The Wannacry ransomware attack was a May 2017 worldwide cyberattack by the Wannacry ransomware cryptoworm, which targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom payments in the Bitcoin cryptocurrency.
It propagated through Eternal Blue, an exploit in older Windows systems released by The Shadow Brokers a few months prior to the attack.
While Microsoft had released patches previously to close the exploit, much of WannaCry’s spread was from organizations that had not applied these or were using older Windows systems that were past their end-of-life. WannaCry also took advantage of installing backdoors onto infected systems.
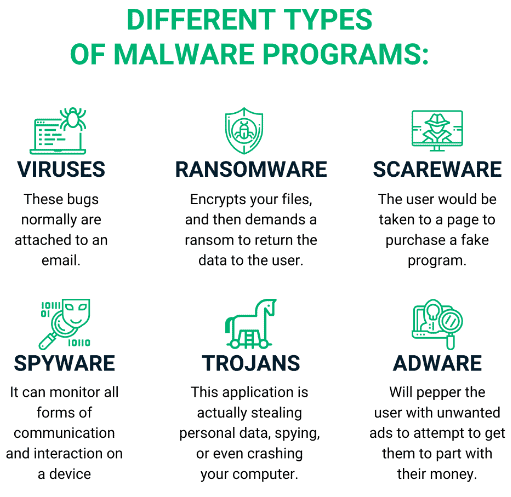 Types of Malware
Types of Malware
Botnet
A botnet is a number of Internet-connected devices, each of which is running one or more bots. Botnets can be used to perform distributed denial-of-service attack (DDoS attack), steal data, send spam, and allows the attacker to access the device and its connection. The owner can control the botnet using command and control (C&C) software. The word “botnet” is a combination of the words “robot” and “network”. The term is usually used with a negative or malicious connotation.
DDoS (Distributed Denial of Service) Attack
A DDoS (Distributed Denial of Service) attack is an illegal large-scale cyber campaign where a big number of devices are used to create traffic to a certain server.
If the number of devices involved is big enough, the overwhelming traffic would be more than what the targeted server is capable of handling.
The malware first creates a network of bots — called a botnet — and then uses the botnet to ping a single server at the same time.
In such a case, the server would get overburdened which would lead to crashes. After a successful DDoS attack, the customers of the service that had its servers targeted would not be able to use/access the said service due to the server crash triggered by the DDoS attacks.
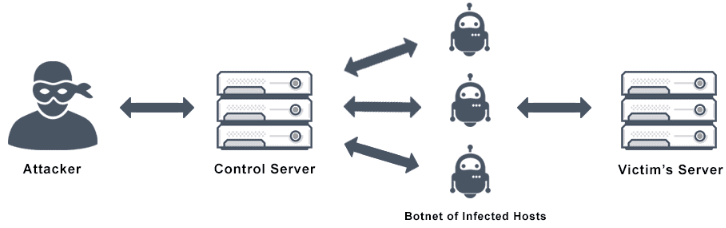 DDoS
DDoS
Reaper is a highly evolved malware capable of not only hacking devices like WiFi routers and security cameras, but also able to hide its own presence in the bot — a device taken over by malware.
Spectrum Pooling
Spectrum pooling is a spectrum management strategy in which multiple radio spectrum users can coexist within a single allocation of radio spectrum space. One use of this technique is for primary users of a spectrum allocation to be able to rent out use of unused parts of their allocation to secondary users. Spectrum pooling schemes generally require cognitive radio techniques to implement them.
Cognitive Radio
A cognitive radio (CR) is a radio that can be programmed and configured dynamically to use the best wireless channels in its vicinity to avoid user interference and congestion. Such a radio automatically detects available channels in wireless spectrum, then accordingly changes its transmission or reception parameters to allow more concurrent wireless communications in a given spectrum band at one location. This process is a form of dynamic spectrum management.
HTTPS
Hypertext Transfer Protocol Secure (HTTPS) is an extension of the Hypertext Transfer Protocol (HTTP) for secure communication over a computer network and is widely used on the Internet.
The principal motivation for HTTPS is authentication of the accessed website and protection of the privacy and integrity of the exchanged data while in transit. It protects against man-in-the-middle attacks.
The bidirectional encryption of communications between a client and server protects against eavesdropping and tampering of the communication. In practice, this provides a reasonable assurance that one is communicating without interference by attackers with the website that one intended to communicate with, as opposed to an impostor.

Quantum Computer
Quantum computing is computing using quantum-mechanical phenomena, such as superposition and entanglement. A quantum computer is a device that performs quantum computing. Such a computer is different from binary digital electronic computers based on transistors.
Whereas common digital computing requires that the data be encoded into binary digits (bits), each of which is always in one of two definite states (0 or 1), quantum computation uses quantum bits or qubits, which can be in superpositions of states. The qubit is the basic unit of quantum computing and the subatomic equivalent of the binary system comprising 0s and 1s that we use today.
It uses binary properties of particles, electron spin (up and down), photon polarization (positive and negative), etc, but, much like Schrödinger’s cat, can actually be in both states simultaneously, a phenomenon called superposition.
Physicists have observed that when one particle is observed, it seems to affect the state of the completely different, opposite particle in a phenomenon called entanglement. This is the basis of quantum computing and communication.
Quantum Supremacy
- Quantum supremacy is the ability to use a quantum computer to perform a single calculation that no conventional computer, even the biggest supercomputer, can perform in a reasonable amount of time.
- Google researchers claim to have achieved a major milestone in computer science known as “quantum supremacy.”.
- The Google research involved checking whether the output of an algorithm for generating random numbers was truly random. The researchers were able to use a quantum computer to perform this complex mathematical calculation in three minutes and 20 seconds, according to the paper.
- It is claimed that it would have taken Summit 3—an IBM-built machine that is the world’s most powerful commercially-available conventional computer—about 10,000 years to perform the same task.
Sycamore: Sycamore is Google’s state-of-the-art quantum computer that was used for Quantum Supremacy.
Quantum-Enabled Science & Technology (QuEST) Programme
India is starting work on building infrastructure and acquiring human resources in the first phase of its push to develop quantum computers under the Department of Science & Technology’s (DST’s) -Quantum-Enabled Science & Technology (QuEST) program.
Currently, QuEST is being funded by the DST, which has put in Rs 80 crore for Phase 1. After three years, the Defence Research and Development Organisation (DRDO), the Indian Space Research Organisation (ISRO), and the Department of Atomic Energy (DAE) are expected to jointly fund Phase 2 with Rs 300 crore.
Blockchain
Blockchains are basically digital ledgers or decentralized database of financial transactions that are immutable and instantly updated across the world.
By design, a blockchain is resistant to modification of the data. It is “an open, distributed ledger that can record transactions between two parties efficiently and in a verifiable and permanent way”. For use as a distributed ledger, a blockchain is typically managed by a peer-to-peer network collectively adhering to a protocol for inter-node communication and validating new blocks.
Once recorded, the data in any given block cannot be altered retroactively without the alteration of all subsequent blocks, which requires consensus of the network majority.
Although blockchain records are not unalterable, blockchains may be considered secure by design and exemplify a distributed computing system with high Byzantine fault tolerance. Decentralized consensus has therefore been claimed with a blockchain.
Blockchain was invented by Satoshi Nakamoto in 2008 to serve as the public transaction ledger of the cryptocurrency bitcoin. The invention of the blockchain for bitcoin made it the first digital currency to solve the double-spending problem without the need for a trusted authority or central server.
The bitcoin design has inspired other applications, and blockchains that are readable by the public are widely used by cryptocurrencies. Private blockchains have been proposed for business use. Some marketing of blockchains has been called “snake oil”.
Bitcoin
Bitcoin is a cryptocurrency, a form of electronic cash. It is a decentralized digital currency without a central bank or single administrator that can be sent from user to user on the peer-to-peer bitcoin network without the need for intermediaries.
Transactions are verified by network nodes through cryptography and recorded in a public distributed ledger called a blockchain. Bitcoin was invented by an unknown person or group of people using the name Satoshi Nakamoto and released as open-source software in 2009. Bitcoins are created as a reward for a process known as mining. They can be exchanged for other currencies, products, and services.
Bitcoin has been criticized for its use in illegal transactions, its high electricity consumption, price volatility, thefts from exchanges, and the possibility that bitcoin is an economic bubble. Bitcoin has also been used as an investment, although several regulatory agencies have issued investor alerts about bitcoin.
Artificial Intelligence
AI, is the “science and engineering of making intelligent machines, especially intelligent computer programs”. AI enables intelligent machines that can execute functions, similar to human abilities like speech, facial, object or gesture recognition, learning, problem-solving, reasoning, perception and response.
AI enables machines to think intelligently, somewhat akin to the intelligence human beings employ to learn, understand, think, decide, or solve a problem in their daily personal or professional lives. Intelligence is intangible.
The present wave of enthusiasm in AI is backed by the industry, with Apple, Amazon, Google, Facebook, IBM, Microsoft, and Baidu in the lead. Automotive industry is also unleashing benefits of AI for self-driving cars, led by Tesla, Mercedez-Benz, Google, and Uber.
Real-world examples from around us:
- AI-empowered cars are already under rigorous testing and they are quite likely to ply on the roads soon.
- The social humanoid robot Sophia became a citizen of Saudi Arabia in 2017.
- Apple’s intelligent personal assistant, Siri, can receive instructions and interact with human beings in natural language.
- Autonomous weapons can execute military missions on their own, identify and engage targets without any human intervention.
- Facial detection has instated deep interest from law enforcement and security agencies.
- China is known to be building a massive facial recognition system, connected with its surveillance camera networks, to assist in detecting criminals and fugitives.
- AI is also changing the ways militaries command, train, and deploy their forces.
Applications of AI
The gaming industry, where AI-empowered computers can think of a large number of possible positions in games such as chess, poker, and go. These computers can test the skills of the human beings who are playing against these AI-enabled computers, in games or simulations which require the greater mathematical and strategic depth.
Computers with natural language processing capability can understand and generate human language, including speech, imitating human capabilities of listening, comprehending, thinking, and responding.
Law enforcement or internal security requirements for detecting and recognizing individuals or criminals, with multitudes of data streaming from police databases or the network of surveillance cameras.
Healthcare industry to design optimized treatment plans, assistance in repetitive jobs, data management for medical records, or even assistance in clinical decision making with better analysis of diagnostics and interpretation of clinical laboratory results.
Banking and financial services for fraud detection using advanced algorithms to identify patterns in transactions and consumer behaviors that are risk-prone.
The automotive industry is already using AI algorithms to enhance fuel efficiency and safety in vehicles to build features such as automatic braking, collision avoidance systems, alerts for pedestrians and cyclists, and intelligent cruise controls.
Deep Learning
It is an aspect of artificial intelligence (AI) that is concerned with emulating the learning approach that human beings use to gain certain types of knowledge. At its simplest, deep learning can be thought of as a way to automate predictive analytics.
While traditional machine learning algorithms are linear, deep learning algorithms are stacked in a hierarchy of increasing complexity and abstraction. To understand deep learning, imagine a toddler whose first word is the dog. The toddler learns what a dog is (and is not) by pointing to objects and saying the word dog. The parent says, “Yes, that is a dog,” or, “No, that is not a dog.” As the toddler continues to point to objects, he becomes more aware of the features that all dogs possess. What the toddler does, without knowing it, is clarify a complex abstraction (the concept of dog) by building a hierarchy in which each level of abstraction is created with knowledge that was gained from the preceding layer of the hierarchy.
Machine Learning
Machine learning is an application of artificial intelligence (AI) that provides systems the ability to automatically learn and improve from experience without being explicitly programmed. Machine learning focuses on the development of computer programs that can access data and use it to learn for themselves.
The process of learning begins with observations or data, such as examples, direct experience, or instruction, in order to look for patterns in data and make better decisions in the future based on the examples that we provide. The primary aim is to allow the computers to learn automatically without human intervention or assistance and adjust actions accordingly.
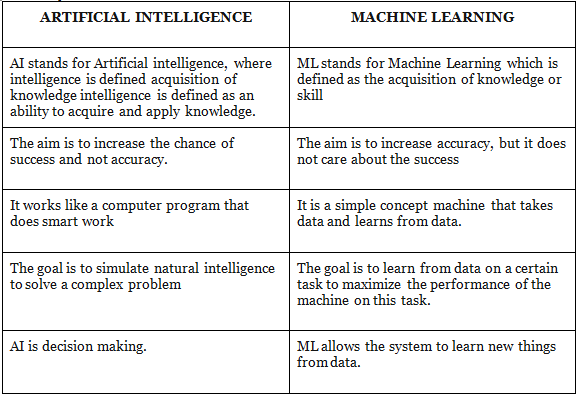
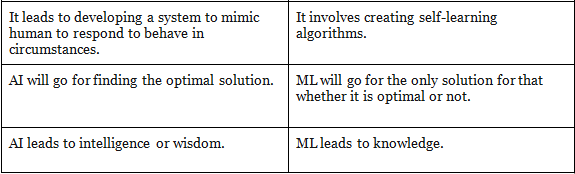
The key difference between AI and ML are:
Project Brainwave
Microsoft has launched “Project Brainwave”, a deep learning acceleration platform for real-time artificial intelligence (AI).
It uses the massive field-programmable gate array (FPGA) infrastructure.
The system architecture allows very high throughput, with the FPGA processing requests as fast as the network can stream them.
Significance: Real-time AI is becoming increasingly important as cloud infrastructures process live data streams, whether they be search queries, videos, sensor streams, or interactions with users.
Humanoid Robot
A humanoid robot is a robot with its body shape built to resemble the human body. The design may be for functional purposes, such as interacting with human tools and environments, for experimental purposes, such as the study of al locomotion, or for other purposes.
In general, humanoid robots have a torso, a head, two arms, and two legs, though some forms of humanoid robots may model only part of the body, for example, from the waist up. Some humanoid robots also have heads designed to replicate human facial features such as eyes and mouths. Androids are humanoid robots built to aesthetically resemble humans.
Features of Humanoid Robots –
- Self-maintenance
- Autonomous learning
- Avoiding harmful situations to people, the property, and itself
- Safe interacting with human beings and the environment
Humanoid Robot Sophia became the world’s first robot citizen as Saudi Arabia granted citizenship to her in a bid to promote artificial intelligence.
Sophia
Sophia is a social humanoid robot developed by Hong Kong-based company Hanson Robotics. Sophia was activated on April 19, 2015. She is able to display more than 50 facial expressions.
In November 2017, Sophia was named the United Nations Development Programme’s first-ever Innovation Champion, and the first non-human to be given any United Nations title.
Traditional Knowledge Digital Library (TKDL)
Traditional Knowledge Digital Library (TKDL) is a pioneer initiative of India to prevent misappropriation of the country’s traditional medicinal knowledge at International Patent Offices on which healthcare needs of more than 70% population and livelihood of millions of people in India is dependent. Its genesis dates back to the Indian effort on the revocation of the patent on wound healing properties of turmeric at the USPTO.
Besides, in 2005, the TKDL expert group estimated that about 2000 wrong patents concerning Indian systems of medicine were being granted every year at the international level, mainly due to the fact that India’s traditional medicinal knowledge which exists in local languages such as Sanskrit, Hindi, Arabic, Urdu, Tamil, etc. is neither accessible nor comprehensible for patent examiners at the international patent offices.
Traditional Knowledge Digital Library has overcome the language and format barrier by scientifically converting and structuring the available contents (till date 0.29 million medicinal formulations) of the ancient texts on Indian Systems of Medicines i.e. Ayurveda, Siddha, Unani, and Yoga, into five international languages, namely, English, Japanese, French, German and Spanish, with the help of information technology tools and an innovative classification system – Traditional Knowledge Resource Classification (TKRC).
TKRC has structured and classified the Indian Traditional Medicine System in approximately 25,000 subgroups for Ayurveda, Unani, Siddha, and Yoga. TKRC has enabled the incorporation of about 200 subgroups under A61K 36/00 in International Patent Classification instead of a few sub-groups earlier available on medicinal plants under A61K 35/00 thus enhancing the quality of search and examination of prior-art with respect to patent applications filed in the area of traditional knowledge.
TKDL has also been able to set international specifications and standards for setting up to TK databases based on TKDL specifications. This was adopted in 2003 by the Committee in the fifth session of the Intergovernmental Committee (IGC) of WIPO on Intellectual Property and Genetic Resources, Traditional Knowledge and Expression of folklore.
TKDL technology integrates diverse disciplines and languages such as Ayurveda, Unani, Siddha, Yoga, Sanskrit, Arabic, Urdu, Persian, Tamil, English, Japanese, Spanish, French, German, modern science & modern medicine.
Till date, TKDL is based on 359 books of Indian Systems of Medicine, which are available at a cost of approx US$ 1000, in the open domain, and can be sourced by any individual/organization at the national/international level. TKDL acts as a bridge between these books (Prior-art) and International patent examiners. It is the TKDL technology that has created a unique mechanism for a Sanskrit verse to be read in languages like German, Japanese, English, Spanish and French by an examiner at any International Patent Office on his computer screen.
At present, as per the approval of the Cabinet Committee on Economic Affairs, access of TKDL is available to nine International Patent Offices (European Patent Office, United State Patent & Trademark Office, Japan Patent Office, United Kingdom Patent Office, Canadian Intellectual Property Office, German Patent Office, Intellectual Property Australia, Indian Patent Office, and Chile Patent Office), under TKDL Access (Non-disclosure) Agreement. Negotiations are underway to conclude the Access Agreement with the Intellectual Property Office of Russia and Malaysia.
As per the terms and conditions of the Access Agreement, examiners of the patent office can utilize TKDL for search and examination purposes only and cannot reveal the contents of TKDL to any third party unless it is necessary for the purpose of citation. TKDL Access Agreement is unique in nature and has in-built safeguards on Nondisclosure to protect India’s interest against any possible misuse.
In addition, pre-grant oppositions are being filed at various International Patent Offices, along with prior-art evidence from TKDL. A significant impact has already been realized. So far about 200 patent applications of the pharmaceutical companies of the United States, Great Britain, Spain, Italy, China, etc. have either been set aside/ withdrawn/ amended, based on the Prior art evidences present in the TKDL database without any cost and in few weeks/months of time, whereas APEDA had to spend about seven crores towards legal fee only for getting few claims of Basmati rice patent revoked. A similar outcome is expected in about 1200 more cases, where TKDL has filed pre-grant opposition.
TKDL is proving to be an effective deterrent against bio-piracy and is being recognized as a global leader in the area of traditional knowledge protection. In 2011, an International Conference was organized by the World Intellectual Property Organization (WIPO) in collaboration with CSIR on ‘Utilization of Traditional Knowledge Digital Library as a Model for Protection of Traditional Knowledge’, at New Delhi. Pursuant to this, WIPO in collaboration with CSIR and DIPP (Ministry of Commerce and Industry) organized an ‘International Study Visit To TKDL’ for 19 countries interested in the replication of TKDL.
TKDL has made waves around the world, particularly in TK-rich countries by demonstrating the advantages of proactive action and the power of strong deterrence. The idea is not to restrict the use of traditional knowledge, but to ensure that wrong patents are not granted due to lack of access to the prior art for Patent examiners.
For entering into TKDL Access Agreement by a Patent Office, Head, CSIR Traditional Knowledge Digital Library Unit may be contacted.
Digiceuticals
What if an app could replace a pill? That’s the big question behind an emerging trend known as “digital therapeutics.” The idea: software that can improve a person’s health as much as a drug can, but without the same cost and side-effects.
Digital therapeutics, or “digiceuticals,” as some call them, have become a Holy Grail in some quarters of Silicon Valley, where investors see the chance to deliver medicine through your smartphone.
Some digiceuticals will work better alongside conventional drugs, rather than on their own– opening up possibilities for alliances between tech and pharma firms. Voluntis, a startup, develops companion software for specific medications or medical devices. These programs can monitor side-effects, help manage symptoms and connect patients with doctors and nurses.
CIMON (Crew Interactive Mobile Companion)
- It is a 3D-printed artificial intelligence system, described by its creators as a “flying brain”.
- It is made up of plastic and metal, created using 3D printing
- It is being developed by Airbus; an aeronautics company based in the Netherlands
- It will be the first AI-based mission and flight assistance system
- It will join the crew aboard the International Space Station (ISS) to assist astronauts.
- It is designed to support astronauts in performing routine work.
Cryptojacking
- Cryptojacking is defined as the secret use of your computing device to mine cryptocurrency.
- Cryptojacking used to be confined to the victim unknowingly installing a program that secretly mines cryptocurrency
- Attackers employ malware to force an entry into the computers of remote users and then using their hardware to mine for coins.
- This form of distributed computing can be profitable since it eliminates the cost burden of owning a mining rig with hundreds of processors.
- Cryptojackers usually target popular websites that draw audiences numbering in the millions every day.
Haptic Communication
Haptic communication is a technology that transmits the sensation of touch over the Internet, had been developed by engineers in the Virtual Reality Laboratories at the University at Buffalo (UB).
The breakthrough leads to the creation of haptic technologies that convey the sense of touch and taught users how to master skills and activities — such as surgery, sculpture, playing the drums or even golf – that require the precise application of ‘touch’ and movement.
Digi Shala
Digi Shala, a free Doordarshan DTH channel is launched to educate and inform people about the various modes of digital payments. DigiShala will be available through GSAT15 (DD Direct DTH), 93.5 degree East, Receive frequency: 11590 Mhz
The channel will help people understand the use of a unified payments interface (UPI), USSD, aadhar-enabled payments system, electronic wallets, debit, and credit cards.
A website was also launched which will serve as a repository of knowledge regarding digital payments.
Both the channel and website were launched as a part of the ‘Digi Dhan Abhiyan’, a campaign conceptualized by the IT ministry to enable every citizen, small trader and merchant to adopt digital payments in their everyday financial transactions.
Significance:
- DigiShala will enable and empower every citizen of the country, especially farmers, students, Dalits and women in rural areas to learn the usefulness and benefits of digital payment in our everyday life to adopt the same on a mass scale.
- The provision of digital literacy to the semi-urban and rural sectors of the economy has become the major focus area for the government.
Computer Firewall
A firewall is a system designed to prevent unauthorized access to or from a private network. You can implement a firewall in either hardware or software form, or a combination of both. Firewalls prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets.
All messages entering or leaving the intranet (i.e., the local network to which you are connected) must pass through the firewall, which examines each message and blocks those that do not meet the specified security criteria.
In protecting private information, a firewall is considered a first line of defense; it cannot, however, be considered the only such line. Firewalls are generally designed to protect network traffic and connections, and therefore do not attempt to authenticate individual users when determining who can access a particular computer or network.
Cyber-Attacks
Cyber-attacks involve the unauthorized access of private or confidential information contained on computer systems or networks, but the techniques and methods used by the attacker further distinguish whether the attack is an active cyber-attack, a passive type attack, or some combination of the two.
According to Symantec, both active and passive cyber-attack types are defined by unique characteristics and techniques, and each type of attack presents unique challenges to victims, system users, system administrators, and cybersecurity professionals.
Knowing the difference between passive and active cyber-attacks can help system users and administrators identify when an attack is taking place so that action can be taken to try and contain the attack.
Active Cyber Attacks
Active cyber-attacks are often aggressive, blatant attacks that victims immediately become aware of when they occur. Active attacks are highly malicious in nature, often locking out users, destroying memory or files, or forcefully gaining access to a targeted system or network. Viruses, worms, malware, Denial of Service attacks, and password crackers are all examples of active cyber-attacks. Usually, hackers that use active attacks are not much concerned with their activities being detected because by the time the attack is detected the damage is already done or is underway.
Passive Cyber Attacks
Passive cyber-attacks often employ non-disruptive and covert methods so that the hacker does not draw attention to the attack. The purpose of the passive attack is to gain access to the computer system or network and to collect data without detection. Many data security breaches involving the exposure of credit card and debit card payment information are the result of passive attacks, as are data breaches where the targeted data collected during the attack is user name, passwords, and other personal identifying information.
Passive attacks are usually data-gathering operations, which means they usually employ some sort of malware or hack that eavesdrops on system communications (i.e., scrubs email for personal identifying information) or records system communications (i.e., keystroke recording malware). Information that is gathered in a passive cyber-attack is usually sold on the black market and dark web for the financial the gain of whoever perpetrated the passive attack.
Digital Signature Certificate (DSC)
A Digital Signature Certificate (DSC) is a secure digital key that certifies the identity of the holder, issued by a Certifying Authority (CA). It typically contains your identity (name, email, country, APNIC account name, and your public key).
- Digital Certificates use Public Key Infrastructure meaning data that has been digitally signed or encrypted by a private key and can only be decrypted by its corresponding public key. A digital certificate is an electronic “credit card” that establishes your credentials when doing business or other transactions on the Web.
- Digital Signatures are legally admissible in a Court of Law, as provided under the provisions of IT Act, 2000.
Open-source software (OSS)
Open-source software (OSS) is computer software with its source code made available with a license in which the copyright holder provides the rights to study, change, and distribute the software to anyone and for any purpose. Open-source software may be developed in a collaborative public manner.
- The main occurrence of open-source sharing goes back to even before the primary PC was created. In 1911, progressive automaker Henry Ford was instrumental in propelling the Motor Vehicle Manufacturers Association. This affiliation propelled an open-source activity that saw real US vehicle makers sharing innovation licenses straightforwardly without looking for any money related advantages consequently.
Software-defined Radio
- Software-defined radio (SDR) is a radio communication system where components that have been traditionally implemented in hardware (e.g. mixers, filters, amplifiers, modulators/demodulators, detectors, etc.) are instead implemented by means of software on a personal computer or embedded system.
- A basic SDR system may consist of a personal computer running SDR software that interfaces with analog-to-digital converter over USB or ethernet, preceded by some form of RF front end with RF amplifiers, filters, and attenuators.
LIDAR-(Light Detection and Ranging)
- LIDAR, which stands for Light Detection and Ranging, is a remote sensing method that uses light in the form of a pulsed laser to measure ranges (variable distances) to the Earth.
- A LIDAR instrument principally consists of a laser, a scanner, and a specialized GPS receiver. Airplanes and helicopters are the most commonly used platforms for acquiring LIDAR data over broad areas.
- Two types of LIDAR are topographic and bathymetric.
- Topographic LIDAR typically uses a near-infrared laser to map the land, while bathymetric lidar uses water-penetrating green light to also measure seafloor and riverbed elevations.
|
114 videos|429 docs|209 tests
|
FAQs on Awareness in Field of IT & Computers- 2 - Science & Technology for UPSC CSE
| 1. What is the importance of awareness in the field of IT and computers? |  |
| 2. How can one increase their awareness in the field of IT and computers? |  |
| 3. What are the potential benefits of being aware in the field of IT and computers? |  |
| 4. How does awareness in IT and computers contribute to cybersecurity? |  |
| 5. How can awareness in IT and computers lead to innovation and problem-solving? |  |

















